Hello friends! This article will be helpful to
considerate the importance of event viewer and how to read the logs generated
by event view that help in troubleshoot of any system or application
problem.
In order
to view Event logs press “window key + R” to open run command and type “eventvwr.msc” then hit enter key.
Windows
Event Viewer is a tool which monitors activity of your system by
maintaining some kinds of log such as application log, system log and etc. It
start automatically when you turn on your system assemble the details critical
state about hardware and software. These logs help a system administrator to troubleshoot
the problems of machine and identify with what is going on. He could use Event
Viewer to view and manage the event logs.
From below image you can observe the window
screen is categories into three panels as describe below:
The left side
contains some folders which keep records of every task perform by machine such
as windows log i.e. system or security.
The middle part contains a list of events,
it contains detail of every event occurred by recording their logs which is
known as Event type such as
“information, warning or error” and their details.
The right
side presents list of some other actions such as creating custom views,
filtering, or even creating a scheduled task depends on a specific event.
Most Important Event Logs
Remarkably there are three kinds of Event Logs:
System
Log: Any action or task performed by operating system such as
such unexpected shutdown and turn ON/OFF of any service is recorded under the
System log.
Application
Log: The Application log records all events by programs such as
successful installation or stop responding while running.
Security
Log: The Security log records security events, such as
legitimate and unacceptable logon attempts which will represent as audit
success for valid attempt and audit failure for invalid attempt. These logs help in identifying any possible
breaches to security. By default security log is disabled you need to enable
them for you system through local security policy.
Enable Local Security Policy for Security logs
Now open Local security policy logs press “window key +
R” to open run command and type “secpol.msc” then hit enter key, then change
security setting for Audit policy under security
setting > Local policies> Audit policy in order to receive its log
inside event viewer security logs.
Form given below image you can observe that there is not
any single security policy is auditing, which means it will not create any
security log inside event viewer.
Let’s enable any one policy for auditing to test what
kind of security log will be generated when we will move into event viewer
security log. Here I had chosen “Audit
account logon event” for auditing.
It will open a new window for its property setting you as
shown in given image Enable the
check box for Success and Failure, click on apply to enable this
policy for auditing.
Hence when a user will Enter password on logon screen it
will generate log as audit success for valid login attempt and audit failure
logs for invalid attempt.
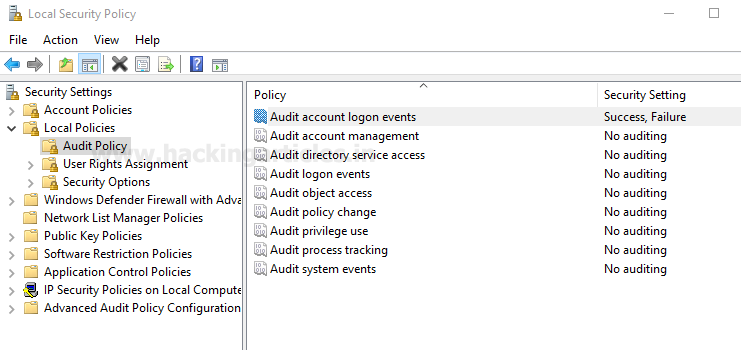
Now you can observe from given below image it is showing
auditing: success & failure for account logon event.
Check by Practical
You can check it by login into your system and type wrong
password as invalid attempt and then finally enter correct password for valid
attempt and then verify generated security logs for you this kind of action.
In order to view Security Event logs press “window key +
R” to open run command and type “eventvwr.msc” then hit enter key.
Now explore Security
event logs under Windows logs, here you will observe some log entries
generated by Security-Auditing as Audit success for valid login attempt and
Audit failure for invalid login attempt.
Event Types
The details of logs are depends upon different types of
event and event logs mainly classify in five categories as describe below:
|
Event Type
|
Definition
|
|
Error
|
A considerable trouble, such as loss of data or loss of
functionality or fault in problem execution.
|
|
Warning
|
This type of event that might not be considerable, but
might point out a future problem.
|
|
Information
|
An event that describes the successful operation of an application,
driver, or service.
|
|
Success Audit
|
An audited security access attempt that succeeds. {In
security logs}
|
|
Failure Audit
|
An audited security access attempt that fails. {In
security logs}
|
From given below image you can observe that the logs are
records in 5 columns to store their important details
Level: displays
event type
Date and time:
displays the date and time of event type when it generated
Source: source of
event type due to which event log is created.
Event Id: The
Event Viewer uses event IDs to describe the uniquely identifiable events that a
Windows computer can come upon.
Task category:
Used to represent an activity of the event launcher program.
General Details of
Event Log
Admin can took help of General property in order to read brief description of event log
which could be helpful in troubleshoot of some problems. He can also read
complete detail of property for any occurred event which is stored under Details Tab.
General property contains following information of an
event log:
|
Property name
|
Description
|
|
Log Name
|
Window log category it may be system, application or
security logs.
|
|
Source
|
The source that produced
the event. It might be any application or system component
|
|
Event Id
|
The Event Viewer uses event IDs to describe the uniquely
identifiable events that a Windows computer can come upon.
|
|
Level
|
Information,
Warning, Error, Success Audit and Failure Audit
|
|
User
|
Display user
name who has logged onto the computer when the event occurred
|
|
OpCode
|
Operational code
Contains a numeric value that
identifies the activity or a point within an activity that the application
was performing when it raised the event. For example, initialization or
closing.
|
|
Logged
|
The name of the
log where the event was recorded
|
|
Task category:
|
Used to represent an activity of the event launcher
program.
|
|
Keywords
|
It can be used to filter or search for events. Such as
“audit failure” or "Respond time."
|
|
Computer
|
The computer
where the event occurred
|
Clear Logs
If you want to remove entire records of logs then move your
cursor at right side of window screen and click on option “clear log” under
Action tab as shown in given below image. Then a dialog box will pop up to
confirm your action, here it let you to save the previous log in other
location.
If you want to keep
record of specific event type for a particular task occurred then you can use
“custom event” which will only keep records of those event type which you have
defined for a particular service or application.
Again move your cursor at right side of window
screen and click on option “custom event” under Action tab as shown in given
below image.
A window screen will pop up which will generate a
customize log according to you. From given below image you can observe that I
wish to get few event type for which check box is enabled from event source as
Remote access only for invalid login attempt.
This custom event log will saved in a new folder “RDP” under
event viewer > custom view. Enter the name for your event log and
description as shown in given below image. It decreases the level of records
and makes an ease in problem troubleshoot.
This section is
applicable only for hacked system, so if you have hacked any windows machine
using Kali Linux and obtain victim’s meterpreter session then run given below
command for deleting all record of logs from his system. Preserve yourself from
being caught by any kind of investigation.
Meterpreter> clearev





















0 comments:
Post a Comment