PumpkinRaising is another CTF
challenge from the series of Mission-Pumpkin v1.0 created by keeping beginners
in mind and all credit for this VM goes to Jayanth. This level is all about
identifying 4 pumpkin seeds (4 Flags - Seed ID’s) and gain access to
root and capture final Flag.txt file.
You can download it from
here: https://www.vulnhub.com/entry/mission-pumpkin-v10-pumpkinraising,324/
Level: Beginner to
Intermediate
Penetrating Methodologies
Scanning
·
Nmap
Enumeration
·
Robots.txt
·
Abusing HTTP services
Exploiting
·
Ssh Login
Privilege Escalation
·
Abusing Sudo
right
Walkthrough
Scanning
Let’s start with network scanning as the IP of this VM is
192.168.0.11. So, initializing this VM by scanning open port and running
services over those port with the help nmap.
nmap -A 192.168.0.11
From its scan result, I found port 22 for ssh and 80 for
http are available, moreover it gave some hint for /robot.txt file that
disallows 23 entities.
Enumeration
So first we navigate to web browser and explored the VM IP and
welcome by following web page. Read the following message:
“To raise Pumpkins, we need to collect seeds at the first
step. Remember Jack? He is the only expert we have in raising healthy Pumpkins.
It’s time to get in search of pumpkin seeds”
From this message we can assume for “Jack” which
could be a username.
Further, I explored /robot.txt file suggested in nmap scan and
found some list of interesting directories, files and paths. Apart from all
entries I found few interesting entries such as: /hidden/notes.txt,
/underconstruction.html and /seeds/seed.txt.gpg. so, we have explored each entry one-by-one.
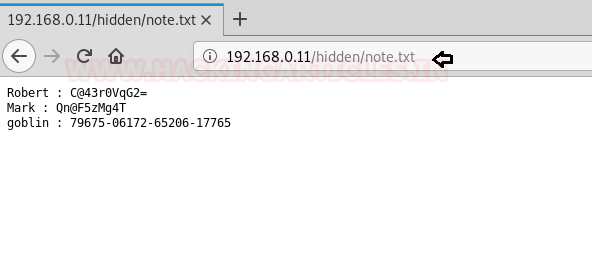
The hidden note.txt showed certain data which may be needed
to login credentials subsequently.
http://192.168.0.11/hidden/notes.txt
Robert: C@43r0VqG2=
Mark: Qn@F5zMg4T
goblin: 79675-06172-65206-17765
when I checked the source code of the homepage and here, I
found a link for pumpkin.html
On exploring source code of http://192.168.0.11/pumpkin.html,
I found a base32 encode string.
With the help of online base32 decoder we have decoded
the string and note the path /scripts/spy.pcap that could be a hint for seed’s
id.
To identity what is inside the spy.pcap file, I
simply downloaded the file in our local machine and used Wireshark to read the
network packet.
Here I found the first seed: 50609 from inside the tcp steam
as shown in the below image.
Again, we come back to pumkin.html page and I found
decimal string on scrolling same file.
On decoding decimal string, we found one more seed:96454
As you know we have enumerated /robots.txt and from inside
that we found another important file /underconstrution.html as
shown below. So, we have explored the source code of the web page and noted
hint for an image.
Now, we have explored the below URL and found a picture for
pumpkin which I have downloaded in my local machine.
http://192.168.0.11/image/jackolantern.gif
After downloading the pumpkin image, I check for hidden data
with help of stegosuite. This image was password protected image and if you
remembered we had enumerated “Mark: Qn@F5zMg4T” secret keys from inside
/hidden/notes.txt
I used the key: Qn@F5zMg4T for extracting the hidden file “decorative.txt”
from inside the stegno image.
So, when I opened this file, it gave me another PUMP-Ke-Mon
Pumpkin seed: 86568
Further I downloaded .gpg file as the link /seeds/seed.txt.gpg
which was mention in the robot.txt file.
gpg -d seeds.txt.gpg
So, when I tried to open the file, I noticed that it requires
the passphrase to decrypt the encrypted data which I don’t know. Here I tried
to use above enumerated keys but could not able to decrypt it. After so many attempts,
I successfully decrypted the file by entering SEEDWATERSUNLIGH which
was mentioned in the home page of website in the 2nd image.
On decrypting I
obtained following text file as shown below and it was a Morse encoded
text which used in telecommunication that encodes text
characters as standardized sequences of two different signal durations called
dots and dashes.
To decrypt the Morse text I have used cyberchef
which is an online decrypting tool. On decrypting the text, I found another BIGMAXPUMPKIN
seed 69507
As it was declared by author that in this VM we need to find
4 SEED’s ID and a root flag. Hence, we have collected all 4 seed’s id but for
getting root flag, we need to compromise the VM.
When I didn’t get any vulnerability to compromised it, I tried
to access ssh by the combination of all 4 seed found in this VM and used this
as password for user jack.
1.
SEED ID: 69507
2.
SEED ID: 50609
3.
SEED ID: 96454
4.
SEED ID: 86568
SSH login Password: 69507506099645486568
Yuppie!! We got the
shell access but for obtaining root flag we need to escalate the privilege from
low privilege shell to high. Therefore, I check for sudo rights for user jack
and found jack can run strace with sudo rights.
Hmmm! We can abuse
the sudo permission set for strace program. Hence type following and obtain the
root flag.
sudo strace -o/dev/null /bin/bash
cd /root
ls
cat flag.txt




























0 comments:
Post a Comment