Today we are going to solve another boot2root challenge called "Tomato: 1". It's available at VulnHub for penetration testing and you can download it from here.
The merit of making this lab is due to
SunCSR Team. Let's start and learn
how to break it down successfully.
Level: Intermediate
Penetration Testing Methodology
Reconnaissance
§
Netdiscover
§
Nmap
Enumeration
§ Dirsearch
Exploiting
- RCE with LFI and SSH
Log Poisoning
Privilege
Escalation
§
Abuse kernel exploit CVE-2017-16995
§
Capture the flag
Walkthrough
Reconnaissance
We are looking for the
machine with netdiscover
$ netdiscover -i ethX
So,
let's start by running map to all ports with OS detection, software versions,
scripts and traceroute.
$ nmap -A –p- 192.168.10.179
Enumeration
We
access the port 80 web service and
find a single page with an image of a tomato. After checking the image with
several stego tools, we did not find anything that could be useful. In the code
either.
In the 8888 port, we have an Nginx server protected with username and password.
We use dirsearch
with the "common"
dictionary and specify the most typical extensions.
We found the directory "/antibot_image/".
We checked the directory and found a "Directory listing”:
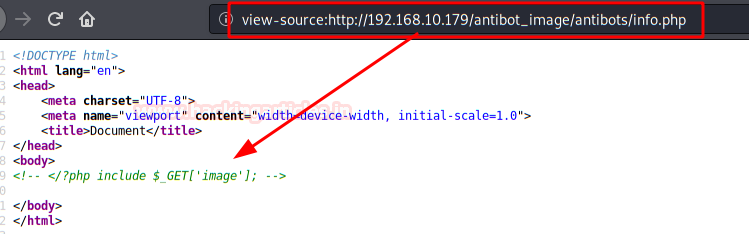
We check the files, we find an "info.php", besides showing us the system information, version,
etc.. It also includes a gift inside. (Possibly, this is the most complicated
part of the box).
This bug will allow us to
upload files via the URL. Let's do a proof of concept.
Indeed! The site is vulnerable to LFI (Local File Inclusion).
Exploiting
Since we can load files,
let's try to load log files, for example that of the SSH service.
Let's
login by SSH, in it we will change
the user by PHP code that will allow us to execute commands.
Perfect!
Let's do a proof of concept by sending a system command to check that it
actually commands.
We
see that by executing commands, we
repeat the steps, but this time we will insert a reverse shell to access the interior of the machine.
The
command in "plain text" will not work, so we must encode it in "URL-encode all characters" with Burp, being as follows.
We
put a listening netcat to port 443
and send the request from Burp.
We
will be inside the box, we will execute a couple of commands to have an
interactive shell.
If
we remember previously, in the 8888
service we were asked to authenticate the site by means of an .htpasswd.
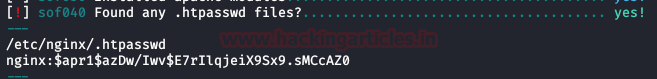
We
crack hash with John and the kaonashi dictionary, we get the password, but this
one will not be useful for any of the two users.
Privilege
Escalation (root)
This
time, we will not try to scale the user first, we have the advantage that the
system is not updated and the kernel is
vulnerable.
We
will use the following exploit that will allow us a privilege scale as root.
Exploit: https://www.exploit-db.com/exploits/45010
We
download the exploit to our machine, compile it and download it to the victim
machine.
Now
we will give it execution permissions and we execute it, this will return a
prompt as root and we will read the file "proof.txt".
Author: David Utón is Penetration Tester and security auditor for Web
applications, perimeter networks, internal and industrial corporate
infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.


























0 comments:
Post a Comment