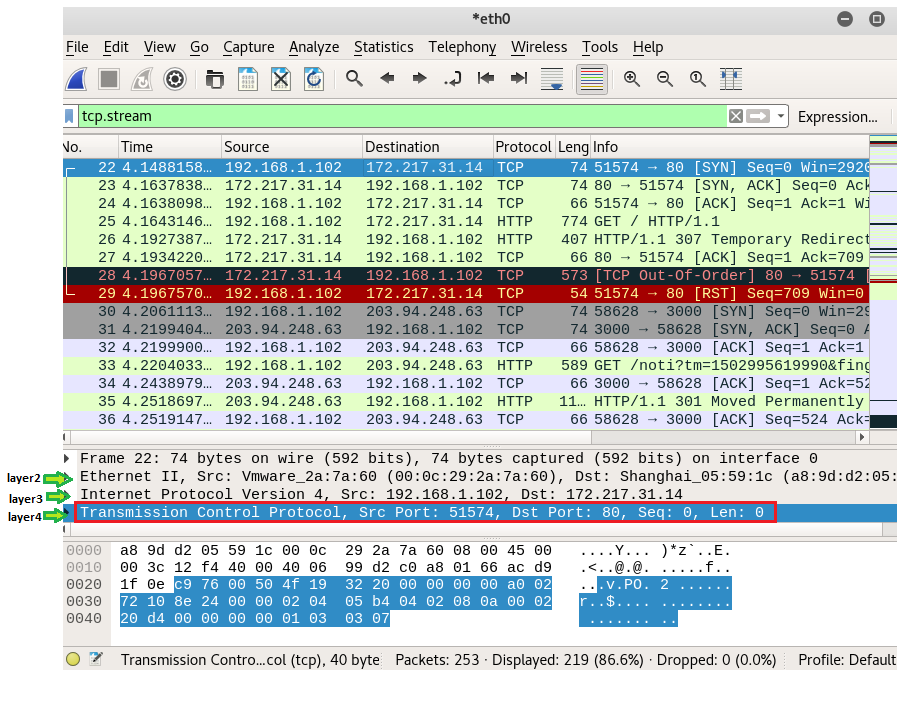
From given below image you can see we had sniffed the network in
order to capture TCP packets, it is clearly showing: time,
source IP, destination IP, Protocol, length of packets and information.
As I had told above if you are aware of OSI model then you can see
it has shown three layers of OSI: layer 2 (Ethernet), layer 3 (Internet
Protocol version 4), layer 4 (Transmission Control
Protocol (TCP)).
Now
let’s analysis layer 4 and compare above theory with given below image. You can
see I have underline all fields of TCP segment. Now read following information
of TCP packets.
Source
Port: 51574
Destination
Port: 80
Sequence
number: 0
Acknowledgment
number: 0
Flags: SYN
Window
size value: 29200
Checksum:
unverified
Urgent
Pointer: 0
Option:
20 bytes
The SYN (synchronize) flag is
the TCP packet flag which is set to start a TCP connection for “3 way
handshakes” and the Sequence number and Acknowledgment number are 0.
From
given below image you can see expanded field for flags is showing only 1 flag SYN
is set between source port and Destination port rest flags are not set at this
moment. Hence the control bits will get 1 for
that sets flag in TCP connection otherwise it remains zero.
Packets
setting the SYN flag can also be used to perform a SYN flood and
a SYN scan.
As
I had explain above in three way handshakes first client request with SYN flag
after that Server responds to the client request with the SYN and ACK flags
set, and from following information we observe same sequence of packet transferring
between client and server and as well as the Sequence number is 0 &
Acknowledgment number is 1.
Source
Port: 80
Destination
Port: 51574
Sequence
number: 0
Acknowledgment
number: 1
Flags: SYN, ACK
Window
size value: 42408
Checksum:
unverified
Urgent
Pointer: 0
Option:
20 bytes
Since server response through SYN-ACK flag therefore port 80 is now source port with SYN-ACK flag
to the destination port 51547.
From
expanded field of flags you can observe that this time 2 flags SYN and ACK are
set rest are remain unset or say zero and control bit is set 1-1 for both
flag. This is the 2nd step for “3 way
handshake”.
From
following information we found this time the Sequence number &
Acknowledgment number are 1 and Client completes the connection by
sending a packet with the ACK flag set. Now TCP connection has be
established between client and server.
Source
Port: 51574
Destination
Port: 80
Sequence
number: 1
Acknowledgment
number: 1
Flags: ACK
Window
size value: 229
Checksum:
unverified
Urgent
Pointer: 0
Option:
12 bytes
For
sending ACK packets client again use source port 51547 to the server on destination port 80.
From
given below image you can observer that the control bit
is 1 for acknowledgement flag and this is the third
step required for “3 way handshake” between source port and destination port.
Once
TCP 3 ways handshake connection established then data can transfer between
client and server as you can see from last image it has shown 7th layer
for Hypertext
Transfer Protocol also for data transferring.
Source
Port: 51547
Destination
Port: 80
Sequence
number: 1
Acknowledgment
number: 1
Flags: PUSH, ACK
Window
size value: 229
Checksum:
unverified
Urgent
Pointer: 0
Option:
12bytes
The
use of push function and the PUSH flag is to move forward the data
from the sending user to the receiving user. In order to permit applications to
read from and write to this socket at any time, buffers are implemented on both
sides of a TCP connection.
Here
you can observe that control bit set to 1 for PUSH and ACK flag as
a result a new layer get open for data transferring between sender application
and receiver application.
Now
when transfer data packet explored we found http header details like:
Host: google.com
User-Agent: Mozilla/5.0
From given image you can observe that the highlighted text
is showing connection: keep-alive,
which means server is online at present.
In order to terminate the connection
with client, the server sends FIN (finish) packets to the client after establishment of TCP 3-way
handshake and successful transfer of data.
Source
Port: 80
Destination
Port: 51547
Sequence
number: 1
Acknowledgment
number: 1
Flags: FIN, PUSH, ACK
Window
size value: 229
Checksum:
unverified
Urgent
Pointer: 0
From given below image you can you can see this time the control bit is set 1 for ACK, PUSH and FIN flag and acknowledgment number is 709 for this packages.
Hence this will close the connection for data transfer
between client and server. From given image you can observe that this time it
is showing, connection: close
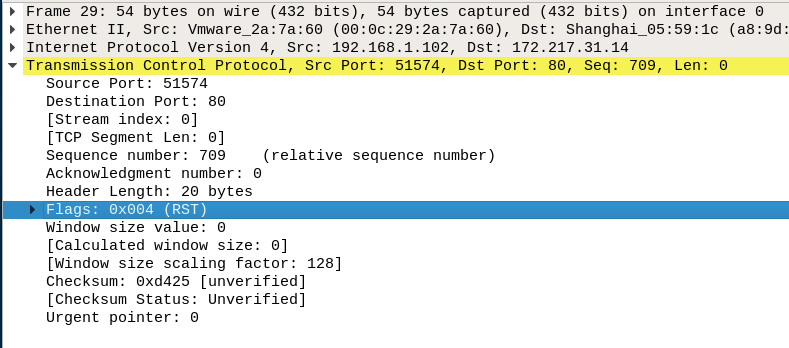
A RST (reset) packet is launched either
in the mid of the 3-way handshake after the server discards the connection or
is unavailable OR in the mid of data transfer when either the server or client
becomes unavailable or discards further communication lacking the formal
4-way TCP connection termination process.
After this client again
try to establish 3–way handshake connection with server.
Source
Port: 51547
Destination
Port: 80
Sequence
number: 1
Acknowledgment
number: 1
Flags: RST
Window
size value: 229
Checksum:
unverified
Urgent
Pointer: 0
In last image you can observe that this control bit is set 1 for
RST flag between source port 51547 and destination port 80.























0 comments:
Post a Comment