Today we are going to take on a new challenge KFIOFan2.
The credit for making this VM machine goes to “Khaos Farbauti Ibn Oblivion” and
it is a boot2root challenge where we have to root the server to complete the
challenge. You can download this VM here
Security Level:
Beginner
Penetrating Methodology:
Scanning
·
Netdiscover
·
Nmap
Enumeration
·
Enumerating ftp services
Exploitation
·
Uploading php shell to get ssh
key
Privilege
Escalation
·
Buffer Overflow to get sudo
rights
Walkthrough:
Scanning:
First thing first, scan the vulnerable
machine using nmap
nmap -p-
-A 192.168.1.33
Here we found that the only port open is
port 26921
Let’s take a look at what the ftp service has
to offer. The ssh banner gave us a message
“Salut Alice ! Suite a l'attaque sur notre
precedent serveur, j'en prepare un nouveau qui sera bien plus securise ! C'est
en travaux pour l'instant donc s'il te plait ne touche a rien pour l'instant...
Bob”
Which translates to
“Hi Alice! Following the attack on our
previous server, I prepare a new one that will be much more secure! It is under
construction for now so please do not touch anything for now ... Bob”
We found anonymous login here. After logging in, we found 4 images and a
directory named `serrure`. We downloaded the images and checked the directory
but found nothing in the directory
After
getting not much information but only 4 images, we tried to decipher the hint
behind this so we tried to find any kind of stegnographical content. So we
tried to get some kind of information from the images by another method. We
combined the images together and found that the catch was very simple. In the
centre of the combined image we found a name of a file named as “cle.txt”.
We tried to
find this file but did not find it anywhere. So we tried to do a little bit
different step. We created a file with dummy content and put it into the target
system through ftp
After
putting the file in the serrure
directory, we tried to scan the target system again. Looks like the cle.txt file worked as a key to unlock
another port 26980 running http service
nmap –p-
-A 192.168.1.33
Now that we have found one other port, we
tried to enumerate the website but the
welcome message looked something like this
“Tout
ce qui est, est père du mensonge et fils du néant”
Which translates into
“All
that is, is father of lies and sons of nothingness”
While analysing the page source of the
webpage, we found a comment something like this
“”
“”
Which translates into
“<!
- Test presence cle.txt file: OK ->”
“<!
- Test content cle.txt file: Error ->”
Indicating that the content of cle.txt file
needs to be changed
Alongside this we tried to get more details
about the target machine and found a directory named uploads, but with none
content
Now to put the correct content in the cle.txt
file, we tried to look for a meaning for the hint. After some research, we
found an article written by the author of this lab. In this article we found
that the hint is the description of the authors nickname i.e. Khaos Farbauti
Ibn Oblivion.
We used this name as content of
the cle.txt and replace this file in the serrure directory through ftp
echo “Khaos Farbuti Ibn Oblivion”
> cle.txt
ftp 192.168.1.33
26921
cd serure
delete cle.txt
put cle.txt
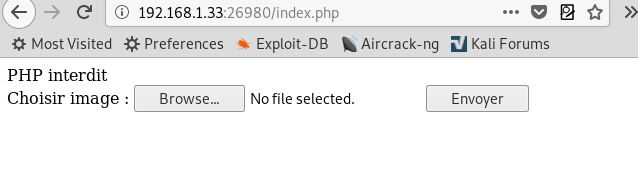
Now let’s check the webpage again.
This time we found a file upload module in place, looks like the content of
cle.txt file was being used to change the functioning of webpage. Now all we
need to do is upload a shell, first we tried to upload a txt file and the was
uploaded easily
Next we tried uploading a php shell but was
blocked
To bypass the security we tried to upload a .php5
shell and succeded
Now to verify that our shell is uploaded, we
tried to check the uploads directory and found that our file is there
Now we
tried to execute the shell but failed, after some attempts we thought that
there might be a .htaccess which might
be blocking us from executing a php application. So to override that we needed
to over-write the previous one, we tried to create a blank .htaccess file and
tried to upload that.
As we were able to upload the .htaccess file
we tried to use the uploaded shell to run system commands and were able to do
that.
After some searching we found a ssh key
Now all we need to find is a ssh port to
connect. We did nmap scan again and this time we found an ssh port on 26922
nmap -p- -A 192.168.1.33
Now we have a ssh port and a ssh key, lets try
to combine them together and get a ssh connection. We saved the ssh key into a
file named id_rsa, provided it 0600
permission and tried to use that key for connection. Once getting the
connection we tried to find all the files with suid permissions and found that there
is a file named test
chmod 0600 id_rsa
find / -perm –u=s –type f 2>/dev/null
When we tried to execute the file, it asked us
for password and we don’t have any. We tried to check the strings in the file
using the strings command and found some interesting things.
strings test
First we found that there is a system function
in use, meaning there is a system command being executed.
Second we found a system command “touch /root/authorize_bob” indicating
that this is the system command that we want to be executed
Third we found a string “aliceestnulle” right below the password prompt “Mot de passe”
We tried to run the file again with the
password that we found and got a message
As we were not able to get anything even after
entering correct password, we tried to get to get details from gdb
gdb test
set disassembly-flavor intel
disassemble main
start
We started the execution of the program using
start command, when the program asked for password, we tried to discover buffer
overflow vulnerability. We created a input string of length 50 using
pattern_create.rb file from metasploit-framework.
cd /usr/share/metasploitable-framework/tools/exploit
./pattern_create.rb -l 50
After putting the input we found that after
certain length our input is put into an executable stack
Before going on multiple types of buffer
overflow exploitation, we went to our previous findings just to check whether
we have some other hints to follow, fortunately we found that when we found the
touch command in the strings command output, right above that there was a
string having content as
lancement
debug
when we translated this it resulted in
launch
debug
when we tried to check the debug function, we
found that there is a system function being executed inside the debug function.
disassemble debug
Next we are left with the attempt to execute
the debug function, so with took the length of the string which resulted in
buffer overflow, and replaced the characters which were stored in the
executable stack with the address of the debug function.
python -c ‘print
(“Aa0Aa1Aa2Aa3Aa4Aa5Aa6”+”\x20\x48\x55\x55\x55\x55”)’ | ./test
After running the same input for multiple
attempts, we logged out of the ssh session and reconnected and tried sudo
command and it worked.
sudo su
Let’s capture the flag and get finished with
the CTF
cd /root
cat flag.txt


































0 comments:
Post a Comment