in this article you will
learn Cross-site request forgery attack.
For CSRF tutorial I have targeted DVWA and try to bypass low security level.
Cross-site request forgery, also known as one-click attack or session riding and abbreviated as CSRF (sometimes pronounced sea-surf) or XSRF, is a type of
malicious exploit of a website where unauthorized
commands are transmitted from a user that the website trusts. Unlike cross-site scripting (XSS), which exploits
the trust a user has for a particular site, CSRF exploits the trust that a site
has in a user's browser.
An
attacker may forge a request to log the victim into a target website using the
attacker's credentials; this is known as login CSRF. Login CSRF makes
various novel attacks possible; for instance, an attacker can later log into
the site with his legitimate credentials and view private information.
Reference:
en.wikipedia.org/wiki/Cross-site_request_forgery
Let’s start!!!
By default the credential
set for DVWA is admin: password. As
you can see I have used them for login in DVWA.
Now set security
level at low and select the bug
cross site request forgery as current vulnerability. Here you see the text fields are given for
changing the password of the database for user admin.
Then
paste above copied HTML code inside a text file. If you are aware of HTML coding then it will
be very to understand the following syntax inside the notepad which will create
a form to reset the password of a web page. Now save the file as csrf.html
Now
when you will open the csrf.html file it will look like the given below image
where it contains the text field for password and a submit button.
Now
again open csrf.html with notepad to
edit the value inside the text field given for new password and confirm
password. In following screenshot you can see I have given value= “hacker” as new password and confirm password. Then again save it with csrf.html
Now
when again you will open csrf.html file you will find that the blank text field
are given for password is get filled.
Now
when you will click on change button
the password will reset for that web page. This is all about how html form will
work and from given screenshot you can read the sent GET request for changing
password through URL.
Now
copy the URL as shown in the following image.
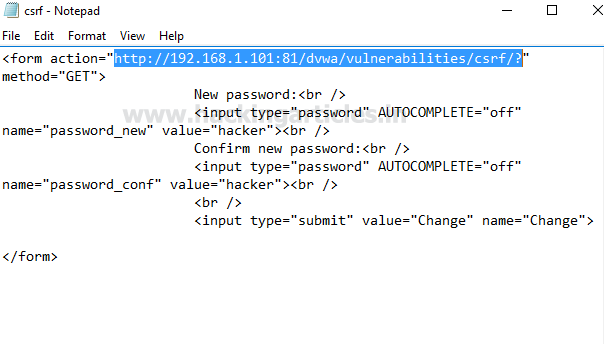
Again open csrf.html with notepad and replace # from above copied URL
which will directly change the password of targeted location for user admin.
Here
you can read the final syntax for html form to change the password for admin
inside DVWA without his involvement. Now
send this crsf.html file to victim
using social engineering or phishing technique to trap the victim for exploiting
with CSRF attack.
New password:
Confirm new password:
When victim will open the csrf.html file and click on change
button the password will get changed for admin inside DVWA.
From
screenshot you can see without admin permission we have successfully changed
his password.
Now
let’s verify, as we know the previous credential was admin: password; here when I try to use them it shows the login
failed.
Further
when I try with admin: hacker as
current credential, I login successfully inside DVWA. This was all about CSRF
tutorial to bypass low security in DVWA.
























0 comments:
Post a Comment