This article will showcase various attacks and tasks that can be performed on a compromised Windows Machine which is a part of a Domain Controller through Metasploit inbuilt Mimikatz Module which is also known as kiwi. We covered various forms of Credential Dumping with Mimikatz in our Series but we didn’t present a consolidated guide to use Mimikatz with Metasploit. Also, after the response from the PowerShell Empire for Pentester: Mimikatz Module, We were encouraged to create this resource.
Table of Content
·
Introduction
·
Local Security Authority (LSA|LSASS.EXE)
·
LSA Secrets
·
Changing Password of a User
·
DC Sync Attack
·
Golden Tickets
·
Purging Tickets
·
Extract Credentials from Security Packages
o
MSV
o
Kerberos
o
SSP
o
WDigest
o
All
·
Mimikatz Commands
·
Extract Wi-Fi Credentials
·
Conclusion
Introduction
To begin with the demonstration, we first need to compromise
a Windows Machine that is a part of a Network governed by a Domain Controller.
The choice of compromise is your own. After the initial compromise through
Metasploit, we get a meterpreter shell. There are a bunch of inbuilt commands
that are loaded inside the meterpreter shell if some commands or a set of
commands are not loaded then they can be loaded in the form of a module.
Mimikatz is also a module that needs to be loaded inside the meterpreter shell.
After loading the module, you can hit the help command to see a list of
different options and attacks that can be performed on the target machine
through this meterpreter shell.
load kiwi
help kiwi
Local Security Authority (LSA|LSASS.EXE)
The lsa_dump_sam moduel gets the SysKey to decrypt SAM
entries (from registry or hive). It connects to the local Security Account
Manager (SAM) database and dumps credentials for local accounts. As we known
that LSA is a system process that authenticates and logs users on the system. LSA
authenticates the Domain Credentials that are used by the Operating System. The
user information is validated by LSA by accessing the SAM of each computer. If
there is a code that is running inside the LSA process than that process is
able to access the credentials. LSA is able to store Reversibly encrypted
plaintext, Kerberos tickets (ticket-granting tickets (TGTs), service tickets),
NT hash, LAN Manager (LM) has. Here we can see that NTLM hash is extracted of
the raj user.
lsa_dump_sam
Learn More: Credential
Dumping: Local Security Authority (LSA|LSASS.EXE)
LSA Secrets
LSA secrets, Let’s understand what is the secret behind
this? Earlier it was designed to store the cached domain records. After a while
Microsoft expanded its usage to store passwords, IE passwords, SQL Passwords,
RAS Passwords and CISCO passwords and much more. A slice of the secrets can be
seen in the screenshot below. This is quite less information than it was
promised as this is a Local Lab Environment. Real Working Domain Controllers
have much more data.
lsa_dump_secrets
Changing Password of a User
The ability to change the password for a user can be not
only a high-risk situation but also can be a tad bit annoying. The
password_change module can help you do just that. There is an option to change
the password if the old password is known. It generates and stores a NTLM hash
for the new user. The other option is if you are able to extract the NTLM hash
of a user, say using the lsadump then you have the ability to change the
password for that user.
password_change -u
raj -p 123 -P 9876
password_change -u raj -n <NTLM-hash> -P 1234
DC Sync Attack
As discussed earlier, the DC Sync attack allows an attacker
to replicate Domain Controller (DC) behavior. In simple words it impersonates
as a domain controller and request other DC’s for user credential data via
GetNCChanges. The only barrier is that you need a compromised machine and its
user who is a member of the privilege account (Administrators, Domain Admin or
Enterprise Admin).
dcsync_ntlm krbtgt
dcsync krbtgt
Learn More: Credential
Dumping: DCSync Attack
Golden Tickets
Golden Tickets is an attack that forges the Kerberos Ticket
Granting Tickets (TGT) which in turn is used to authenticate users with the
help of Kerberos. The Ticket Granting Services (TGS) is depended upon the TGTs
to verify the authenticity of tickets. This means that the forged ticket can be
used to be directly authenticate the attacker. These tickets can have a life
span up to a decade. That makes them so valuable almost as gold.
golden_ticket_create -d ignite.local -u pavan -s
<SID> -k
kerberos_ticket_use /root/ticket.kirbi
shell
dir\\DC1.ignite.local\c$
Learn More: Domain
Persistence: Golden Ticket Attack
Purging Tickets
While working with the tokens and tickets, there will be a
time where the number of tickets would be too large to work with. This scenario
will arise sooner or later and that’s when the purge command will help you. It
will purge all the tickets in the current session.
kerberos _ticket_list
kerberos_ticket_purge
kerberos_ticket_list
Extract Credentials from Security Packages
MSV
Microsoft provides the MSV1_0 authentication package for
local machine logons that do not require custom authentication. The Local
Security Authority (LSA) calls the MSV1_0 authentication package to process
logon data collected by the GINA for the Winlogon logon process. The MSV1_0
package checks the local security accounts manager (SAM) database to determine
whether the logon data belongs to a valid security principal and then returns
the result of the logon attempt to the LSA. MSV1_0 also supports domain logons.
MSV1_0 processes domain logons using pass-through authentication We can extract
the hash using the creds_msv command on meterpreter as shown in the image.
creds_msv
Kerberos
Similarly, if we want to extract the credentials from the
Kerberos Service, we can run the creds_kerberos to attack the Kerberos. This
however have the ability to extract clear text passwords for the users.
creds_kerberos
SSP
SSP or Securtiy Support Provider is dynamic-link library
(DLL) that implements the SSPI by making one or more security packages
available to applications. Each security package provides mappings between an
application's SSPI function calls and an actual security model’s function.
Security packages support security protocols such as Kerberos authentication
and the Microsoft LAN Manager. Due to the connection of the SSP with the
Kerberos, it can extract credentials in clear text as shown in the image below.
creds_ssp
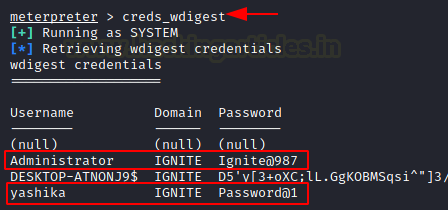
WDigest
WDigest.dll was introduced in the Windows XP operating system
The Digest Authentication protocol is designed for use with Hypertext Transfer
Protocol (HTTP) and Simple Authentication Security Layer (SASL) exchanges.
These exchanges require that parties that seek to authenticate must demonstrate
their knowledge of secret keys. This process improves upon earlier versions of
HTTP authentication, in which users provide passwords that are not encrypted
when they are sent to a server, leaving them vulnerable to capture by attackers
by using the creds_wdigest.
creds_wdigest
All
Incase, you want to extract all the possible hashes or
credentials from all the security packages on the target machine, then use
creds_all command on the meterpreter. It will show all the credentials from the
packages that we just discussed in one go.
creds_all
Learn More: Credential
Dumping: SAM
Mimikatz Commands
There are modules inside the Mimikatz that don’t have the
direct access in the form of commands in kiwi. This is where the ability to run
the Mimikatz commands comes to the rescue. This acts as a normal shell with the
ability to run the Mimikatz commands and perform almost all the attacks
possible in the scenario.
kiwi_cmd hostname
Extract Wi-Fi Credentials
Among the attacks that duplicate that tickets to provide the
ability to run the commands as domain controller, the ability to read the Wi-Fi
credentials seems a bit dim but the this is not the case. The Wi-Fi passwords
are not the most thought-out passwords. It usually the first things that comes
into the user’s mind. This provides insight as to how that particular user will
create passwords. There is a good chance that the account of that user will
have the same passwords. Even if it turned out to be that case, you get free
Wi-Fi access and that’s not bad.
wifi_list
Conclusion
After Credential Dumping Series which contained different
tools that can be used against a specific vulnerability and PowerShell Empire
for Pentester: Mimikatz Module which provided an insight on the ability of
PowerShell Empire to attack the Windows Authentication Process. We felt the
need for a guide that can help a person who is trying to get the reins of
Metasploit.























0 comments:
Post a Comment