Whether it's guessing up a login credential or opting a valid payload for a specific vulnerability, both of these things are time-consuming and require a number of permutation and combination to built up a dictionary for them, if done manually. But what, if all these things are done with some simple click and you just need to sit and analyze the outcome it drops out?
Today in this article, we’ll learn the most common
technique i.e. “fuzzing” that has been used since decays in order to
deface a web-application, by exploiting some vulnerabilities over at the
web-application with a list of pre-defined payloads that are offered by the
burpsuite’s intruder tab.
Table Of
Content
·
Introduction
to Fuzzing
o
What
is Fuzzing?
o
How
Burpsuite works as a Fuzzer?
·
Fuzz
with Burp’s built-in Payload lists.
o
Fuzzing
for Login credentials.
o
Fuzzing
for SQL Injection
o
Fuzzing
to find Hidden Files
o
Fuzz
to find Restricted File Upload Extensions
Introduction
to Fuzzing
What is Fuzzing?
Fuzzing or Fuzz Testing plays a vital role in software testing procedures. It is a technique which is
used for find bugs, errors, faults, and loophole by injecting a set of
partially – arbitrary inputs called fuzz into the
program of the application which is to be tested. A Fuzzer takes structure inputs
in a file format to differentiate between valid and invalid inputs.
However, the Fuzzer tools
are best in identifying vulnerability like SQL injection, buffer overflow, Cross-Site
Scripting, OS command injection and many more.
How Burp Suite work as a Fuzzer?
Burp Suite comes with an integrated HTML Fuzzer,
commonly termed as a Burp Intruder. This burp intruder gives us several
opportunities to fuzz the injection points in the most customizable way we can.
In order
to make a fuzzing attack possible, we need to add up a dictionary as a payload
list. However, Burp Suite’s Professional Edition gives us an option to opt the
predefined lists containing the most
common fuzz strings according
to the attack types.
You might be wondering about how the fuzzing works
here, right??
Let’s
clear it in some simple steps.
·
First,
we need to intercept the HTTP Request, therewith that we’ll thus share
it with the Intruder.
·
As
soon as we do so, we’ll define the parameters or the injection points
where the fuzzing needs to be done.
·
Now,
at last, the attack type and payloads list need to be defined up
with that.
And as soon as we launch the fuzzing attack by hitting the “Attack” button, we’ll get the output screen stating up all the possible hits and drop. Therewith it, we can thus analyse them and find a crucial hit.
Fuzz with
the Burp’s built-in Payload Lists
Up till
now, you might be clear about what fuzzing is, and how the Burp Suite’s
Intruder helps us to fuzz a web application. So let’s take a deep dive and
intercept some request in order to fuzz an application with the burp’s
predefined payload lists.
Fuzzing for Login Credentials :
Usernames and Passwords plays a major role within an application, thereby if we could fuzz them in the best way, we would be able to bypass the authentication phase. So let’s do it.
The Password field –
Turn
ON the burp suite in order to intercept the request and then share the same
to the Intruder.
Now, configure
the Position where the payload needs to injected by hitting the Add button.
And even manipulate the Attack Type which determines how the payload will
hit at the injection point (payload position).
Payload
position: 12345 (User
input as the password)
Attack
type: Sniper (for one
payload)
Choose the payload option to
configure a Simple list of payload for the attack.
Burp suite Intruder contains
fuzzing strings for testing a common Password, therefore let’s opt the Password option there.
Hit the “Attack”
button and initiate the attack.
As soon as we do so, our
burpsuite will start the attack by sending requests to hit the correct password
for the respective username.
Now from a given list of
applied strings, double click on the length section to sort them in the
ascending order. Further, select the one which has the lowest length.
Cool !! From the below image,
you can see that with the payload “zombie” we’re are getting a 302
success.
Let’s
check the response it made, use bee : zombie over the login field. And
there we go, we’ll are inside the application.
There
are times, when the password that the user configured is not in the Password
Payload list, therefore in such cases, we can use the other Burpsuite’s
predefined list i.e. “Short Words”
Let’s
capture the HTTP Request for the user Raj, and then, in the same way,
we’ll share it to the intruder tab.
Over
there, we’ll set the Payload position again i.e. 123 by hitting the Add
button.
Now, for
this time, rather than the Password option, we’ll opt the Short words payload
list.
Time to
go. Fire up the Add button and analyse the output response.
As soon as
we sort the length option as in the ascending order, we’ll get our
password as “movie”
The Username field –
There
are times, that we encounter such situations when there is a common password
but we don’t know how many users are having the same, and if they are, then
what are their usernames.
Therefore,
in order to solve this dilemma, burpsuite offers one more great payload list
that contains all the common usernames. let’s try to use that too.
Back into
burpsuite and capture the login request, and share it with the intruder.
Further set the injection point to “random”.
Note –
Here we
are guessing all the possible users with their password as “admin”.
Now, after
setting the payload position, its time to enroll for the payload type. Opt the Usernames
payload list from the Add from list… option.
Hit the “Attack”
button, and there we go. Great !! we got “ADMIN” and “admin” as the
usernames for the most common password admin !!
Fuzzing for SQL Injection
SQL
Injection is one of the most crucial vulnerability one could find for. However,
this vulnerability encountered majorly at the user-input fields. To
learn more about SQL Injection, click here.
Burp Suite
offers a separate Payload list for SQL Injection fuzzing, but the common
fuzzing lists the quick and the full also contributes some payloads for
SQL Injection, OS Command Injection, Cross-Site Scripting and many more. Therefore
for this time, we’ll be using the Fuzzing – full list in order to bypass
the login portal.
Over with
the similar way, let’s capture the ongoing HTTP Request of the test.vulnweb
login portal, and share it with the Intruder.
Time to
set the positions and the attack type. Here, I’ve added both the positions
i.e. uname and pass for fuzzing. Along with it, I’ve opted Cluster Bomb
this time as we’re having two payload positions.
With all
this, let’s select the Fuzzing – full list for payload position 1
in order to find the SQL vulnerability within the application.
For position
2 select the same.
Cool !!
From the below screenshot, you can see that we got some successful responses
as when we alter the length section in the descending order.
Let’s now
check the first captured response in the login fields as username = ‘--
and password = ‘
Wonderful
!! From the below screenshot, you can see that we’ve successfully bypassed the
Login credentials.
Fuzzing to find Hidden Files
There
are many web pages that are hidden for the common users but they exist over on
a web-application. However, it is quite difficult to determine that, which
webpage is giving a 200 Success, 302 Redirection or a 404 Not
Found.
Thus, in order
to make our work easy, burpsuite drop out with some amazing payload lists which
contains almost a number of commonly used webpages that are somewhere hidden
inside the webpage.
Back with
the bWAPP web-application dashboard, let’s capture an HTTP Request,
and therewith it, we’ll again share it with the intruder.
Configuring
the payload position to “portal” and the attack type to
“Sniper”.
Now, let’s
opt the Payload list, and for this time we’ll choose it to “Filename –
short”. Further, we’ll hit the “Attack” button to proceed.
From the
below image, we can see that there are a number of files that are unknown to
us, let’s check this secret one.
As soon as
we manipulate portal.php with secret.php, we’ll thus land up to
an unexpected page that says “Your secret: Any Bug?”
These
were the most common filenames that are largely available at web-applications,
but what about the unique ones? The Filenames – long gives us the possibility to hunt them too.
Now,
rather than the Filenames – short, let’s opt the Filenames - long
in the Payload Options.
As soon as
we hit the Attack button, the fuzzing get’s started up and thus within a
few minutes we’re presented with the redirecting web pages.
Let’s manipulate
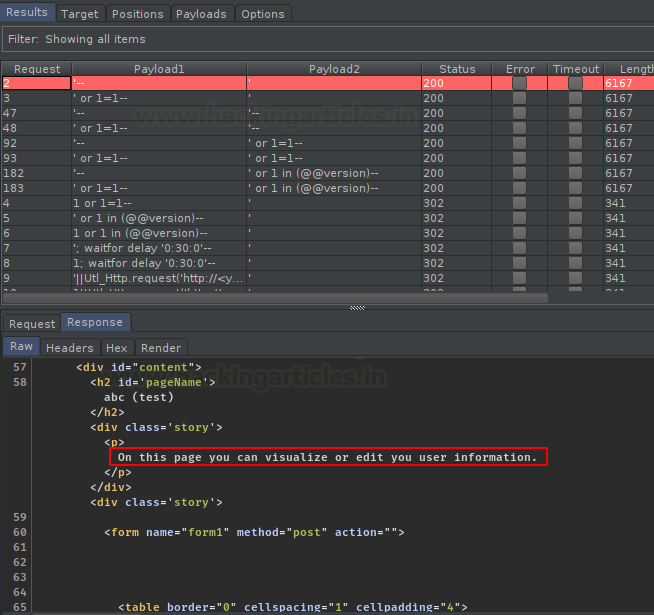
portal.php with captcha.php and let’s check what it offers to us.
Fuzz to find Restricted File Upload Extensions
File upload vulnerability is
one of the major problems within web-based applications. Here the attacker uploads a file with some malicious codes within it, which
thus could be executed on the server directly.
You can learn more about file upload vulnerability from here.
There are times when the
web-developers blocks up some certain file extensions in order to make their
web-applications secure. However, ensuring which extension is blocked by the
developer is quite impossible to find out.
But, we can do this task in one
of the most simplest way i.e. by fuzzing. Burp’s Intruder is having a
payload list in-built for this thing too, let’s use it this time.
Initially, over at the file
upload option, select a specific file.
Capture the request in a similar way that we did earlier, and share it to the
intruder.
Now, let’s setup Paylaod
positions, here we’ll do it with the file extension we’re having.
At last, we’re now at our favorite section, i.e. opting the built-in payload list. Choose the Extensions – short and hit the “Attack” button in order to initiate the fuzzing.
Let’s make the output somewhat
more simpler to analyze, we’ll use the grep option in order to determine
which extensions are blocked and which are not.
Therefore, at the Options
tab, scroll down to the Grep – Match field, there remove all the
predefined keywords and add “blocked” over there.
Note –
This “blocked” keyword has
been added intentionally, as this is the error generated at when a wrong file
extension is uploaded. So rather than blocked keyword, you have to use the one
that displays as a part of an error message when you upload a restricted file.
As soon as we fire up the “Attack”
button, we’ll be redirected to the next page where the outputs are displayed.
Double click on the “blocked” section in order to sort the Request.
Cool !! From the below image,
you can see that we got all the blocked extensions mentioned. Now with
this, we can simply upload any file with an extension rather than the marked
ones.









































0 comments:
Post a Comment