In the previous article, we have discussed about of the Lab setup of Thick Client: DVTA
You can simply take
a walkthrough by visiting here: - Thick
Client Pentest Lab Setup: DVTA
In this article, we
are going to discuss about how can we configure the DVTA application to connect
to our server
For this, I’m going
to use one single window 10 instances for the entire setup. That means both the
DVTA client as well as the SQL server are going to run on the same machine.
You can configure
the DVTA client and SQL server on Different Window 10 instances.
Table of Content
·
Prerequisites
·
Download Links &
Credentials
·
Download and install the DVTA
application
·
Reversing and Modifying the
original DVTA application
·
Configure & log in to the
Modified DVTA application
Prerequisites
·
Good knowledge of C# (C Sharp)
programming knowledge.
·
A bit of Reverse Engineering
knowledge.
Download Links & Credentials
DVTA application: - https://mega.nz/file/rPJQ0LTL#CuhQ9HBeEIKHa67jbITFQbt49FZalugWlRe5A33O6y4
DnSpy application: - https://github.com/dnSpy/dnSpy/releases
Database users and password: -
User Password
1.
vijay vijay
2.
raj raj
3.
admin admin123
Download and install the DVTA application
You can directly download the DVTA
application by using this link
https://mega.nz/file/rPJQ0LTL#CuhQ9HBeEIKHa67jbITFQbt49FZalugWlRe5A33O6y4
when the download completes extract it
into a new folder which similarly looks like this as shown in the image below.
Alright, this is the Release File that
we have gotten for the testing. If you see there are a couple of file inside of
the Release folder and the main application here is the one with the Red icon
named “DVTA.exe”
So, let’s give a double click to the
DVTA.exe and run it.
Once that done you should see a prompt window
something like this. If you notice the bottom part of the prompt window, we can
configure the server here.
The original DVTA application doesn’t
have this feature and the IP address is hardcoded. The problem with that is we
need to have a server with the exact same IP that is hardcoded in the
application. For this, all we need to compile the source code to modify the
application somehow so that it points or redirects to our server.
Now, our main Task before configuring
the server is to enable the “configure Server” button so that it can
talk to our server.
This requires a bit of Reversing
knowledge…. And this going to be fun.
Reversing and Modifying the original DVTA application
Now let’s see how we can enable the “configure
server button”.
Before we enable this button let’s
think a while what are the situations where we came across this kind of
disabled buttons in the client applications in the real world when we do
pentesting. There are cases where a user logs In and some menus are disabled for
him. For instance, he is the maker and he can’t have checker menus so some
developers disable them in the client assuming that the user cannot enable them
and these disabled menus can be easily enabled in C sharp.net applications.
Now let’s see how we can do that. First
of all, simply take a copy of the Extracted DVTA Release folder for the case if
we did something wrong or messed up with codes so simply, we can start from
fresh without downloading it again. To enable the “configure server” button
we’re going to use a tool called dnSpy. You can download it directly by
following this link: - https://github.com/dnSpy/dnSpy/releases
Download the latest version from the
release section.
When the download is complete extract it
into a new folder.
Once the extraction is complete you
should see two versions of dnSpy one is 32-bit and the other one 64-bit. We are
going to use the 32-bit version because our target application is 32-bit.
So, if you see in the below image the
one which is having dnSpy-x86 is the 32-bit version, and the other one that
just says the dnSpy is the 64-bit version.
So, without wasting time Quickly open up
“dnSpy-x86” by giving it a double click and simply run it
When the dnSpy application started open
up the DVTA application by navigating to File > open
And go to the Release folder of the DVTA
application and choose DVTA.exe.
So, this is the main application that
we’re going to modify.
Now, our main task is to find out the
exact location of the button which is disabled and then patch the binary in a
way that it’s going to be enabled
On the left side menu, click on the DVTA
and expand the DVTA.exe. Once it expanded select DVTA. Now, If you see, there
seems to be a couple of here within the DVTA application. Basically, these are
C sharp files in the source code. If you notice above when you open the DVTA application,
it open’s up the login page of DVTA and on that page the bottom part has
the “configure server” button. So, this is what we’re interested in.
Now, without wasting time click on Login
and it will start automatically decompiling the source code for us.
Now, it seems very interesting and it’s
pretty easy for us to understand the entire source code of what this
application is doing here. When you scroll down to the source code you can find
there is a condition that is looking for a method called “is server
configured” when you click on this it will see where the definition is and
when you see the definition it is always returning “false” and what
happens if its return the value True.
Let’s see…
It is going to show the particular
message “MessageBox.Show(“This application is usable only after configuring
the server”) That means this block is never
going to execute because it is always “returning false”. So
what that means is “this.configserver.Enabled = False;” is the part
which is going to get executed always as highlighted by the right arrow In the below image
If you noticed that is all the source
code is are in C sharp.
Let’s take a look at the IL version of
this source code. IL is an intermediate language. This is similar to the old
assembly language in the C programming world. You can convert the source code
into the IL by navigating to a drop-down box nearby the start icon. If you
compare the C sharp code or IL code basically, they are doing the same thing.
As we have seen earlier “config server”
is a button that you can easily find here. It’s a button of “class
[system.windows.Forms]System.Windows.Forms.Button “ after this particular
line there seems to be a call to “System.Windows.Forms.Control” and set
Enabled method is being called and this Set_Enabled method is taking a Boolean
value which can be true or false. If you see there seems to be a value which is
ldc.i4.0 and then if you hover over your mouse on Set_Enabled(bool) it pushes
the integer value of 0 onto the evaluation stack as an int 32 and probably
that’s the reason why the button is always disabled because this value is being
pushed under the stack as an argument and set enable is always set to false.
Now, give a right-click to the value of
ldc.i4.0 and “Edit the IL instructions” as shown below
Now, it will open up another prompt and
give a right-click to the value ldc.14.0 and further then select ldc.i4.1
instead of 0 and hit ok as shown below
Now save the configuration by navigating
to the File > Save Module
Now save this file in the same place
where your original DVTA exist so that it can replace the original DVTA.exe as
shown below
Now we can close the dnSpy application
and open up the Modified application DVTA.exe by going to the same directory.
Configure
& log in to the Modified DVTA application
Hurray…as you can see the “configure
server button is enabled
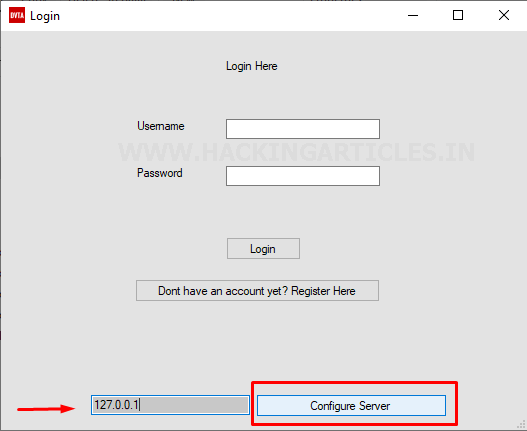
So, we’re all set to configure the
server. As I told you earlier, we are going to use the same server as the
database.
So, let’s enter “127.0.0.1” as
our server and click on “configure server”.
As you can see our server is
successfully configured.
Now, just to make sure everything is
fine come back to the directory of release folder of DVTA and give a double-tap
to the DVTA.exe XML configuration file which is just below the DVTA application
as shown below
This is basically a configuration file.
Give it a double tap and open the configuration file.
When you see the application settings you
can see that the Database server is “127.0.0.1/SQLExpress” and the “FTP
server is also configured to 127.0.0.1”.
Awesome… now we’re good with the
configuration.
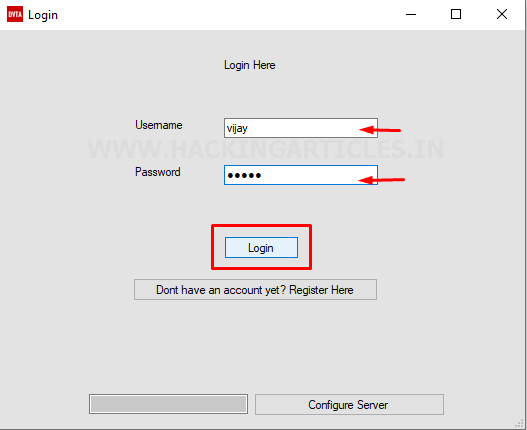
Now open the modified DVTA application
and log in as the user “vijay” that we created previously on the SQL
Server setup.
Great, as we can see we have
successfully logged in to the application
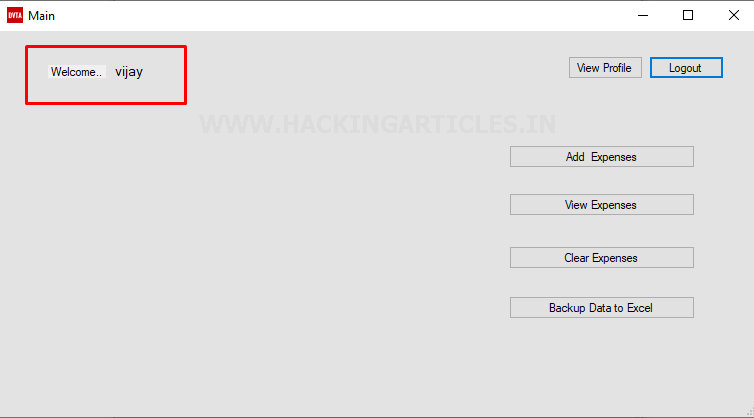
Let’s also verify another user for
example admin and check which rights admin have
Great, as we can see everything works fine
and we’re successfully logged in as user admin.
Congratulations.
Now if you have been done until here
then you are all set with your Damn Vulnerable Thick Client Application setup.
From the next part, we are going to
systematically pentesting this application for various issues.
One most important thing “you can use
all these steps from here as a checklist for your real-world Thick Client
Penetration Testing Engagements”.






























0 comments:
Post a Comment