Hello
friends!! Today we are going to discuss “Payload Processing” option of Burpsuite
which is advance functionality comes under Intruder
Tab for making brute force attack.
Payload
Processing
Payload
Processing can be defined as when payloads are generated using payload types, they can be further manipulated or filtered using various processing rules and payload encoding.
These rules are
defined to perform various processing task on each payload before it is used.
These rules are executed in a sequence, and they can be used to help debug any
problem with the configuration. Payload processing rules are useful in
situations where you need to generate different payloads, or where we want to
wrap payloads within a wider structure or encoding scheme.
There are 12
types of payload processing rules available:
- Add prefix
- Add suffix
- Match / Replace
- Substring
- Reverse substring
- Modify case
- Encode
- Decode
- Hash
- Add raw payload
- Skip if matches regex
- Invoke Burp
extension
Let's
start!!
Add
Prefix
This processing rule adds up a prefix
before the payload.
First, we have
intercepted the request of the login page in the Bwapp LAB, where we
have given default username and wrong password. Then click on login, the burp
suite will capture the request of the login page in the intercept tab.Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted password and follow the given below step for selecting payload position.
·
Press on the Clear button given at right of window
frame.
·
Now we will select the fields
where we want to attack and i.e. the password filed and click on Add button.
·
Choose the Attack type as sniper.
- In the given below image we have selected password that means we will need one dictionary files for password.
Before executing the attack we have added a payload processing rule to the payload type which is Add Prefix and we have given an input string “hash” which is added as a prefix with every input strings in the dictionary, as shown in the result window of the attack.
Sit back and relax because now the burp suite will do its work, match the password which will give you the correct password. The moment it will find the correct value, it will change the value of length as shown in the image.
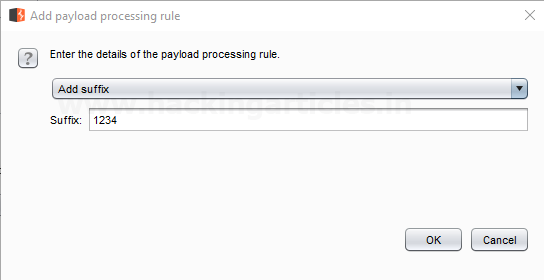
Add Suffix
This processing rule adds up a suffix
after the payload.
First, we have
intercepted the request of the login page in the Bwapp LAB, where we
have given default username and wrong password. Then click on login, the burp
suite will capture the request of the login page in the intercept tab.Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted password and follow the given below step for selecting payload position.
·
Press on the Clear button given at right of window
frame.
·
Now we will select the fields
where we want to attack and i.e. the password filed and click on Add button.
·
Choose the Attack type as sniper.
In
the given below image we have selected password that means we will need
one dictionary files for password.
Now click on payloads option after selecting payload position. Then select the Payload type as Simple list,
where we have added a dictionary by clicking on Load button. We
can either load the dictionary or we can manually add input strings using the Add button in the payload options as shown in the image.
Before executing the attack we have added a payload processing rule to the payload
type which is Add Suffix and we have
given an input string “1234” which is added as a suffix with every input strings in the dictionary, as shown in the result window of the attack. Sit back and relax because now the burp suite will do its work, match the password which will give you the correct password. The moment it will find the correct value, it will change the value of length as shown in the image.
Match / Replace
This processing rule is used to replace any part of the payload that match a specific regular expression, with a string.
Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted password and follow the given below step for selecting payload position.
·
Press on the Clear button given at right of window
frame.
·
Now we will select the fields
where we want to attack and i.e. the password filed and click on Add button.
·
Choose the Attack type as sniper.
- In the given below image we have selected password that means we will need one dictionary files for password.
Before executing the attack we have added a payload processing rule to the payload type which is Match / Replace and we have given an input “9870” in the Match Regex which will match the input given with the input strings in the dictionary, if the there is a certain match than it will replace it with the input “1234” given in the Replace with as shown in the image.
Sit back and relax because now the burp suite will do its work, match the password which will give you the correct password. The moment it will find the correct value, it will change the value of length as shown in the image.
Substring
This processing rule is used to extracts a sub-portion of the payload, starting from a specified offset up to a specified length. Here the offset and length are counted from the front.
Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted password and follow the given below step for selecting payload position.
·
Press on the Clear button given at right of window
frame.
·
Now we will select the fields
where we want to attack and i.e. the password filed and click on Add button.
·
Choose the Attack type as sniper.
- In the given below image we have selected password that means we will need one dictionary files for password.
Before executing the attack we have added a payload processing rule to the payload type which is Substring and we have given an input “0” in From option which specifies the offset and a input “3” in the Length option which specifies the length of the input strings.
For example if “password” is word in dictionary and we had applied above filter so it will place alphabet p = 0; a = 1; s = 2 and s = 3 hence it will read only pass from whole word “password”.
The length specified will select only those inputs having the specific length and other lower or greater length inputs are discarded as shown in the result window of the attack.
Sit back and relax because now the burp suite will do its work, match the password which will give you the correct password. The moment it will find the correct value, it will change the value of length as shown in the image.
Reverse Substring
This processing rule is used as a substring rule, but the end offset is specified counting backwards from the end of the payload, and the length is counted backwards from the end offset.
Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted password and follow the given below step for selecting payload position.
·
Press on the Clear button given at right of window
frame.
·
Now we will select the fields
where we want to attack and i.e. the password filed and click on Add button.
·
Choose the Attack type as sniper.
- In the
given below image we have selected password that means we will need
one dictionary files for password.
Before executing the attack we have added a payload processing rule to the payload type which is Reverse Substring and we have given an input “2” in From option which specifies the offset and an input “9” in the Length option which specifies the length of the input strings and they are similar to the Substring rule but it works from backwards of a offset and the length is counted backwards where the offset ends.
For example if “admin123456” is word in dictionary and we had applied above filter so it will place alphabet 4 = 0; 3 = 1 ; 2 = 2 ; 1 = 3 ; n = 4 ; i = 5 ; m = 6 ; d = 7 ; d = 8 ; a = 9 hence it will read only ‘admin1234’ from whole word “admin123456”.
The length specified will select only those inputs having the specific length and other lower or greater length inputs are discarded as shown in the result window of the attack.
Sit back and relax because now the burp suite will do its work, match the password which will give you the correct password. The moment it will find the correct value, it will change the value of length as shown in the image.
Use this combination of username and password for login to verify your brute force attack for correct password.
Modify Case
This processing rule can be used to modify the case of the payload, if needed. This rule has the same options available for the Case Modification payload type which we have explained in Part-1 of the Payload types article.
Source:
portswigger.net



































0 comments:
Post a Comment