Today it is time to solve another challenge called "UltraTech". It is available at TryHackMe for penetration testing practice. The challenge is of medium difficulty if you have the right basic knowledge and are attentive to little details that are required in the enumeration process. The credit for making this machine goes to lp1. The breakdown of the Machine with the redacted flags is as follow:
Level: Medium
Penetration Testing Methodology
·
Network Scanning
o
Nmap Scan
·
Enumeration
o
Enumerating REST API
o
Enumerating Web Application
o
Directory Bruteforce using dirb
o
Detecting Remote Code Execution
·
Exploitation
o
Exploiting Remote Code
Execution
o
Reading the User Hash from
Database File
o
Decoding the Hash
o
Connecting using SSH
·
Privilege Escalation
o
Escaping Docker Environment
o
Getting Root Shell
Walkthrough
After Booting up the target machine from
the TryHackMe:
UltraTech CTF Page, an IP will be assigned to the machine and
will be visible on that page as well.
IP Address: 10.10.213.191
There are nine questions that are required
to complete this machine. You can find the questions as the answers are
discovered below.
Network Scanning
We will start a nmap scan with the -sC for
Default Scripts and -sV for Scanning Versions as well as Ping Scan to detect
any uncommon ports and services.
nmap -sC -sV -Pn -p- 10.10.213.191
Nmap scan was able to detect 3 service
running on the target machine. We have the FTP (21), SSH (22), HTTP (8081,
31331). Since we don’t have any credentials for the FTP service or SSH service,
let’s start enumeration from HTTP Service.
Q.1. Which software is using the port
8081?
Node.js
Q.2. Which other non-standard port is
used?
31331
Q.3. Which software using this port?
Apache
Q.4. Which GNU/Linux distribution
seems to be used?
Ubuntu
Enumeration
We began enumeration of HTTP service from
the Node.js Express framework HTTP service running on port 8081. It reveals
that this is an API service. We have the name of the API as UltraTech API
v0.1.3.
http://10.10.213.191:8081/
Since this was an API, there must be a web
application that is pulling data from this API. We open the second HTTP service
running on the port 31331. We find our web application. It a stock web
application with a bunch of pages.
http://10.10.213.191:31331/
While we are enumerating the Web Application
manually, let’s run a Directory Bruteforce on the API using dirb. After running
for a while, it was able to extract two pages auth and ping.
dirb http://10.10.213.191:8081
Upon accessing the ping, we see that there
is a Handling Error as shown in the image below. Close inspection of the error
suggests that there is some parameter or variable missing. Since we don’t have
any documentations for the API, we will have to guess about that parameter.
Q.5. The software using the port 8080
is a REST api, how many of its routes are used by the web application?
2
http://10.10.213.191:8081/ping
Since, it is a ping service, we decided to
use the ip parameter with the loopback IP to check if it works. We were able to
run the ping command on the target machine from API.
http://10.10.213.191:8081/ping?ip=127.0.0.1
Exploitation
After trying different variants to run
another command through the ping command, we were able to run the ls command by
inserting the command inside the quotes [``]. We are able to see that there is
a SQL file inside the current directory.
Q.6. There is a database lying
around, what is its filename?
utech.db.sqlite
http://10.10.213.191:8081/ping?ip=`ls
-la`
We use the cat command inside the same
quotes to read the contents of the SQL database file. We were able to get
credentials for a user by the name of r00t. The credentials were however
encrypted. To be able to use those credentials, we need to decode them.
Q.7. What is the first user's
password hash?
################################
http://10.10.213.191:8081/ping?ip=`cat%20utech.db.sqlite`
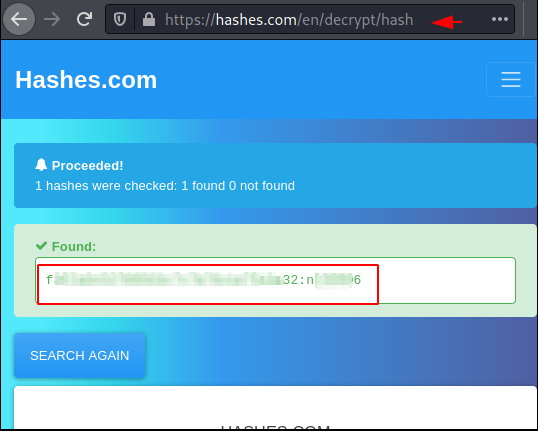
We take the credentials and try to decrypt
using online decrypter tool. We were able to read the password for the user
r00t.
Q.8. What is the password associated
with this hash?
#######
Now that we have the credentials for the
r00t user, we use them to connect to the target machine using the SSH service.
After getting the shell we ran the id command to find that we are inside a
docker instance.
ssh r00t@10.10.213.191
id
Privilege Escalation
We will use the GTFOBIN to
elevate privileges on the target machine. It tells us that in order to get out
of the restricted environment of docker, we need to spawn an interactive shell
inside the docker.
We run the script directly from the
GTFOBIN. It gave us the error that it was unable to find the alpine image. We
use the docker ps -a command to get the images that are on this docker
instance. We see that we have the image by the name of bash. After replacing
the image name from alpine to bash in the command, we ran the command gain to
ding that we are able to get the root access. We use the cat command to read
the private key for the root user as per the requirement for the conclusion of
this machine.
Q.9. What are the first 9 characters
of the root user's private SSH key?
#########
docker run -v /:/mnt --rm -it alpine
chroot /mnt sh
docker ps -a
docker run -v /:/mnt --rm -it bash
chroot /mnt sh
whoami
cat /root/.ssh/id_rsa





















0 comments:
Post a Comment