Burp Logger++: A Powerful Extension
In this article, we’ll learn about a powerful Burp Extension
cool tool called "Burp Logger++". It is like a super detective for
websites, always on the lookout for any hidden problems. It is an extra feature
that you can add to Burp, which lots of web experts use to find issues on
websites.
Suppose you are a web explorer, and you want to know
everything about a website. Burp Logger++ is like your trusty notebook. It is
super helpful because it has a magical filter. You can tell it what kind of
information you are looking for, and it will only show you those things.
With Burp Logger++, you can also color-code things. Think of
it like using different colors to highlight the most important parts of a
picture. This helps you spot the important stuff quickly.
·
Setting Up & Navigating
·
Query-Based Filter
·
Filter Library
·
Regex-Based Filter
·
Export Data Feature
Setting Up & Navigating
You can download and install the extension from the BApp
Store. Go to Extensions > Bapp Store. Here, search for Logger++ or simply
scroll down.
Click on it, on the right side scroll down and install it.
After successfully installation, it will appear on the tool
bar.
Navigating
There are a lot of options visible to you. First, let's
explore the "Options" tab to discover what advanced settings are
included in this extension?
Navigate to "Options" to see the various log
filter options. It allows you to customize logging setting as per your
preference.
Logger++ is running by default. Here are some others
important setting:
•
Log Filter: This feature lets you specifically
choose the requests that you don't need to record for analysis, or you may turn
it off when not in use.
•
Log From: It enables you to capture data from
the specific logs that you want to capture from.
•
Import: You can import log data from CSV and
OWASP ZAP reports with this function.
•
Export: The log data can be exported for further
analysis.
Depending on your preferences, you can use different
configuration. We are sticking with the default settings for the time being.
Query-Based Filter
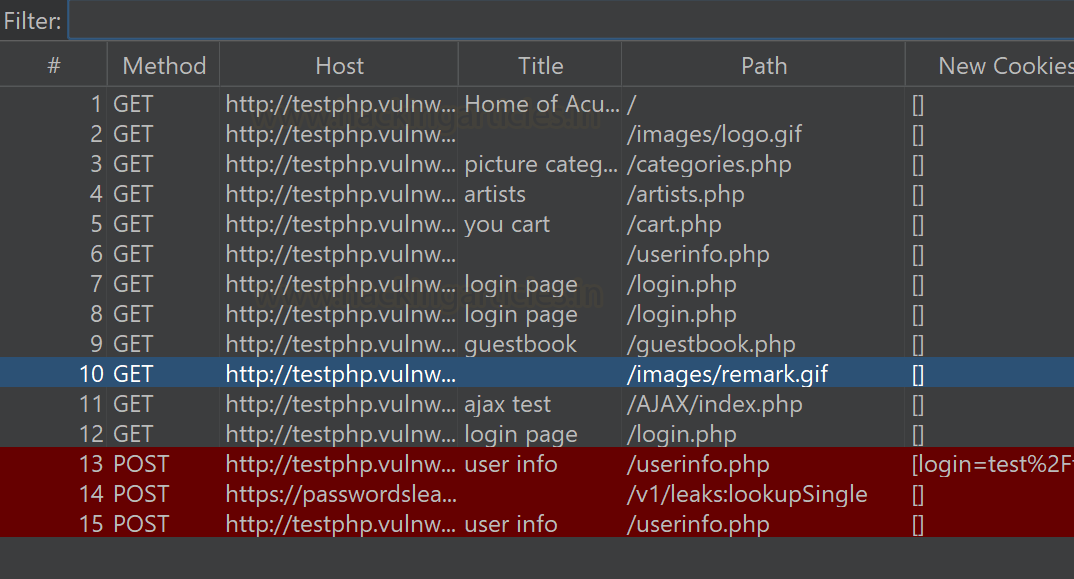
The View Log tab contains all the logs. Using this website
"vulnweb" as an example, browse it and simply scan the entire site;
all logs will show up here under the View Logs page.
Now, go to Signup. In order
to capture the logs for credentials, enter the test login details.
Username: test
Password: test
then click on
"Login".
Let’s update some more details to capture more requests for
further analysis.
You can see that all requests have been captured here in
View Logs.
Magical Filter
You can use filter to selectively view or manipulate HTTP
requests and responses. These filters help you focus on specific aspects of the
web traffic and are especially useful during security testing. The working is
based on query string. It accepts a logical query and returns output based on
them.
You have some advanced choices with the filter options:
• Entry: You can apply filters according to number, tool, tags, InScope, and other criteria.
•
Request: It lets you filter just the
request itself using many options such as header, body, URL, method,
parameters, cookies, etc. As shown below:
•
Response: It lets you filter just the
response by using various options such as header, body, Inferred Type, Method,
Parameters, cookies etc. As shown below:
Scenario 1: Let's suppose you just want to view
HTTP POST requests from all logs. It is understood that HTTP POST
parameters are in HTTP Request.
Go to Filter bar > right click > Select Request >
Select Method
The method has been chosen and visible in filter bar.
Quary: Request.Method == “POST”
And hit enter. As result, Only HTTP POST Method requests appear.
Scenario 2: Taking another example, suppose we just
want to view the requests which contains any username information from all
logs.
Go to Filter bar > right click > Select Request >
Select Body
Quary: Request.Body CONTAINS “uname”
As a result, the following request is highlighted:
Below are some useful queries which are helpful during
penetration testing.
|
Some Useful
Filter Queries |
|
|
JSON Injection (Check for only one json request) |
Response.InferredType == "json" |
|
Injections Attack (Check for HTML, XML, JSON) |
Response.InferredType IN ["json",
"html", "xml"] |
|
Disclosed Server Information |
Response.header CONTAINS “Server:” |
|
Exposed Sensitive File |
Response.Body CONTAINS [“.git”, “.config”, “.zip”, “.swf”,
“.doc”, “.pdf”, “.xlsx”, “.csv”, ] |
|
Exposed Sensitive Path |
Request.Path CONTAINS [“/git”, “/etc”, “/var”] Request.Path MATCHES “/account*” |
|
Sensitive Parameter in Query String |
Request.Path CONTAINS [“id”, “username”, “password”,
“role”, “IsAdmin”] |
|
Sensitive Parameter in Request |
Request.Body CONTAINS [“id”, “username”,
“password”, “token”, “role”, “EnterpriseID”, “IsAdmin”] |
|
Missing Robots.txt |
Request.Path MATCHES “/robots.txt” |
|
CORS Misconfiguration |
Response.Header MATCHES “
Access-Control-Allow-Origin: *” |
|
Check for CSRF Token |
Request.Method == "POST" AND Request.Body
CONTAINS "csrf" |
|
URL Redirection |
Request.Path CONTAINS [“redirect=”, “page=”,
“url=”, “index.page=”] |
Filter Library
We can use the saved or pre-configured filters from the
library directly with the help of the Filter Library. When you start testing,
you do not have to manually type or remember the query string of filter
pattern.
Click on “Add Snippet”.
Here are two values that must be added.
•
Alias: Put any Alias name for your query
string.
•
Snippet: Add query string here.
As you can see below, I have added a filter for
Request_Type: Request.Method == “POST”
You no longer have to type repeatedly to find only POST
requests. You can color-code this request so that the highlighted request
stands out among all captured requests on the View Logs page.
Click on Use as Color LogFilter > Select Background Color
> check Enable and save it.
All POST requests are now highlighted in
"Dard-Red" on this page.
Similarly, you can save whole test scenarios in the Filter
Library. There is two ways to call the saved filter:
Method 1: In Filter Library, click on Set as
LogFilter.
It will directly run the query and the desire result will be
displayed.
Method 2: Use
“#” with Alias name directly in filter bar.
And hit enter. The equivalent outcome will appear as follows:
Regex-Based Filter
Burp Logger's regex filter is a powerful feature that helps
web security professionals pinpoint specific data within the vast sea of
information during security testing.
You need to specify the regular expression (regex) pattern.
This pattern acts like a search query, telling Burp Logger++ what kind of data
you want to capture. You can create regex expression pattern to find data as
like Email Address, IP Address, Server-side error messages, Software version
disclosed, Any API Key exposed etc.
Go to Logger++, click on Grep Values tab. Here, you can see
more filters to limit the search criteria.
·
Search Response = It will perform search only in
responses.
·
Search Request = It will perform search only in
requests.
·
In Scope Only = If you added the target URL in
Scope only then it will only search within the scoped target.
For the time being, choose to search through every request
and response. Let’s take an example, if you want to find email addresses in web
traffic, your regex pattern might look like
Regex: [\w\.-]+@[\w\.-]+.
Directly paste this expression under Regex bar and press
enter.
Consequently, the /userinfo.php request — which includes the
email mentioned above is displayed.
You have two ways: Manually search through the complete
request/response or click on Unique Result. The results that match the regex
expression will be displayed only in Unique Results.
Similarly, Let’s check for IP Address also,
Regex Exp: \b\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}\b
It is evident that a POST request is being sent through the
IP address 10.10.1.10.
In the same way, you can check for other important
information like if you want to find the web traffic contains any FTP, HTTP,
WWW.
Regex: \b(ftp|www|http)[^\s]+
For reference, the following link includes helpful regex
expression to find the disclosed server version within the error information.
https://github.com/lwierzbicki/RegexFinder/blob/main/burp.regex.tsv
Export Data Feature
Burp Logger's data export feature is a valuable tool for web
security professionals. It allows you to save, analyze, and share the captured
data efficiently, making it an essential tool for documenting findings,
performing in-depth analysis, and collaborating with others in the field of web
security.
Why Export Data Feature is Helpful?
·
Data Preservation: Exporting data from
the Logger++ allows you to save a record of your testing session. This is essential
for documentation and analysis.
·
External Analysis: By exporting data, you
can use external tools or software to perform in-depth analysis, generate
reports, or share findings with team members.
·
Archiving Evidence: It helps in
preserving evidence of potential vulnerabilities or security issues discovered
during testing, which is crucial for audits and compliance.
·
Collaboration: Exported data can be
easily shared with colleagues or experts for collaborative analysis, making it
an asset in team-based security testing.
·
Customization: Depending on the export
format chosen, you can tailor the exported data to meet specific reporting or
analysis requirements.
Supported Formats:
·
Base64 JSON Format: Base64-encoded data
is often used to include binary data within a JSON structure.
·
JSON Format: JSON is a lightweight
data-interchange format used for structured data.
·
CSV Format: CSV files are widely
supported and can be opened in spreadsheet software like Microsoft Excel or
Google Sheets.
·
HAR Format: HTTP Archive (HAR) format is
used for capturing and storing the performance-related data. The HAR format
contains detailed information about HTTP requests and responses.
For Example, suppose you want to export all POST requests
for further analysis.
Select the associate requests > right click > choose
Export entries as > Export as CSV
Now Select All > Choose Save > Enter the name and
click on Ok.
Save the result to your system offline. You can examine the
CSV file; it contains all of the values that you chose to save.
You may select the only required values to store based on
your needs.
That’s All, Cheers!!!
Conclusion
People like Burp Logger++ because it makes their job easier.
It is your smart friend who helps you find hidden treasures (or problems) on
websites. With its filters and colorful highlights, has the superpowers for
website exploration.
So, if you are a web detective, it is a tool that will make
your job much more fun and efficient. Give it a try and see how it can help you
on your web adventures!
Author: Megha is a Certified Security Professional
with extensive experience. She is a passionate Researcher and Technical Writer
at Hacking Articles. Contact here.






































0 comments:
Post a Comment