Hello Friends!! In our previous article part1 we had
discussed how to perform brute force attack on any web application server for
making unauthorized login into it using some Payload of Burpsuite. In part 2
articles you will learn more about brute force attack with help of remaining BurpSuite
payloads that might be helpful in other situation.
Let’s
Start!!
Character Substitution
This type of payload allows to configure a list of strings and
apply various character substitutions to each item. This type of payload is
useful in password guessing attacks and generating common variations on
dictionary words. The UI of this payload allows you to configure a number of character substitutions. For each item, it will generate a number of payloads, which include all permutations of substituted characters according to the defined substitutions.
For example, the default substitution rules states (which include e > 4 and r > 5), the item "Raj Chandel" will generate the following payloads:
raj chandel
5aj chandel
raj chand4l
5aj chand4l
First, we have intercepted the request
of the login page in the DVWA LAB,
where we have given a default username and wrong password. Then click on login,
the burp suite will capture the request of the login page in the intercept tab.
Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted password and follow the given below step for selecting payload position.
·
Press on the Clear button given at right of window
frame.
·
Now we will select the fields
where we want to attack and i.e. the password filed and click on Add button.
·
Choose the Attack type as sniper.
- In the given below
image we have selected password that means we will need one
dictionary files for password.
Now click on payloads option after selecting payload
position. Here we can add a dictionary by clicking on Load option or we
can manually add Strings by clicking on the Add option.
Now we have substituted 4>a , 5>s , 9>o as per our requirements to match the password and we have added the input as p445w9rd using the Add option which will substitute the character's according to the Defined substitution as shown in the image.
Start Attack in the Intruder menu as shown in the image.
Sit back and relax because now the burp suite will do its work, match the password and will give you the correct password. The moment it will find the correct value, it will change the value of length as shown.
And to confirm the password matched, we will give the matched password in the DVWA LAB login page. We will see a message “Welcome to the password protected area admin” which shows are success in the character substitution payload attack.
Copy Other Payload
This is a type of payload which can copy the value of the current payload to another payload position. It is very useful for attack types that have multiple payload sets such as cluster bomb, pitch fork and battering ram. This payload type can be useful in various situations, for example:
First, we have
intercepted the request of the login page in the Bwapp LAB, where we
have given wrong username and password. Then click on login, the burp suite
will capture the request of the login page in the intercept tab.
Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted username and password and follow the given below step for selecting payload position.
Now click on payloads option
after selecting payload position, here we need to add a dictionary which will
use for both payload set. Then select the Payload type as Simple list for Payload Set '1'
which will attack at the username field.
Now to attack at the password field we will select Payload type as Copy other payload for Payload Set '2' because we want to attack the same payload type at payload set 2 which will copy the dictionary given for payload set 1 to attack.
Select Start Attack in the Intruder menu as shown in the image.
Sit back and relax because now the burp suite will do its work, match the username and password which will give you the correct username and password. The moment it will find the correct value, it will change the value of length as shown in the image.
And to confirm the password matched, you can give the matched password in the BWAPP LAB login page.
Username Generator
This type of payload allows you to set up a list of names or email addresses, and can produce usernames from given specific schemes.
For example, Let's take a username "raj chandel" which can give results in up to 115 possible usernames, some combination are as follows :
rajchandel
raj.chandel
chandelraj
chandel.raj
chandel
raj
rajc
etc...
This type of payload is useful to target at a specific user, where you do not know the username or email address scheme of the user which is being used in a specific application.
First, we have intercepted the request of the login page in the Bwapp LAB, where we have given wrong username and password. Then click on login , the burp suite will capture the request of the login page in the intercept tab.
Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted username and password and follow the given below step for selecting payload position.
Then select the Payload
type as “Username Generator” for
Payload Set '1' which will attack at
the username field, we have a given input string “raj chandel” by using the Add option as shown in the image, which
will use different permutations on that input string given to match the correct
username.
Now to attack at the password field we will select Payload type as Simple list for Payload Set '2' for which we have added a dictionary manually created by us by using the Load option.
Select Start Attack in the Intruder menu as shown in the image.
Sit back and relax because now the burp suite will do its work, match the username and password which will give you the correct username and password. The moment it will find the correct value, it will change the value of length as shown in the image.
Repeat the same to intercept the request of the login page in the Bwapp LAB, where we have given wrong username and password. Then click on login, the burp suite will capture the request of the login page in the intercept tab.
Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted username and password and follow the given below step for selecting payload position.
Now to attack at the password field we will select Payload type as Dates for Payload Set '2'
because we are guessing the user might have its birth date or any other date
as a password.
After this we have set the inputs for Payload set '2' in the fields given in the payload options such as FROM, TO, STEP and FORMAT as shown in the image.
Now Select Start
Attack in the Intruder menu for
brute force attack.
Sit back and relax because now the burp suite will do its work, match the username and password which will give you the correct username and password. The moment it will find the correct value, it will change the value of length as shown in the image.
Now we have substituted 4>a , 5>s , 9>o as per our requirements to match the password and we have added the input as p445w9rd using the Add option which will substitute the character's according to the Defined substitution as shown in the image.
Start Attack in the Intruder menu as shown in the image.
Sit back and relax because now the burp suite will do its work, match the password and will give you the correct password. The moment it will find the correct value, it will change the value of length as shown.
And to confirm the password matched, we will give the matched password in the DVWA LAB login page. We will see a message “Welcome to the password protected area admin” which shows are success in the character substitution payload attack.
Copy Other Payload
This is a type of payload which can copy the value of the current payload to another payload position. It is very useful for attack types that have multiple payload sets such as cluster bomb, pitch fork and battering ram. This payload type can be useful in various situations, for example:
·
Suppose we are using two
different parameters and we want to attack at two different fields, therefore
we can set different “payload types” at multiple “payload sets” inside
burpsuite payload configuration as per our attack type as it allows us to
simply use the same dictionary for both payload that we have set at particular
position by giving the position of the payload we want to copy. It will execute
the complete payload which is set at a specific position.
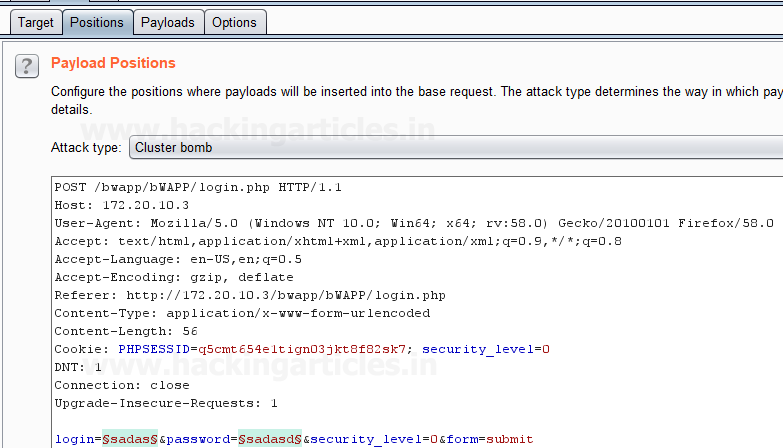
Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted username and password and follow the given below step for selecting payload position.
·
Press on the Clear button given at right of window
frame.
·
Now we will select the fields
where we want to attack which is the username and password and click on Add button.
·
Choose the Attack type as Cluster Bomb.
·
In the given
below image we have selected username and password that means we will need two
dictionary files i.e. one for username and second for password.
Now to attack at the password field we will select Payload type as Copy other payload for Payload Set '2' because we want to attack the same payload type at payload set 2 which will copy the dictionary given for payload set 1 to attack.
Select Start Attack in the Intruder menu as shown in the image.
Sit back and relax because now the burp suite will do its work, match the username and password which will give you the correct username and password. The moment it will find the correct value, it will change the value of length as shown in the image.
And to confirm the password matched, you can give the matched password in the BWAPP LAB login page.
Username Generator
This type of payload allows you to set up a list of names or email addresses, and can produce usernames from given specific schemes.
For example, Let's take a username "raj chandel" which can give results in up to 115 possible usernames, some combination are as follows :
rajchandel
raj.chandel
chandelraj
chandel.raj
chandel
raj
rajc
etc...
This type of payload is useful to target at a specific user, where you do not know the username or email address scheme of the user which is being used in a specific application.
First, we have intercepted the request of the login page in the Bwapp LAB, where we have given wrong username and password. Then click on login , the burp suite will capture the request of the login page in the intercept tab.
Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted username and password and follow the given below step for selecting payload position.
·
Press on the Clear button given at right of window
frame.
·
Now we will select the fields
where we want to attack which is the username and password and click on Add button.
·
Choose the Attack type as Cluster Bomb.
·
In the given
below image we have selected username and password that means we will need two
dictionary files i.e. one for username and second for password.
Now to attack at the password field we will select Payload type as Simple list for Payload Set '2' for which we have added a dictionary manually created by us by using the Load option.
Select Start Attack in the Intruder menu as shown in the image.
Sit back and relax because now the burp suite will do its work, match the username and password which will give you the correct username and password. The moment it will find the correct value, it will change the value of length as shown in the image.
Dates
This type of
payload generates date payloads within a given range and in a specified format.
This type of payload is can be used in data mining or brute forcing.
For example it
can be used to guess a user's birth date, wedding date, anniversary date etc
which can be used to brute force the security questions for an application or
web applications, or it can used to brute force the password of user’s, where
user's uses dates as their password.
The following
options are available in this type of payload:
- From - This is said as the first date
which will be generated.
- To - This is said as the last date
which will be generated.
- Step - This is said as an increase
between sequential dates, days, weeks, months or years. It should be a
positive value.
- Format - This is said as the format in
which dates can be represented. we can select from different predefined
date formats, or we can make our own custom date format as per our
requirement. Some example of the date format are given below:
|
E
|
Mon
|
|
EEEE
|
Monday
|
|
D
|
2
|
|
dd
|
02
|
|
M
|
9
|
|
MM
|
09
|
Repeat the same to intercept the request of the login page in the Bwapp LAB, where we have given wrong username and password. Then click on login, the burp suite will capture the request of the login page in the intercept tab.
Send the captured request to the Intruder by clicking on the Action Tab and follow given below step. Now open the Intruder tab then select Positions tab and you can observe the highlighted username and password and follow the given below step for selecting payload position.
·
Press on the Clear button given at right of window
frame.
·
Now we will select the fields
where we want to attack which is the username and password and click on Add button.
·
Choose the Attack type as Cluster Bomb.
·
In the given
below image we have selected username and password that means we will need two
dictionary files i.e. one for username and second for password.
Then
select the Payload type as Simple list for Payload Set '1' which will attack at the username field where we
have given a dictionary as an input string as shown in given below image.
After this we have set the inputs for Payload set '2' in the fields given in the payload options such as FROM, TO, STEP and FORMAT as shown in the image.
Sit back and relax because now the burp suite will do its work, match the username and password which will give you the correct username and password. The moment it will find the correct value, it will change the value of length as shown in the image.





























0 comments:
Post a Comment