A SQL injection attack consists of insertion or "injection" of a SQL query via
the input data from the client to the application. A successful SQL injection
exploit can read sensitive data from the database, modify database data
(Insert/Update/Delete), execute administration operations on the database (such
as shutdown the DBMS), recover the content of a given file present on the DBMS
file system and in some cases issue commands to the operating system. SQL
injection attacks are a type of injection
attack, in
which SQL commands are injected into data-plane input in order to effect the
execution of predefined SQL commands.
Requirement:
Xampp/Wamp Server
DVWA Lab
Kali Linux: Burp suite,
sqlmap tool
Very
first you need to install DVWA lab in your XAMPP or WAMP server, read full
article from here
Now
open the DVWA in your pc and login with following credentials:
Username – admin
Password – password
Bypass Low Level Security
Click on DVWA Security and set Website Security Level low
From
the list of vulnerability select SQL Injection for your attack. Type user ID: 1 in text box. Don’t click on submit button without setting
browser proxy. Set your browser proxy to make burp suite work properly.
Turn
on burp suite in kali Linux click on proxy
in menu bar and go for intercept is
on button. Come to back and click on submit button in browser. The Intercept button is used to display HTTP and Web
Sockets messages that pass between your browser and web servers. Copy the complete detail of intercept; past on leafpad; save on desktop as 1.
Open terminal and type following command for SQL
injection attack using Sqlmap.
sqlmap -r
/root/Desktop/1 --dbs -D dvwa --dump all --os-shell
sqlmap is
an open source penetration testing tool that self-regulates the process of
detecting and exploiting SQL injection vulnerabilities
and taking over of database servers. -r is used for recursions which will
analysis your intercepted data from path/root/Desktop/1.
Things
that to be notice is I have used –dbs
in above command which fetched all database
names as you can see in below image. Then it will ask to store hashes in
temporary file type y and hit enter.
Now
next it extracts table: user for database DVWA which I have mentioned in
above command as –D dvwa.
Grateful
we have penetrated the user table successfully. Please have a look over fetched
data you will find that it dumps
login-ID for user; fail login; user first name; user last name; hash password.
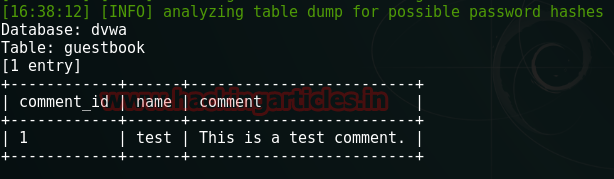
Table: guestbook
for database DVWA which having only
1 entry.
Now this tool is going to use a web backdoor for command
prompt where it will ask to choose language for backdoor
Type 4 and hit enter.
Afterwards it will ask to choose any options for location
for writable directory.
Type 1 and hit enter.
You can see the backdoor has been successfully uploaded
on destination folder. Type y for
retrieved the command standard output. Now I am inside the os-shell which I
have mentioned in above command as os-shell.
Os-shell> net
users
Bypass Medium Level Security
Click on DVWA Security and set Website Security Level Medium
From
the list of vulnerability select SQL Injection for your attack. Select user ID: 2 from list. Set proxy turn on
intercept tab in burp suite and come back to web browser for submit.
Follow
the same process save the selected detail fetched by intercept on the desktop
as file: 2.
Now
security level is increased so I was unable to get os-shell but successful
received all detail of database by typing following command on terminal.
sqlmap -r
/root/Desktop/2 --dbs -D dvwa --dump all
Again
I have got all database names
including dvwa. Now again type y for further process.
Table: user
for database DVWA It has dumped
again same login-ID for user; fail
login; user first name; user last name; hash password.
Table: guestbook
for database DVWA which having only
1 entry.
Bypass High Level Security
Click on DVWA Security and set Website Security Level High
This
is very similar to the low level, however this time the attacker is inputting
the value in a different manner. The input values are being transferred to the
vulnerable query via session variables using another page, rather than a direct
GET request.
Here
you find different scenario when you will select SQL Injection don’t get panic
follow the step carefully this level is as similar as low level security. For
hint the developer told that he had redirect the submit user ID to another page
through POST action.
Click on link here to change your ID which will
redirect to new window type ID: 1
turn on intercept then comes back
and clicks on submit.
Now
compare the intercepted data of both levels high and low you will find that POST action is use in high security as
well as GET action is used in low
security level. Copy the complete data and make following change in it. For
help please look at below images.
Past
the copied data to a leafpad replace POST from GET and add /?id=1&Submit=Submit
save your file:third on desktop.
GET
/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit HTTP/1.1
Here go with flow!!!
Same
process as above and this time again I will try for os-shell.
sqlmap -r
/root/Desktop/1 --dbs -D dvwa --dump all --os-shell
Again I have got all database
names including dvwa. Now again
type y for further process.
Table: user
for database DVWA It has dumped
again same login-ID for user; fail
login; user first name; user last name; hash password.
Table: guestbook
for database DVWA which having only
1 entry.
Oops!! Fail to get os-shell
but we have retrieve database of dvwa under high security.