Introduction
In the series of Privilege escalation, till now we have learned
that Microsoft Windows offers a wide
range of fine-grained permissions and privileges for controlling access to
Windows components including services, files, and registry entries. Today
through applications we are going to exploit the privileges .Many GUI applications
need the higher privileges other than the current user have, to access some of
its particular services. Secondly, just due to misconfiguration of application.
Let’s deep dive into it.
Table of Content
·
Introduction
·
Prerequisites
·
Lab setup of insecure
GUI Application
·
Abusing Insecure
GUI Application
Prerequisites:
Machine A-Window 10 (Ignite as admin user)
Notepad++ Installed application on window 10
Lab Setup of Insecure GUI Application
Machine A, has ignite as an admin user.
Now ,by the whoami /priv command we get to know that “Ignite
“an admin user has only 5 privileges of shut down, change notification etc.
with the enable and disable state which are displayed in the below screenshot
Whoami /priv
We have to understand that if any user has admin access even
though that user does not have full or higher privileges.
Now we will check the ignite admin user’s privileges by
adding a new user “demo”. Unfortunately access is denied. It means “ignite”
user does not have full higher privileges.
Install Notepad++ on window 10 and misconfigure the
application or insecure it by providing the run as administrator.
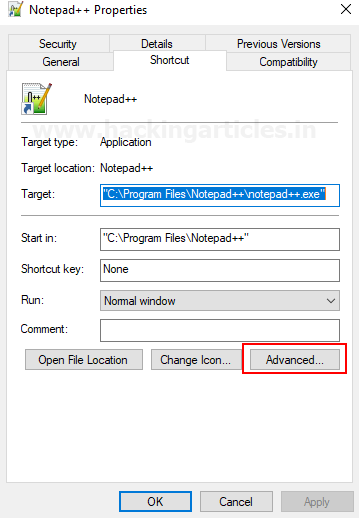
Right click on the Notepad++ icon and click on the
properties to edit advance settings.
Edit the Notepad++ properties just by click on advanced and
then ok, by default it will display some of the information of Notepad++
properties as mentioned in the following screenshot.
In the next window of advanced properties, there is an option
to run the application as an administrator. Just tick the option and click on
OK. Now whenever we will execute the Notepad++ automatically it will run as
administrator.
Abusing Insecure GUI
Application
After enumerate some time on
windows applications, we found that Notepad++ application has a feature that
allow us to open file, short key to open file is CTRL+O or by navigate to option
File then go to open.
Note: In lab set up we had already granted the permission to run as
administrator, whenever we execute the Notepad++.
Next open prompt, will allow us to run a binary with same
privilege escalation same as Notepad++ process.
Just by entering the cmd exe in the navigating bar it will open
command prompt.
Now,Command prompt will open with the Notepad++‘s
administrator privileges. The following command will display all the privileges
name, description and enabled and disabled features
Whoami /priv
If it will allow operations like to open a command prompt or
to run executable with the high privileges then it will allow to escalate the
privileges.
This demonstrates that admin user “ignite” does not have
same privileges as Notepad++ application that runs as an administrator .Just compare
the first and last screenshot for the better understanding. We will
characterize this as privilege escalation even though we can now add any new
user through command line. Finally demo user is successfully added and take the
advantage of insecure GUI application to exploit the privileges.
















0 comments:
Post a Comment