While solving CTF
challenges, serveral times I have to use the most amazing tool “Impacket” which
is a collection of Python classes for working with network protocols, Infact
some of its python classes are added to metasploit framework for taking remote
session.
Table of content
§ Introduction to Impacket
§ Lab set-up Requirement
§ Remote code Execution
§ SMB/MSRPC
§ Kerberos
§ Windows Secrets
§ Server Tools/MiTM Attacks
§ WMI
§ Known Vulnerabilities
§ MSSQL / TDS
§ File Formats
§ Others
Introduction to Impacket
Impacket is a collection
of Python classes for working with network protocols. Impacket is focused on
providing low-level programmatic access to the packets and for some protocols
(e.g. SMB1-3 and MSRPC) the protocol implementation itself.
Packets can be constructed from scratch, as well as parsed from raw data, and the object oriented API makes it simple to work with deep hierarchies of protocols. The library provides a set of tools as examples of what can be done within the context of this library.
Packets can be constructed from scratch, as well as parsed from raw data, and the object oriented API makes it simple to work with deep hierarchies of protocols. The library provides a set of tools as examples of what can be done within the context of this library.
The following protocols
are featured in Impacket:
§ Ethernet, Linux "Cooked" capture.
§ IP, TCP, UDP, ICMP, IGMP, ARP.
§ IPv4 and IPv6 Support.
§ NMB and SMB1, SMB2 and SMB3 (high-level
implementations).
§ MSRPC version 5, over different transports: TCP,
SMB/TCP, SMB/NetBIOS and HTTP.
§ Plain, NTLM and Kerberos authentications, using
password/hashes/tickets/keys.
§ Portions/full implementation of the following MSRPC
interfaces: EPM, DTYPES, LSAD, LSAT, NRPC, RRP, SAMR, SRVS, WKST, SCMR, DCOM,
WMI
§ Portions of TDS (MSSQL) and LDAP protocol
implementations.
Lab set-up Requirement
For the following
practical we will require two systems,
A Windows Server with
Domain Controller Configured
A Kali Linux
Here, in our lab scenario
we have configured the following settings on our systems.
Windows Server Details
§ Domain: Pentest.local
§ User: Administrator
§ Password: Ignite@123
§ IP Address: 192.168.1.103
Now let’s install the
Impacket tools from GitHub. Firstly, clone the git, and then install the
Impacket as shown in the screenshot.
git clone https://github.com/CoreSecurity/impacket.git
cd impacket/
python setup.py install
This will install Impacket on your Kali Linux, now after
installation let’s look at what different tools does Impacket have in its box.
cd
impacket/examples
ls -la
There are several python classes as shown in the below
image, in this article I had place all script in a same category which are
preforming same task.
§ Remote code
Execution : atexec.py, dcomexec.py, psexec.py,
smbexec.py and wmiexec.py
§ SMB/MSRPC : getArch.py, ifmap.py, lookupsid.py, samrdump.py, services.py,
netview.py, smbclient.py, opdump.py, rpcdump.py and reg.py
§ Kerberos: GetTGT.py, GetST.py, GetPac.py, GetUserSPNs.py,
GetNPUsers.py, ticketer.py and raiseChild.py
§ Windows
Secret: secretsdump.py and
mimikatz.py
§ Server
Tools/MiTM Attacks: ntlmrelayx.py,
karmaSMB.py and smbserver.py
§ WMI: wmiquery.py and wmipersist.py
§ Known
Vulnerabilities: goldenPac.py,
sambaPipe.py and sambaPipe.py
§ MSSQL / TDS:
mssqlinstance.py and mssqlclient.py
§ File Formats:
esentutl.py, ntfs-read.py and registry-read.py.
§ Others: GetADUsers.py, mqtt_check.py, rdp_check.py,
sniffer.py, ping.py and ping6.py
In this tutorial guide we have elaborated two category
(Remote Code Execution & SMB/MSRPC) in brief description.
Remote code Execution
atexec.py:
This example executes a command on the target machine through the Task
Scheduler service and returns the output of the executed command.
./atexec.py
raj/Administrator:Ignite@123@192.168.1.103 systeminfo
dcomexec.py: A
semi-interactive shell similar to wmiexec.py, but using different DCOM
endpoints. Currently supports MMC20.Application, Shell Windows and Shell Browser
Window objects.
./dcomexec.py raj/Administrator:Ignite@123@192.168.1.103
dir
psexec.py:
PSEXEC like functionality example using RemComSvc.
What is RemCom : RemCom is a small (10KB upx
packed) remoteshell / telnet replacement that lets you execute processes on
remote windows systems, copy files on remote systems, process there output and
stream it back. It allows execution of remote shell commands directly with full
interactive console without having to install any client software. On local
machines it is also able to impersonate so can be used as a silent replacement
for Runas command.
Source:
https://github.com/kavika13/RemCom
./psexec.py
raj/Administrator:Ignite@123@192.168.1.103 net user
smbexec.py: A
similar approach to PSEXEC w/o using RemComSvc. The technique is described
here. Our implementation goes one step further, instantiating a local smbserver
to receive the output of the commands. This is useful in the situation where
the target machine does NOT have a writeable share available.
./smbexec.py
raj/Administrator:Ignite@123@192.168.1.103
wmiexec.py: A
semi-interactive shell, used through Windows Management Instrumentation. It
does not require to install any service/agent at the target server. Runs as
Administrator. Highly stealthy.
./wmiexec.py
raj/Administrator:Ignite@123@192.168.1.103 netstat
SMB/MSRPC
getArch.py:
This script will connect against a target (or list of targets) machine/s and
gather the OS architecture type installed by (ab) using a documented MSRPC
feature and doesn't require any authentication at all.
./getArch.py
-target 192.168.1.103
Note: Remember this
trick will not work if the target system is running Samba.
ifmap.py: This
script will bind to the target's MGMT interface to get a list of interface IDs.
It will used that list on top of another list of interface UUIDs seen in the
wild trying to bind to each interface and reports whether the interface is
listed and/or listening.
./ifmap.py
192.168.1.103 135
lookupsid.py:
A Windows SID brute forcer example through [MS-LSAT] MSRPC Interface, aiming at
finding remote users/groups.
./lookupsid.py
raj/Administrator:Ignite@123@192.168.1.103
samrdump.py:
An application that communicates with the Security Account Manager Remote
interface from the MSRPC suite. It lists system user accounts, available
resource shares and other sensitive information exported through this service.
./samrdump.py
raj/Administrator:Ignite@123@192.168.1.103
If you will notice the image given below then you will
observe that username along with uid and complete account details such password
complexity and so on.
services.py: This
script can be used to manipulate Windows services through the [MS-SCMR] MSRPC
Interface. It supports start, stop, delete, status, config, list, create and
change.
./services.py
raj/Administrator:Ignite@123@192.168.1.103 list
As you can observe from the given below image that it has
dump list of all services running or stopped.
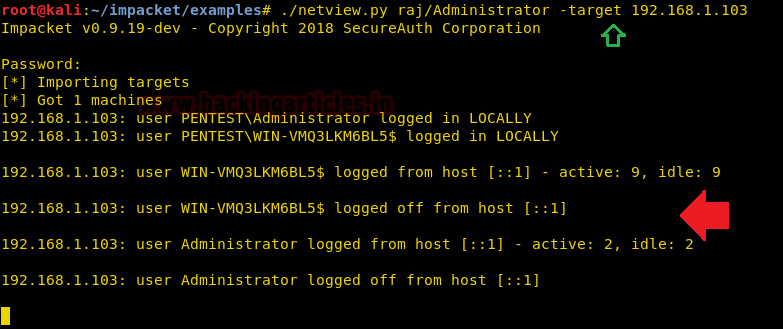
netview.py:
Gets a list of the sessions opened at the remote hosts and keep track of them
looping over the hosts found and keeping track of who logged in/out from remote
servers.
./netview.py
raj/Administrator -target 192.168.1.103
As we all know netview command identify the sessions
opened at the remote hosts and keep track and from the given below image you
can observe it is keep on tracking whenever target machine is active or logged
off.
smbclient.py:
A generic SMB client that will let you list shares and files, rename, upload
and download files and create and delete directories, all using either username
and password or username and hashes combination. It's an excellent example to
see how to use impacket.smb in action.
./smbclient.py
raj/Administrator:Ignite@123@192.168.1.103
From the given below image you can observe, it is showing
all shares directory of the target machine.
opdump.py:
This binds to the given hostname:port and MSRPC interface. Then, it tries to
call each of the first 256 operation numbers in turn and reports the outcome of
each call.
To run this command you have to give MSRPC interface and
for that first you need to run ./ifmap.py command and then from its output
result choose UUID for which you want to run opdump.py script.
./ifmap.py
192.168.1.103 135
./opdump.py
192.168.1.103 135 99FCFEC4-5260-101B-BBCB-00AA0021347A 0.0
rpcdump.py:
This script will dump the list of RPC endpoints and string bindings registered
at the target. It will also try to match them with a list of well-known
endpoints.
./rpcdump.py
raj/Administrator:Ignite@123@192.168.1.103
reg.py: Remote
registry manipulation tool through the [MS-RRP] MSRPC Interface. The idea is to
provide similar functionality as the REG.EXE Windows utility.
./reg.py
raj/Administrator:Ignite@123@192.168.1.103 query -keyName
HKLM\\SOFTWARE\\Policies\\Microsoft\\Windows -s
Reference
Source:
https://www.secureauth.com/labs/open-source-tools/impacket