This article aims to demonstrate an open-source breach & emulation framework through which red team activity can be conducted with ease. It focuses on MITRE simulation and has tons of other functions that can be used in the activity.
Table
of Contents
MITRE Att&ck
Caldera
·
Pre-requisite & dependencies
·
Interface
·
Installation
·
Plugins
Campaigns
·
Step1: Abilities
·
Step2: Deploy an Agent
·
Step3: Setting up operations
·
Step4: Exporting the result
Conclusion
Mitre
Att&ck
Mitre
framework provides list of all the Tactics, Techniques
and Procedure (TTPs) & their corresponding sub-techniques arranged in a well-structured
form which can be used in red team activities.
Caldera
CALDERA breach & emulation tool designed to easily automate
adversary emulation, assist manual red-teams, and automate incident response.
The framework consists of two components:
The core system: This is the framework code,
consisting of what is available in this repository. Included is an asynchronous
command-and-control (C2) server with a REST API and a web interface.
Plugins: These repositories expand the core framework
capabilities and providing additional functionality. Examples include agents,
reporting, collections of TTPs and more.
Pre-requisite & dependencies
These requirements are for the computer running the core
framework:
·
Any Linux or MacOS
·
Python 3.7+ (with Pip3)
·
Recommended hardware to run on is 8GB+ RAM and
2+ CPUs
·
Recommended: GoLang 1.17+ to dynamically
compile GoLang-based agents.
Installation
Follow these steps for setting up caldera:
git clone https://github.com/mitre/caldera.git --recursive

cd caldera
pip3 install -r requirements.txt
python3 server.py –insecure
Interface
Caldera provides web interface which is simple to navigate and use.
http://127.0.0.1:8888
username: red
Password: admin


Plugins
The Plugins category offers a list of all current plugins and
allows you to quickly and easily access their functionality.
·
Access (Red team
initial access tools and techniques)
·
Atomic (Atomic
Red Team project TTPs)
·
Builder (Dynamically
compile payloads)
·
CalTack (embedded
ATT&CK website)
·
Compass
(ATT&CK visualizations)
·
Debrief (Operations
insights)
·
Emu (CTID
emulation plans)
·
Fieldmanual (Documentation)
·
GameBoard (Visualize
joint red and blue operations)
·
Human (Create
simulated noise on an endpoint)
·
Manx (Shell
functionality and reverse shell payloads)
·
Mock (Simulate
agents in operations)
·
Response (Incident
response)
·
Sandcat (Default
agent)
·
SSL (Enable
https for caldera)
·
Stockpile (Technique
and profile storehouse)
·
Training (Certification
and training course)
To know
more about particular plugin, follow the link.
Campaigns
Agents, adversaries, and operations make up the Campaigns
category, which may be used to build up the numerous agents, adversaries, and
operations needed for a red team operation or adversary emulation.
Step1: Deploy an Agents
To begin with initial access we need to implant an agent inside
the target system.
To set up an agent or listener:
1.
In campaign tab, click on agents

2.
Choose an agent (3 types currently available)

3.
Choose the platform (Windows, Linux or Darwin
[mac OS])

4.
As soon as the platform is selected, you need
to set up the IP, Port & name of the implant

5.
It will also give set of commands needed to be
executed on the target
·
In case of Linux/Mac OS, execute it on
terminal

·
Deploy agent inside the target machine by
simple copy paste

·
In case of Windows, execute it on PowerShell (Bypass
the execution policy first)
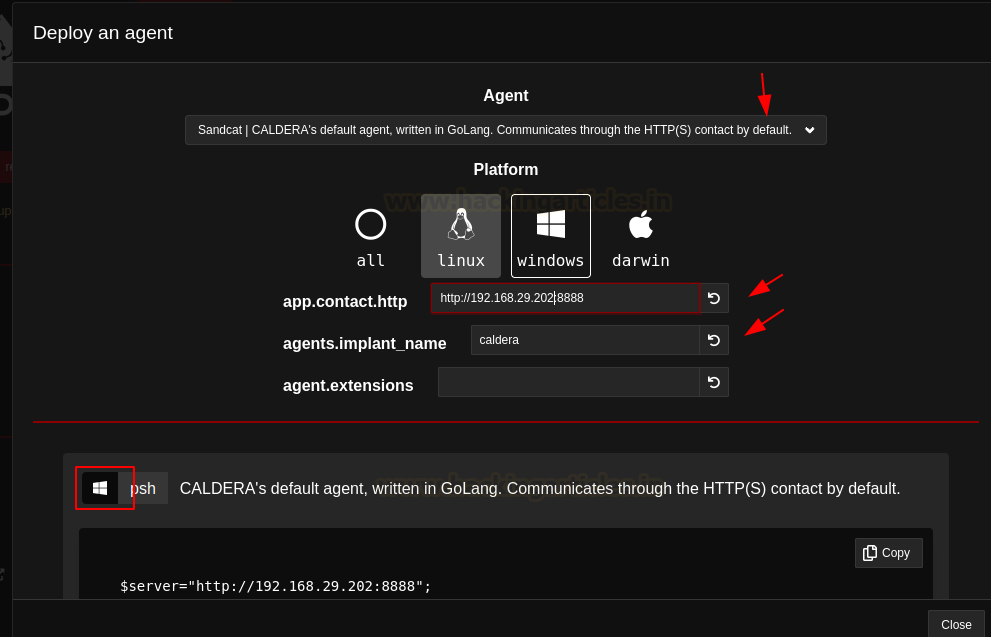
·
Deploy agent inside the target machine by
simple copy paste.
6.
The agent pops backs onto caldera which specifies
the command which was executed on the victim end was successful

Step2: Abilities
An ability is a specific ATT&CK tactic/technique
implementation which can be executed on running agents. Abilities will include
the command(s) to run, the platforms / executors the commands can run on (ex:
Windows / PowerShell), payloads to include, and a reference to a module to
parse the output on the CALDERA server.

As you can see in above ss, we can select Platform and related
TTPs. Let us take discovery as a tactic & Linux as platform (same tactic
demonstrated for windows in this article)

Step3: Setting up Operations
After setting up the agent, now it is time to run the abilities or
the set of instructions as shown above. For this we need to set up an operation
To do this:
1.
Under Campaigns tab, select operations
2.
Choose Create operations

3.
Choose the adversary (Adversary Profiles
are collections of ATT&CK TTPs, designed to create specific effects on a
host or network. Profiles can be used for offensive or defensive use cases.)

4.
Fill in the details and specifications of the
operation you want to run

5.
Click on start, after a while you can see that
it starts running and populating the results on the screen
6.
As you can see, all set of commands running is
obfuscated in base64nopadd format (also you can select other
options specified), we can also see the command and also, we can view output of
the command (Also, we can see the status of the task performed)
Step4: Exporting
the result
After the activity has been completed, we can extract the report
in two ways:
1.
Directly from the download tab which appears
after operation is completed

2.
Go to debrief tab, choose the pointers
to be included in the report; then download the full report as PDF


Conclusion
We have thus been able to perform the adversary simulation by the
help of Caldera. Using this framework, Red/Purple team activities can be easily
performed.
Reference: https://caldera.readthedocs.io/en/latest/
Author: Ankit Sinha is an infosec researcher















0 comments:
Post a Comment