In the previous article, we have discussed about the reverse engineering of original DVTA application in the Lab setup of Thick Client: DVTA part 2
In this part, we are going to
systematically pentesting the DVTA application for various issues.
Table
of content
·
Prerequisites
·
Information Gathering by using
CFF Explorer
·
Information Gathering by using
Sysinternal Suite
·
Information Gathering by using
Procmon
·
Information Gathering by using
Wireshark
Prerequisites
·
CFF explorer
·
Sysinternals Suite
·
Wireshark
Information
gathering by using CFF Explorer
You can directly install CFF Explorer
from here: - https://ntcore.com/files/ExplorerSuite.exe
CFF Explorer was designed to
make PE editing as easy as possible, but without losing sight on the portable
executable's internal structure. This application includes a series of tools
which might help not only reverse engineers but also programmers.
Let’s open up the CFF explorer. Basically,
CFF explorer is used to check how the binary is built. Having knowledge on what
languages are used for building the binary is really useful because if it is
built using Java, C, C++, ML, Al… we can look for vulnerabilities like Buffer
overflow if it is built using C-sharp.net kind of languages it is very easy to
decompile the application and reverse engineered
So, without wasting of much time quickly
open up the DVTA.exe by navigating to File > open > DVTA.exe as
shown in below image.
Let’s see which type of juicy
information we get …
So if you notice by 2nd line
this is a Portable Executable 32.NET Assembly and Microsoft Visual .NET is used
to build this. So, as you can see this binary is built using Microsoft Visual
Studio .NET and it’s a .NET assembly so that we can de-compile this application
very easily.
This information is enough to decompile
the application easily.
Information
Gathering by using Sysinternals Suite
Download and install Sysinternal Suite: https://download.sysinternals.com/files/SysinternalsSuite.zip
Once the download complete, install it.
Installation is pretty much easy there are no need to do changes in
installation just simply press next and next until installation doesn’t
finishes.
Let’s begin with a tool TCP View from
the Sysinterals Suite
Open up the application TCP view and
just after opening the application you can see the machine is making network
communications and what we’re interested in is DVTA application.
So, the thing is we have to gather
information like where these applications communicating such as the Destination
IP address.
To do this launch the modified DVTA
application and see what happens… 🤔
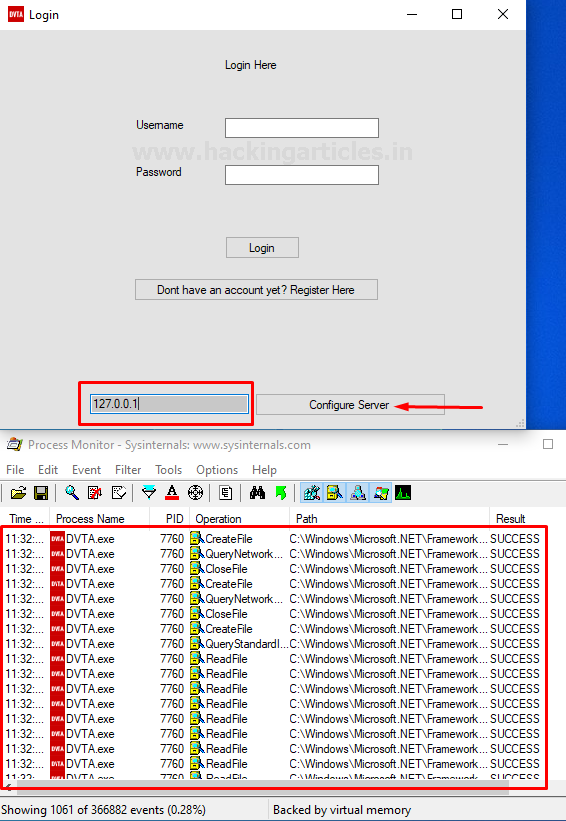
First of all configure the server to
your local Ip address or the loop back address and the login to the DVTA
application with the user credentials.
Now, you can see there is a new entry in
TCP view showing DVTA.exe processes and the local address is 127.0.0.1 and the
remote address that is communicating with localhost in this case because it’s
the loop back address where the database is installed.
In this way we can figure out the IP
addresses that our applications are communicating with. So, we have completed
first step towards the information gathering.
Let’s move to another tool from the
Sysinternals Suite called Procmon.
Procmon
Basically, Procmon is a process monitor
that helps us to understand the file system changes and what is being accessed
on the file system.
Let’s open up the application Procmon
which you can find in the folder of Sysinternals suite.
Here we’re using 32-bit of version.
Just after opening of Procmon
application you can see this process monitor is showing lot’s of traffic and
the reason behind of that is it picks up all of the process and shows output of
all the processes In its window.
This becomes complex for us to understand
the process that we’re interested in. To reduce that complexity lets setup a
filter by navigating to Filter > Filter or just simply press Ctrl+L
Select the Attribute to Process Name is DVTA.exe because this is the only process that what we’re interested in and ADD the filter.
Now you are going to see the screen
empty because DVTA is not currently running.
So, without wasting of time go back to
modified DVTA application folder and run the DVTA.exe
Now just by opening of DVTA there is
traffic generated only for the DVTA.exe file.
So now its become more interesting and
easier to understand.
Now configure our server to 127.0.0.1.
we have configured the server already in previous articles we’re doing this
again to understand what changes are being made in the file system when we
configure it.
But before doing this clear your screen
to reduce the complexity by navigating to Edit > Clear Display so
that when we press configure server button, we can only see which changes being
made.
Just after hitting the Configure server
button you can see there is instantly lots of traffic generated as shown below
In the image.
Now what we interested in we want to
understand what happen when we clicked on configure server button. So just
scroll down to the output and see what we can find anything interesting.
There are lots of registry entry being
accessed and at bottom there are some files that are being accessed such as
create file, Query Network open information file, Close File …
so, it looks like these files is
something which is being accessed by DVTA.exe when we try configuring the IP
address. So quickly open it up and see what it has. We can directly jump from
process monitor to the location of this file by giving it a right click and
then navigate to Jump TO…
It will redirect you the location of
that file were changes in file system are being made as shown below also it
automatically highlights to the file where changes are being implied.
Now let’s open up the DVTA.exe xml
configuration file in you favourite XML viewer.
It’s gonna very interesting as you can
see the server is configured to configured to 127.0.0.1 exactly the same
IP address that we have entered earlier and looks when we click on configure
server the Ip address is taken from the text box and placed here… 🤔
Apart from these entries here we have
some other interesting entries if you notice there is a database name which is DVTA
… if you remember this is the name of the database we have used when creating a
database in SQL Server Express. Also there is the user name and the password
for the database but it seems like password is Encrypted but if you observe
just right below that there is an AES encryption key possibly used for
decrypting the Encrypted value and apart from that there is IV value which
is probably used with the AES Encryption.
Now the main thing to be noted is
that when we tried configuring the server in the application… the application
is accessing this DVTA.exe.config file and it is trying to place the IP address
place there then we have also noticed some more interesting information such as
Encrypted Database password and the AES key.
Let’s open up the DVTA application and
login to the application by using user credentials as shown below and on the
other tab process monitor start capturing the traffic.
As you can see, we have successfully
logged in to the application also you can verify the user credentials by
navigating to View profile. Now close the tab directly without doing Logout.
Now again open the DVTA application and
if you noticed it doesn’t ask to enter the credentials again. That means it is
storing the credentials somewhere or it may be storing the session somewhere in
the client. So, what we will try to do is we will close the application and
clear the procmon display once again so that we’ll have to deal with less
number of entries and once again we’ll open DVTA.exe and we already notices we
didn’t Logout so it will directly bring you to main screen
Now, let’s see if there is anything
interesting happening on the file system when we trying to open this
application with the existing session. So, keep scrolling down to the output
screen until we don’t find something interesting and if you see there is a registry
specific to our application name DVTA and inside that there seems to be some
keys like username, is Logged in… etc
So, it seems like interesting let’s
quickly open up the registry entry by giving it a right click and navigating
to Jump to or you can directly jump to file by pressing ctrl+J.
It will open up the Registry entry. As
we can see it has couple of keys like Email, Is Logged in, Password, and
Username. So basically, this application is storing the credentials here
and it is also checking if the user is already logged in or not.
And that means if you change the
isLoggedIn value true to false then it will probably ask you to enter the login
credentials again even if you are already logged in.
Hmm… exited Let’s do it.
Let’s check that by closing the DVTA
application and opening it once again.
When you open the DVTA application again
it will ask you to enter the login credentials again so that means our
acknowledges are correct. If the application finds this registry entry with the
value true it will not ask you for log in.
So, this can be used for some
interesting attacks for example if we change the user name and password In the
registry entry we can easily trick to the application to believe that the
particular user is already logged in with his credentials.
This looks very interesting attack …
isn’t it…?? Let’s do it
Change the Password value to vijay to
paras or your on own as by giving a double click to the registry of Password as
shown below.
Same again change the username value
vijay to paras or your own name and hit ok
Let’s check what happen if we once again
open the DVTA application.
As you can see, we directly logged in to
the application without entering the login credentials.So, as we see we can
simply trick the application to logged in to application directly by doing
changes in registry entry.
Now what we learnt from all of these
process that the application is storing log in credentials in registry entry.
Information
gathering by using Wireshark
You can download Wireshark by visiting the
official page of Wireshark: - https://www.wireshark.org/download.html
After downloading the Wireshark install
it on your system by hitting next and next it doesn’t need any changes in the
installation. By installing it run the Wireshark and the interface looks
similar like as shown in below image.
Since we are using loopback address
let’s choose loopback traffic capture
Now go back to the modified DVTA
application and login to the application by using login credentials.
Just after login to application come
back to the Wireshark and you can see there are lots of traffic going there just refresh the capture and again
login to the DVTA application and just after hitting the login button come back
to Wireshark and its better to stop the capture immediately after clicking the
login button so it won’t capture unnecessary traffic as shown below in image
where I opened two different tabs one of Wireshark and another one is DVTA
application just to see how it capture the traffic when I press the login
button.
Now what we’re interested in is to
understand how this login is making communication with the server. If you look
there are some packets that uses UDP protocol so let’s open it in UDP stream
and then let’s see what we can find.
When you open that packet, you can see
this is a packet containing a request to SQL server. You can see there is an
SQL Express and the host name where the SQL server is running.
So, this packet shows that we are making
a network connection with the SQL server and this is enough also you can
capture the whole traffic of DVTA application how the application is
communicating with the server.
Now the key takeaway here is that the
application is making some SQL connections when you are trying to interact with
it.
In the next part we will talk different
attack vectors.











































0 comments:
Post a Comment