It's very hard for a bug bounty hunter or a web application pentester to remember all the codes or to search for different payloads by searching it over google. So, what if we can get all the payload in one place so that you don’t have to hop from one site to another? For that, we have got a great extension called Hacktool that provides us with the cheat sheet that is very useful in performing web penetration testing. So, let’s start to explore all the functionalities that are provided by this extension.
Table of
Contents
·
Configuring the Extension
·
Exploring Hacktool extension
o Reverse
Shell
o Php
Reverse Shell
o TTY
Spawn Shell
o Useful
Linux Commands
o PowerShell
Handy Commands
o File
Transfer
o Local
File Inclusion
o Cross-Site
Scripting
o SQL
Injection
o Base64
Encoder/Decoder
o Hash
Generator
o URL
Encoder/Decoder
o Hexadecimal
Encoder/Decoder
o Template
Injection
o Exploit
Feed RSS
·
Conclusion
Configuring the Plugin
Hacktool extension is available for both Google Chrome
and Mozilla Firefox. You can simply visit their extension website or add on
store of the browser and search for hacktool over there to add this extension to
your browser. Let us get this plugin over our browser. For Firefox, visit the link
and then click on add to Firefox button:
You will get a prompt
to add that extension to Firefox just press the Add button
After this, you will
see that extension has been added to the firefox.
Similarly, you can get this extension on your google
chrome by clicking here.
If you are interested in viewing its source code then click here.
Exploring the Hacktool extension
There are various services provided by this extension.
When you open up the extension you will see that there are various options
present on the left-hand side of the extension. We will look for which of these
can be useful and when.
Functionalities provided are:
·
Reverse Shell
·
Php Reverse Shell
·
TTY Spawn Shell
·
Useful Linux Command
·
PowerShell Handy Commands
·
File Transfer
·
Local File Inclusion
·
Cross-Site Scripting
·
SQL Injection
·
Base64 Encoder/Decoder
·
Hash Generator
·
URL Encoder/Decoder
·
Hexadecimal Encoder/Decoder
·
Template Injection
·
Exploit Feed RSS
Reverse Shell
When you will open the extension, you will be presented
with the Reverse Shell. In this, there are various reverse shells
present for different systems. You can use the payload based on the language
used by the webpage or by the OS used by its server.
Let’s now see how we can use an exploit to get a reverse
shell of Parrot OS machine on a kali machine.
In this, I have entered kali machines IP and port which
we will be using for listening to get the reverse shell. We will copy this bash
command which I will paste in my parrot OS machine. First, let's start a Netcat
listener on kali machine.
Now, our Netcat listener is up. We will be pasting out reverse shell on Parrot OS Terminal and press enter.
Let’s now have a look at our Netcat listener. We see that
we have successfully obtained parrot OS shell on kali machine.
Php Reverse Shell
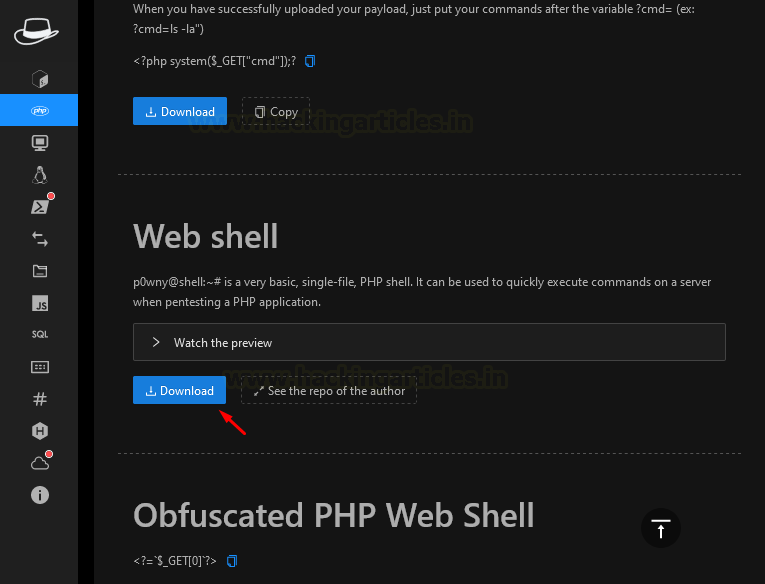
Second option present in hacktool is Php Reverse Shell. It's an important option as most of the server’s support PHP and if there is unrestricted file upload present then you can upload your PHP reverse shell. Using this shell, you can get its terminal on your pc from where you can get crucial information out of it. Let us have a look at how we can use it for a real attack.
Boot your bWAPP vulnerable application and navigate to
the unrestricted file upload section keeping the security level set to low.
Now we will download a payload from PHP reverse shell
option by setting our machine’s IP and port on which we will be listening.
Then we will download the Pentestmonkey’s reverse shell
in our PC and save the file as can be seen in the below image.
Now we will start to listen on the port we specified
using Netcat on my Kali Linux machine.
Now we will browse our shell and click on upload
After the file is uploaded, we will have to click on here
as shown in the below image which will pop up a new tab.
Now we will get a reverse shell in our kali machine and
we will type w to view users and we can be sure that we got a reverse
shell of bWAPP in our machine.
We have one more payload named Web Shell we will download
it in our pc.
After the PHP file is downloaded upload the shell as we
did in the above case and then we will click here after uploading and a
new tab will open up in which we got a shell. We will type w to print
users of the shell.
TTY Spawn Shell
TTY stands for TeleTypewriter. It will happen many
times that you got a shell but you are not able to interact with it or you are
facing issue in interacting with it, so for that purpose, we can spawn a TTY
shell to interact with the shell more easily. Let's see how we can obtain TTY
shell on our already captured parrot shell.
First, we will copy our payload from the extension
Now we will paste this command in our reverse shell and
we will see that we have got a TTY shell successfully.
Useful Linux Command
When you have got a reverse shell or you found out that OS command injection is possible and the server is Linux then you can use this extension which provides us with useful Linux commands that can help in gaining some crucial information.
Let us have look over some useful Linux command for
attacking. So, turn on your bWAPP again and choose OS Command injection with
security level set to low.
We will get the page as below and we will click on lookup
to see what is the normal output:
Now we will check if server is Linux or not for which we
will be typing “;ls”
After pressing the lookup button, we found out that we
were able to list out the files that are present on the server. So by this, we
can see that the command after metacharacter which is “;” in this case
is executed. So this tells us that OS command injection is possible and the server
is using Linux.
By this, we are clear that OS command injection is
possible. So, we will be using some Linux commands to get information about the
host. We will copy the below command.
We will now enter the command as ;cat /etc/*-release and click on Lookup,
and we will notice that we got on what version this web application is
operating on.
Now let's try to get the kernel version by copying the
below command.
We will be inserting the command in the field as ;uname
-a and click on Lookup and get the following output from it.
PowerShell Handy Commands
Like Linux commands there is also an option for Windows PowerShell commands. If you got the control of the CMD then you can use this option to take out crucial information like system info, WLAN enumeration, HTTP download, active directory enumeration. In short, it contains all the commands that you will require to dig deep into the PowerShell to get crucial information.
File transfer
There are various methods present that can be used to
upload or download a file to the remote machine. Let see an example of this
Let us try to send a file from one machine to another
machine. First, we will set the IP and the port number of the receiving
machine. In this example, I will be transferring file from parrot machine to
kali machine so we will be entering the IP address of kali machine and its port
on which we will be receiving the file and also the file name that we will be
transferring which is ignite.txt in this case. Let’s first see what is the file
content of ignite.txt.
Then we will finalize our field in the extension.
Now we will copy Netcat commands as we will be using Netcat
in this demonstration.
We will do ls to check if there is any file present or
not and then save the file as ignite.txt so, for that, we have replaced file_saved
with ignite.txt in our kali machine.
We will be pasting our payload for transferring ignite.txt
using Netcat which is on my Parrot OS machine.
We will see on our kali machine that a connection is
established and we will notice that we got a file named ignite.txt and
when we view its content it is same as the original file on parrot machine,
Local File Inclusion
Using Local File Inclusion vulnerability an attacker tries to trick web-application by including files that are present locally in the server. This vulnerability exists when its PHP file contains functions such as “include”, “require”, “include_once”, “require_once”. We will be now seeing LFI exploitation using hacktool. Let us do a hands-on of LFI for which we need bWAPP with Remote & Local File Inclusion (RFI/LFI) of which security level is set low.
We will click on Go and then we will observe in
the URL that we got language as an exploitable field. Language is an
exploitable field as the exact PHP file was reflected in the URL which gave us
an idea that we can trick the web-application to show us some internal files
present in its server.
We will pick a payload
from LFI in the option present in Hacktool.
Now we will copy-paste this in the URL as shown below and
hit enter and will get the result as follows. In the field, we got hostname of
the server which is bee-box in this case.
Cross-Site Scripting
Cross-Site Scripting
often abbreviated as “XSS” is a client-side code injection
attack where malicious scripts are injected into trusted websites.
XSS occurs over in those web-applications where the input-parameters are not properly sanitized or
validated which thus allows an attacker to send malicious Javascript codes over
to a different end-user. So, HackTool provides us with an option to exploit
this vulnerability.
Let us perform exploitation on XSS-Reflected (GET) on our
bWAPP application with security level set to medium.
We will type the first name and last name and then will
click on Go and observe the default output.
Now let’s pick up a payload from Hacktool
Now we will paste this payload in First name field while
keeping the last name field unchanged, we will press Go
We will observe that we got a popup saying XSS.
SQL Injection
SQL is a language that is used to communicate to the
database. SQL injection is injecting SQL queries in a web-application to trick
them to reveal the data that is stored in the database. In this extension,
there is an option for SQL injection.
Now let us have a look at how we can use hacktool for
SQLi.
We will be using vulnweb for this purpose. You can access
this lab by clicking over here
Now we will select a payload from Hacktool plugin as can
be seen in the following image.
Now we will paste this payload into username and password
field and then we will press Login
Hurray!!! We have successfully logged in to the account.
Base64 Encoder/Decoder
You will find out that there are many places where base64
encoding is used or takes entry only in base64 encoding. This extension has
inbuilt base64 encoder and decoder to help you encode or decode a string right away
instead of going to other tools.
Hash Generator
Hashes are usually used to check if the file that we got
is same or is altered. It helps in maintaining the integrity of a file. This
extension provides us to check MD5 hashes, SHA256 hashes, SHA1 hashes, SHA512
hashes and SM3 hashes.
URL Encoder/Decoder
URL encoding is used in many places nowadays. You can
decode URL encoded string to a string or encode a string to encoded string
using this option.
Hexadecimal Encoder/Decoder
This extension also provides option to convert
hexadecimal string to a normal string or from normal string to hexadecimal
string.
Template injection (SSTI)
This extension has an option for template injection.
Template injection that is present in this extension is for Flask/Django
websites only. Template injection is injecting a user inputs unsafely inside
the template being used by the website. Unsafe input in the template results in
Server-Side Template Injection.
Exploit feed RSS
It contains the websites from where you can search for
vulnerabilities, exploits for services, security article, etc. so that you can
target the attack more effectively.
Conclusion
This extension provides us with the cheat sheets of
various web application attacks possible. Along with the cheat sheets it
provides us with the shells that you can use without even knowing what's inside
that payload to carry out the attack. This tool is helpful if we are testing at
the basic level but if we will be using this extension for advanced level then
you should have some internal knowledge that how it is working and what you
need to change to make it work. It also provides various encoders and decoders
that will help you encode and decode the strings using that extension only
without going to any other site or using any other tool.

























































0 comments:
Post a Comment