Subscribe to:
Post Comments (Atom)
skip to main |
skip to sidebar
Labels
- Batch File tricks (8)
- crytography (3)
- CTF (100)
- Cyber Forensics Tools (56)
- DLL Hacking (6)
- footprinting (2)
- Google Hacking (1)
- Hacking Tools (12)
- Kali Linux (370)
- others (5)
- Penetration Testing (1348)
- redteam (9)
- Stegnography (7)
- Windows Hacking (6)
Popular Posts
-
Introduction Shellcodes are machine instructions that are used as a payload in the exploitation of a vulnerability. An exploit is a small ...
-
While wrting Applocker bypass series , we found a new tool which was especially design for bypassing whitelisting application. So Idecid...
-
Abusing AD-DACL: ReadGMSAPassword ReadGMSAPassword Attack is a technique where attackers abuse misconfigured Group Managed Service Account...
-
Pre2K (short for "Pre-Windows 2000") Active Directory misconfigurations often stem from overlooked legacy settings in Windows en...
-
In this post, we explore the exploitation of Discretionary Access Control Lists (DACL) using the Generic ALL permission in Active Director...
-
In this post, we explore the exploitation technique known as the Shadow Credentials attack. This attack leverages the mismanagement or explo...
-
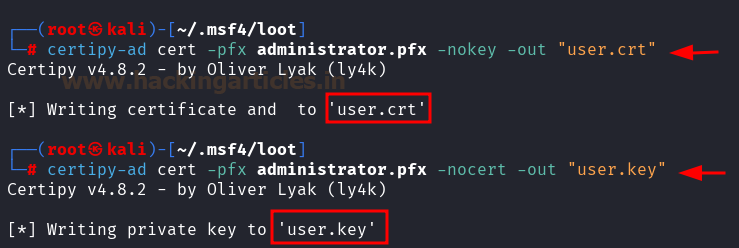
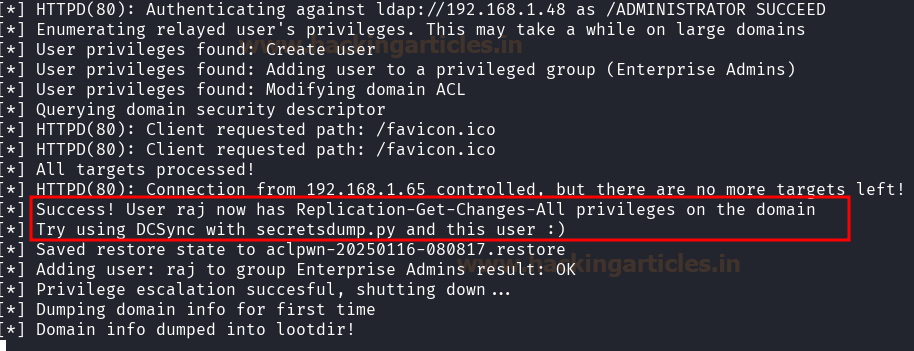
The AD CS (Active Directory Certificate Services) certificate template is a predefined configuration in Microsoft AD CS that defines the ty...
-
NetExec (nxc) is a powerful network exploitation tool developed as a modern successor to CrackMapExec (CME), which was widely used by penetr...
-
Active Directory (AD) penetration testing is an essential part of the security assessment of enterprise networks. The Netexec tool offers a...
































0 comments:
Post a Comment