Today we are going to solve another boot2root challenge called "Relevant: 1". It's available at VulnHub for penetration testing and you can download it from here.
The merit of making this lab is due to
@iamv1nc3nt.
Let's start and learn how to break it down successfully.
Level: Intermediate
Penetration Testing Methodology
Reconnaissance
§
Netdiscover
§
Nmap
Enumeration
§
Dirsearch
§
Nmap with scripts WordPress
Exploiting
- Wp-file-manager 6.7
Remote Code Execution (RCE)
Privilege
Escalation
§
Abuse of credentials
with weak hashes in hidden files
§
Abuse of sudo
§ Capture the flag
Walkthrough
Reconnaissance
We are looking for the
machine with netdiscover
$ netdiscover -i ethX
So,
we put the IP address in our "/etc/hosts"
file and start by running the map of all the ports with operating system
detection, software versions, scripts and traceroute.
$
nmap -A –p- 192.168.10.161
Enumeration
So
far it seems all easy, a web service with some links containing credential
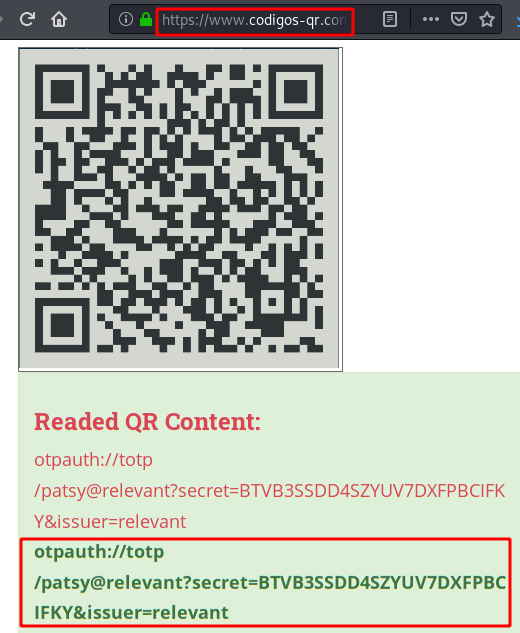
information in leaks and a QR code to set up a double authentication factor
(2FA) . Too beautiful to be true!
Listing of credentials in public leaks.
Content of
the QR code:
We log in via SSH,
insert the password, insert the double authentication factor and disconnect!
The account has disabled the use of this service, so it is a rabbit hole.
It's time to launch my favorite fuzzing tool, in my case I
used dirsearch. We list that there
are WordPress files and directories
displayed on the machine.
Going back to the clue given by the creator of the machine in
the description: "enumerate the box,
then enumerate the box differently".
Since our only evidence is the remains of WordPress files, we will try with the nmaps
scripts for this CMS.
It will list two plugins, among them "wp-file-manager 6.7".
Exploiting
I After the above list, we look for exploits and
vulnerabilities that we can exploit for this version. We found an exploit that
allows remote code execution without
the need for authentication.
Exploit: https://github.com/w4fz5uck5/wp-file-manager-0day
Execute the exploit and access the server.
Since visibility is a bit of a problem, we upload a "pentestmonkey" webshell, put a
netcat on it and run our webshell.
We execute our two favorite commands to get an interactive
shell.
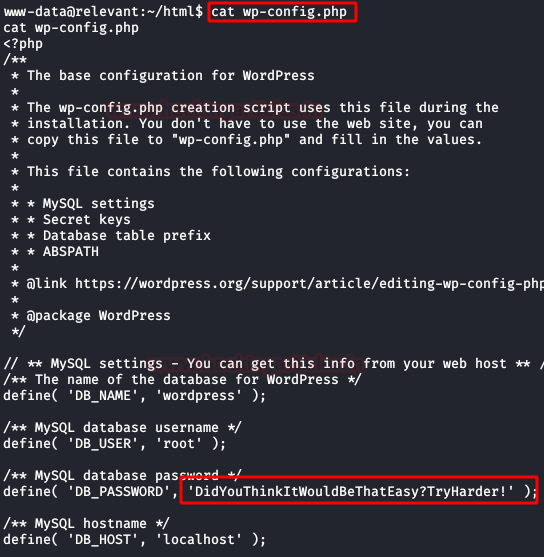
We read the file "wp-config.php",
but something tells me that the password is not going to help us much either.
xD
We checked the files of the user "h4x0r" and found a "hidden"
folder with three dots, in it there is a file called "note.txt" with some credentials in SHA-1 that we must crack.
We access the online site
"hashes.com" and insert our hash and get the password in plain text.
Privilege
Escalation (root)
Now yes, we authenticate
with the user "news", we
execute "sudo -l" and we
see that we have permissions to execute the binary "node”.
We
take advantage of this to scale privileges in the system as root, for this we
will execute the following syntax.
And
finally, we will read our deserved flag!
Author: David Utón is Penetration Tester and security auditor for Web
applications, perimeter networks, internal and industrial corporate
infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.























0 comments:
Post a Comment